Cherlynn Cha
In today’s interconnected world, cyberthreats are everywhere, and they’re always changing. Startups can’t afford to ignore the importance of securing their digital infrastructure. Waiting until a security breach happens can lead to severe consequences, such as financial losses and reputational damage.
Recently, ExpressVPN collaborated with Linking Help, the NGO behind UA.SUPPORT that provides pro bono legal support to Ukrainian refugees, to conduct a threat modeling analysis. The objective was to identify security concerns and provide effective mitigation measures. Inspired by this experience, I want to share our methodology with the wider community and empower you to enhance your security posture — even with limited resources and other business pressures.
Unmasking exploits with threat modeling
Threat modeling is a key practice for strengthening digital defenses. Simply put, it involves understanding and knowing your organization, so others can’t cause you harm. The goal is to raise awareness of security gaps and minimize the risk of potential exploits by systematically analyzing potential avenues for abuse.
Various threat modeling standards and frameworks exist, and the right choice for you depends on your specific context. Instead of telling you which of these to use, we will focus on the underlying methodology that we used to conduct threat modeling for UA.SUPPORT, thereby generating efficient and practical security recommendations.
Actionable security strategies for startup resilience
1. Know thy enemy
Identifying potential adversaries and their objectives is crucial for assessing why and how you may be targeted. For instance, cybercriminals often target systems that handle credit cards or personal identifiable information (PII), while nation-state adversaries may be interested in information for espionage or intelligence purposes.
In the case of UA.SUPPORT, potential adversaries included:
- Advanced adversaries, who have the following objectives:
○ Gathering intelligence on individuals from Ukraine.
○ Compromising systems to gain unauthorized access, gather sensitive information, or conduct espionage activities.
○ Disrupting the organization’s platform to hinder its ability to assist vulnerable individuals.
- Opportunistic cybercriminals, who aim to:
○ Exploit the PII of refugees for monetary gain.
○ Engage in unauthorized cryptocurrency mining or launch ransomware attacks
○ Utilize the organization’s infrastructure to distribute malware to unsuspecting users.
Once we identify who the potential adversaries are, we can look at what they perceive as “crown jewels.” We can then use this to start breaking down why they might target you, and how they would go about doing it.
2. Know thyself
To figure out how threats might manifest themselves within your environment, you must first gain a clear understanding of your environment.
The best way to achieve this is by engaging with the resident experts who developed or manage the systems, components, and processes you use. Their expertise can provide valuable insights into the inner workings of systems as well as the flow and exchange of data. This process helps create an inventory and blueprint that captures the intricate web of business and technological interactions at play.
In our engagement, key areas we reviewed included:
- Refugee-legal support interactions.
- Information transfer mechanisms.
- Perimeter systems and their connections.
- Employees and volunteer access privileges.
- “Know your customer” programs.
- Employee interactions with IT systems.
- Overall system configuration, security, and hosting.
Examining these provides insights into potential vulnerabilities that adversaries could exploit.
3. Anticipate weak points
Adversaries have various methods to gain access to systems, and by formulating detailed, hypothesis-driven questions, we can pinpoint potential weak points that adversaries may exploit.
In the case of UA.SUPPORT, it is crucial to analyze the direct interaction between refugees and legal volunteers. This analysis involves focusing on the following areas:
- CRM systems.
- Databases for transaction management.
- Workstations with sensitive files.
- Front-facing websites for information submission.
- Servers hosting the website.
- Other locations where data is processed or stored.
By expanding our examination and going into granular specifics, we gain a deeper understanding of how adversaries might navigate each system in their pursuit of compromise.
4. Step into the adversary’s shoes
To effectively address potential vulnerabilities, consider the paths of least resistance that adversaries may exploit. Startups like you have an advantage in this regard, as you are likely to possess intimate knowledge of your systems because of your size. This knowledge enables you to conduct an in-depth analysis of potential risks and weaknesses.
For example, if the concern is customer credit card theft, startups can ask specific questions during threat modeling. Some of these questions may include:
- How are credit cards processed for customer transactions across our systems?
- Which system handles the submission of credit card information?
- Do these systems solely process payments, or do they interact with other systems for storage or operations?
- How are these systems built and structured?
- Who has access to them, and what measures are in place for backups?
- Are there any third-party payment service providers in use, and how are they integrated into our ecosystem?
Visualizing potential attack scenarios using tools like an attack tree diagram can also be helpful. This approach allows you to map out the progression an adversary might make from one compromised point to another in pursuit of their end goal. For instance, compromising a developer’s workstation could provide access to secrets and credentials, which could then be used to target the CI/CD pipeline, cloud infrastructure, production systems, or even backup systems. Subsequently, the attacker could pivot from a compromised backup server to the associated database, ultimately gaining access to coveted credit card information.
The attack tree diagram for such an attack may look something like this:
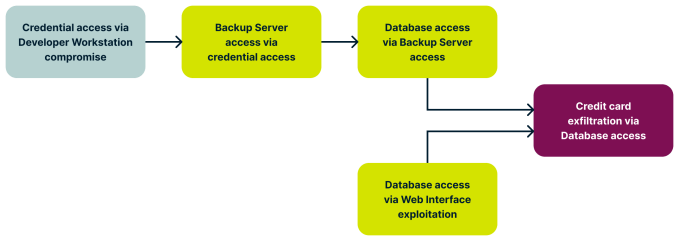
Of course, real-world systems are more complex than that, and you may end up with an attack tree that may have multiple branches and levels:
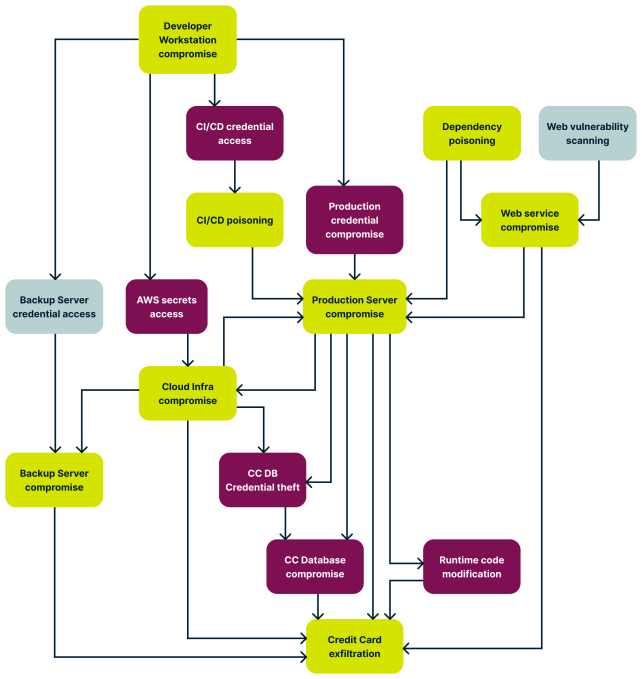
By understanding the system landscape and obtaining answers to these questions, you can visualize how attackers might chain actions to progress toward their objectives.
5. Put an evilness score on it
To prioritize efforts to address security risks, use a scoring system to assign threat scores. This allows for a quick evaluation of how critical each step is in a potential attack. Several parameters can be considered when assigning these scores:
- Severity: The extent of compromise or harm that could be caused by an attack (ranging from 0 [Not Severe] to 5 [Highly Severe]).
- Impact: This effect or consequence of an attack on your day-to-day operations and overall business (ranging from 0 [No Impact] to 5 [High Impact]).
- Likelihood: The probability for an attack to occur (ranging from 0 [Unlikely] to 5 [Highly Likely]).
- Capabilities: The skills and tools required, and the level of difficulty faced if an adversary attempts to execute the action (ranging from 0 [High Capabilities] to 5 [No Capabilities]).
By summing up the scores for each step, you can better understand the potential risks you face, and prioritize mitigation efforts based on the highest-scoring threats. This approach ensures that resources are allocated to the most critical areas first.
After adding up these scores, this sample scale can be used to evaluate overall risk:

Implement proactive security measures
Once potential vulnerabilities and high-priority threats are identified, take proactive steps to address them. This includes implementing security controls and countermeasures to mitigate the identified risks.
Accept, mitigate, or transfer
Based on the threat scores, determine whether to accept the risks, mitigate them by implementing additional safeguards, or transfer them by leveraging third-party vendors or solutions.
Common proactive security measures include:
- Implementing two-factor authentication for user accounts to prevent unauthorized access.
- Keeping software and systems up-to-date to address known vulnerabilities.
- Conducting regular training for employees and volunteers to educate them about security threats and best practices.
- Implementing secure coding practices to prevent common vulnerabilities like injection attacks and cross-site scripting (XSS).
- Using encryption to protect sensitive data.
- Implementing intrusion detection and prevention systems (IDPS) to monitor and block malicious activities.
Update scores
As you implement security protections, it is important to update your threat scores accordingly. This will help you reassess the effectiveness of your newly implemented security protections by reflecting the likelihood of threats occurring.
Continuously monitor and adapt
Threat modeling and proactive security measures are not one-time activities. You should regularly review and update your threat models as the business and threat landscape evolves. Additionally, it’s essential to foster a culture of security awareness and accountability throughout the organization by encouraging employees and volunteers to promptly report any security concerns or incidents.
The value of proactive cybersecurity strategies
Cybersecurity is a complex and multifaceted field, and even with thorough threat modeling, there’s always a risk of compromise. Nevertheless, each proactive step we take to secure our systems makes it more difficult for adversaries to compromise us.
The goal isn’t necessarily to be the fastest sprinter. Instead, our focus is on outrunning others being targeted and staying one step ahead. By investing time and effort into proactive cybersecurity strategies, we elevate our overall security posture, increasing our chances of staying ahead and protecting our digital assets effectively.



























Comment