In what Edward Snowden deems “not unprecedented,” hackers calling themselves the Shadow Brokers have collected NSA-created malware from a staging server run by the
Equation Group, an internal hacking team. The Shadow Brokers published two chunks of data, one “open” chunk and another encrypted file containing the “best files” that they will sell for at least $1 million. Wikileaks has said they already own the “auction” files and will publish them in “due course.”
They’ve also released images of the file tree containing a script kiddie-like trove of exploits ostensibly created and used by the NSA as well as a page calling out cyber warriors and “Wealthy Elites.” The page also contains links to the two files, both encrypted. You can
grab them using BitTorrent here.
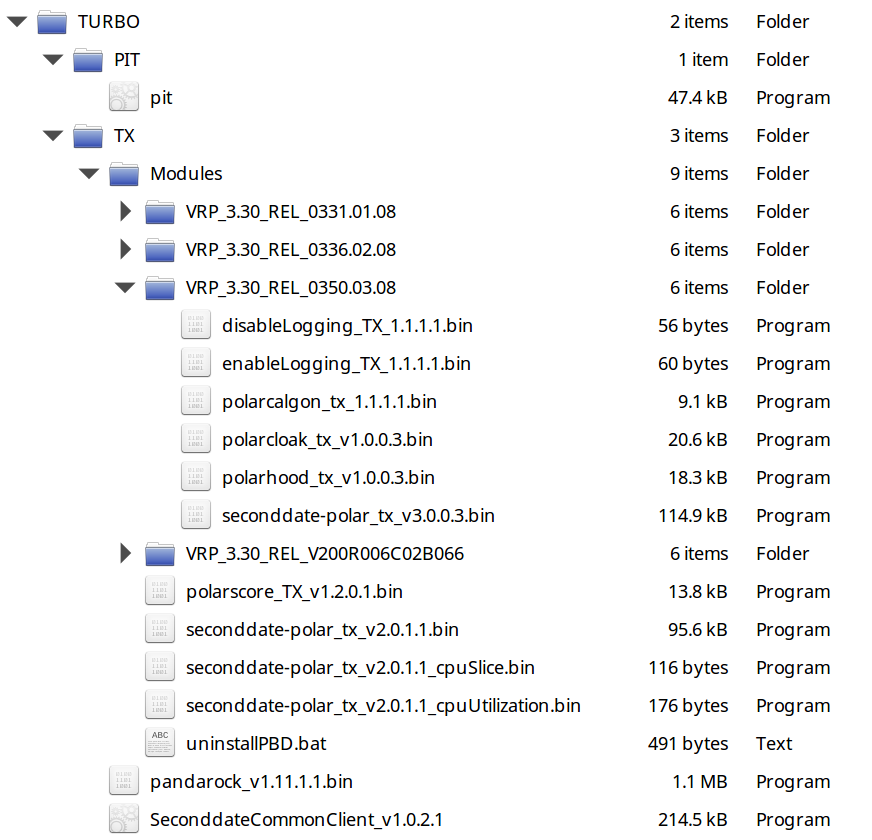

The “free” file contains many staging programs designed to inject malware into various servers. From my cursory inspection the files look to be more functional than damaging and show NSA hackers how to quickly deploy their tools and then close infiltrations without a trace. It is yet unclear how these files can be used to damage networked computers although I’m sure there is something of value in the trove.
The Shadow Brokers wrote:
Snowden suggests that the hackers were Russian although the simplistic grammar above could be a cover.
What Does It Mean?
First, we need to understand what these files are and what they do. These are hacking tools including RATs – or remote access Trojans – and exploits designed to attack web and file servers. The “free” files are all dated from the Summer of 2013 which suggests they aren’t completely up to date and they contain fairly innocuous-looking tools with ominous names like “eligiblebombshell” and “escalateplowman.” Most of these are human-readable and written in Python or shell script although there are some compiled binaries.
Some of the files – BANANAGLEE, for example – appeared in the leaked Snowden files which suggests the files are real and sourced from the NSA’s own servers. Without training, however, it is not clear if any of the files are particularly dangerous on their own.
These are, however, the files that an NSA agent would use if they were trying to hack your server. While a folder of files isn’t as exciting as, say, a whirring, clicking magic hacking machine we’d see in the movies, this is the stuff an agent would download, use, and delete when trying to take control of a server. Snowden suggests that all of these files were on a staging server somewhere within the Equation Group servers and by admitting they scoured the Group’s “source range” we learn that the Shadow Brokers found one Equation Group server and methodically tried IP addresses in that range.
The hackers have received a little over a bitcoin in their online wallet and no one has come forward to pay for the “best files.”
As for the auction the Equation Group will release the files to the highest bidder and they promise the files are “better than stuxnet,” a virus used to slow down Iran’s nuclear enrichment programs. They wrote:
Don’t Panic
The hack of an NSA malware staging server is not unprecedented, but the publication of the take is. Here's what you need to know: (1/x)
— Edward Snowden (@Snowden) August 16, 2016
The files don’t appear to contain any identifying data nor do they clearly point to any single agent in the field. Owning these files on your computer, however, could suggest to a foreign power that you are part of the NSA’s nefarious schemes, a slight concern when crossing borders.
This isn’t a damaging leak, per se. It is a dump of tools used by NSA agents in the field, akin to the image of the TSA master keys used to create 3D printed copies. It’s an embarrassing breach and should have never happened.
This is not new data, either. The hacker seems to have been ejected from the server in June 2013 and unless the auction files contain newer exploits, most of these tools are probably neutered or out of date. Barring some serious file intrusion on an operative’s computer these files cannot identify any single agent or part of the agency. Finding these files is like finding a toolbox on the side of the road. You can figure out if the owner was a carpenter or a plumber based on the tools inside but, without further information, you can’t identify the owner herself.
OK, Panic
The fact that any of this was found is a black eye for the NSA. While Snowden rightly notes that the agency is not made of magic, leaving an entire staging server up, even in the benighted summer of 2013, is a foolish and reckless move. Now that these files are public state actors can easily pin a certain type of attack on the NSA. “This leak is likely a warning that someone can prove US responsibility for any attacks that originated from this malware server,” wrote Snowden. Further, it shows that the NSA is sloppy, something that anyone with a passing knowledge of government IT would understand.
For example, one script recommends that users copy an exploit in place of the common sendmail program.
put /current/bin/FW/DurableNapkin/durablenapkin.solaris.2.0.1.1 sendmail -> put the tool up as "sendmail"
The NSA hackers go on to describe the close-out commands to be used to shut things down, culminating in the lines:
# Now type GO to send 1 packet or type GO 25 to send 25 packets.. whatever
GO
When finished completely
DONE
Don't forget to remove your binary from target
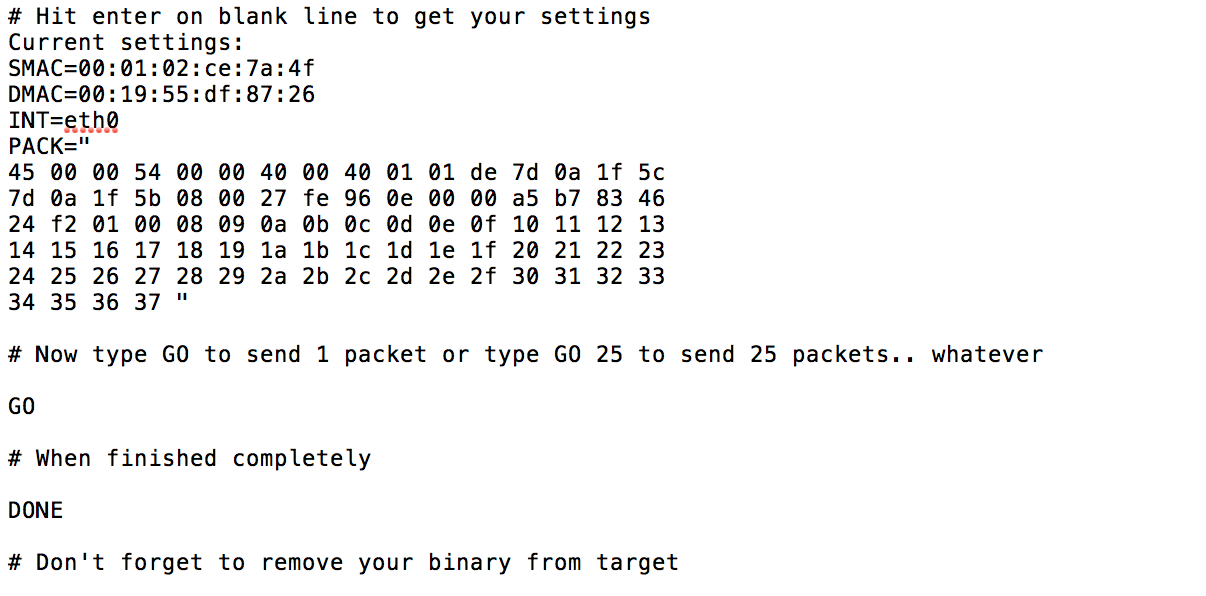
Considering I read those lines on my insecure MacBook on a beautiful August morning in 2016 it’s clear that someone, somewhere, screwed up. Given that there is an entire file containing further exploits we’re led to wonder where else they slipped.































Comment