There was a good post on ZDNet recently talking about how a market has developed for the bulk-purchasing of Gmail, Hotmail and Yahoo email accounts (amongst others). The market rate seems to be around $10 for every thousand accounts, with discounts applied with larger orders of 100,000 accounts or more.
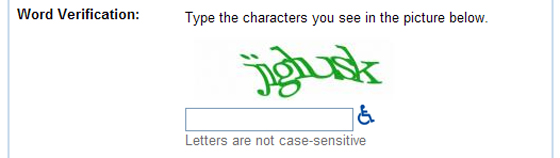
The most popular security mechanism for protecting against accounts being automatically created is a CAPTCHA (Completely Automated Public Turing Test to Tell Computers and Humans Apart), where the user is presented a challenge image with a number of letters or words that they must fill out. To deter automated attacks against CAPTCHA protection, the letters and numbers used are often distorted so that image recognition algorithms would not be able to easily decipher it, but while a human reasonably could. The weakness in CAPTCHA is that with each letter or character, the correct response is one of ten numbers or 25 letters – so even with distortions applied and various different colors or additional lines the latest attacks can achieve success rates of between 60-99% (depending on the CAPTCHA style used).
Because the account creation process is automated, with even a success rate as low as 10% hundreds of accounts can be created per minute. The reason why Gmail, Yahoo Mail and Hotmail email accounts are a popular target is because there is an implicit trust of emails being sent from those domains in many spam filtering solutions. That implicit trust is based on the service’s ability to filter out fake or spam users, which relies mostly on the CAPTCHA. So without the CAPTCHA security, the trust mechanism is broken to the detriment of all users of those systems as well as external email systems that trust email from those domains in some way more than others.
The second common method for breaking CAPTCHAs is for the attacker to take the challenge image and present it to an unaware user on an unrelated site that the attacker controls. For instance, the attacker may control a large network of pornography or other video related websites where the visitor would be prompted with a challenge CAPTCHA to view a video or to access content. The user is not aware that the challenge they are responding to is actually assisting the attacker in registering a new account at another service – and that the image is simply being proxied through to them. Once the user enters their response, the attacking service would then relay the request along with the account registration details back to the original service. With large-scale web traffic to such sites, and with users being challenged with an image on each video or content view, the attacker can rapidly register a large number of accounts depending on traffic levels.
The techniques for breaking CAPTCHAs have advanced to the point of being able to create thousands of accounts automatically and rapidly, and an entire market for the sale of these email accounts has been created. The knowledge on breaking CAPTCHAs need not be distributed broadly – but only needs to lie with those with the incentive to break and sell accounts. With the system broken once, the flood gates are open while CAPTCHAs reach a limit in terms of how far they can be obfuscated because real humans would then have problems deciphering them. The CAPTCHA solutions currently seen on these popular email services is probably as far as you could blend or distort the image without creating accessibility issues that outweigh the security gains (and those gains are quickly approaching zero).
CAPTCHAs as a human filter have always been controversial, as they are not accessible to the blind and create a friction point in new user registration (I have given up on a registration process many times because I simply couldn’t get the CAPTCHA response right). With the large-scale cracking of accounts that rely on CAPTCHAs, a healthy market for cheap accounts as well as the complexity of CAPTCHAs now reaching their limits of usability, it might finally almost be time to bid farewell to a security solution that has never been popular and was only effective for a very short period of time.


























Comment