Andre Durand
Editor’s note: Andre Durand is the founder and CEO of Ping Identity.
Where is your data, and how quickly can you safely reach it?
These questions are top of mind now that cloud and mobile apps like Dropbox, Google Apps and iCloud, as well as mobile banking apps pervade our everyday lives at home and at work. By 2020, there will be an estimated 6.5 connected devices per person. And as more devices — from baby monitors to cars and pacemakers — get Internet connections, there’s an even bigger question: How easily can hackers access devices and sensitive information?
We’re all concerned about protecting our personal data as our lives becomes more visible online every day. For CIOs and enterprise IT teams, the stakes are just as high given concerns over protecting company, partner and customer data and corporate devices. Consider these scenarios:
Executives traveling to foreign countries are accessing internal systems via unsafe networks. Employees are using mobile devices to log into corporate assets in the cloud and sharing sensitive information through email, cloud storage services and websites. Often, they are not following, or even aware of, official IT security policies. Hackers are bypassing traditional perimeter security and firewalls altogether by compromising weak and stolen passwords to take sensitive personal data right off the network.
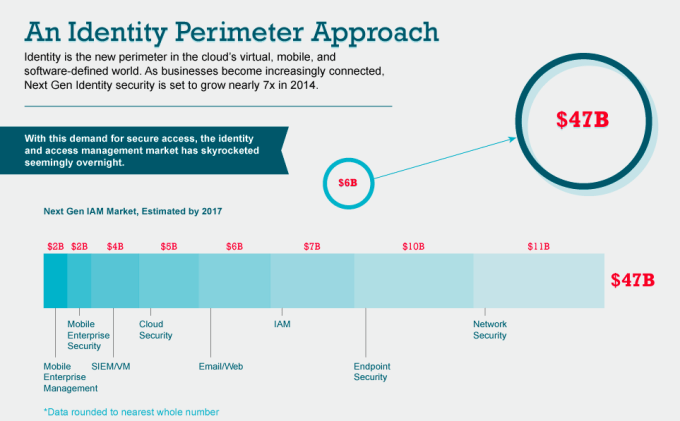
These realities cost companies money — a lot of it. The average cost of a data breach in 2013 was $3.5 million, 15 percent higher than the previous year. Hacking costs the overall U.S. economy as much as $100 billion and 500,000 jobs each year. Despite the fact that hackers are getting in, spending continues on legacy security software mostly unfit to thwart the bad guys. By 2017, nearly $50 billion will be spent on security solutions, from antivirus software and network security to mobile and cloud security.
Much of the IT security industry exists today because we didn’t get identity right at a network level 30 years ago. But many of the tenants of our security model built around the notion that we put known, controlled and trusted users, devices and applications all in one place and surround them with a firewall no longer exist in a world of cloud and mobile.
According to a study conducted by the Ponemon Institute, 57 percent of security professionals say their organizations aren’t protected against advanced attacks, and 63 percent don’t think they can stop confidential information leaks. Many have taken a posture of simply assuming their perimeter has been breached. Now what?
Eliminating the Password
One of the weakest links in our battle against cybercriminals is the password. Lacking a strong, consistent and universal method of identifying ourselves to the Internet, every application and device has been forced to ask us who we are via username and password. This redundant, wasteful but ultimately flawed reality has resulted in hundreds of millions of weak and easily stolen entryways into our networks, applications and data.
Even the father of the computer password, MIT Professor Emeritus Fernando Corbató, admits that the model is flawed because strong passwords are hard to remember. As a result, most people simply re-use the same password on multiple accounts, which makes it easy for hackers to do even more damage. According to the Verizon 2013 Network Investigations Data Breach Report, 76 percent of network intrusions exploit weak or stolen credentials. And the financial losses are whopping. Forrester Research says the online services industry is seeing more than $200 billion in annual losses from password breaches.
Let’s pause for a moment and do the math. The nearly $50 billion invested in IT security products each year is still costing companies $200 billion in password-related losses every year. These numbers tell a clear story: Legacy IT security and identity access management approaches are failing. But is killing the password really a viable solution?
There are a number of technologies that promise to kill the password — biometrics like the fingerprint authorization popularized by the new iPhone, USB security tokens, Trusted Platform Modules (TPMs), embedded secure elements (eSEs) and smart cards. But so far none has been able to save the day. Why? Because we haven’t yet networked identity across the Internet and, therefore, have no way to leverage one strong identification and authentication system to access all our systems — from networks, to Internet services providers, to mobile devices and cloud apps. Identity needs to become the centerpiece of security, not a one-off add-on.
It may seem like an impossible task to eliminate something that permeates our everyday lives and is firmly rooted in our basic behavior through years of conditioning. However, there are companies that see identity as the future. They are re-allocating budgets from traditional security to identity because they realize identity not only offers greater security, but can also transform the way a business is run in today’s modern environments. They recognize the perimeter no longer stops at the firewall, but extends to the cloud and every end-user device that is used to access their applications, including laptop, tablet and mobile phone.
Who are these forward-thinking companies? A top five U.S. bank is making great strides in reducing reliance on passwords alone. You still have a log-in with a traditional username and password, but once you’re in the system you have access to dozens of programs within the company’s federated network. There are no redirects or multiple log-ins needed.
For instance, when you order new checks, an integrated solutions payment provider handles the order without requiring a second log-in. If you use the online investment tool, you are routed through a different service, but you never leave the bank’s site. To participate in the cash back rewards program, different program partners are involved in enabling you to take advantage of deals from hundreds of retailers. When you “go paperless” and receive eBills, you’re never taken off the bank’s site to access account information from different vendors.
Identity is the key throughout all of this, serving as the universal connector to all of the services and features regardless of the provider offering them. Within the enterprise, identity gives employees and suppliers the ability to traverse the applications relevant to their roles. If companies can guarantee the identity of a user, then they can offer them access to dozens, even hundreds, of services and without multiple sign-ins and sign-outs.
Imagine the improvements in productivity when the right people can have access to the information they need — and only the information they need — based on their unique roles. In that scenario, enterprises can securely integrate with all their partners and suppliers. This is the modern enterprise that I expect we’ll see become the norm in the not-so-distant future.
With Change Comes Big Opportunity
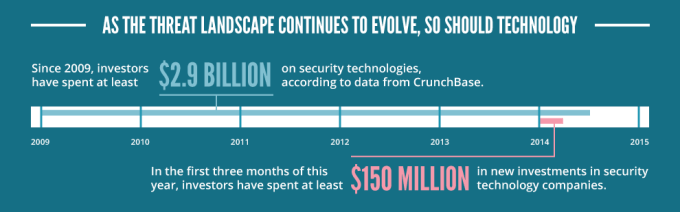
With the emergence of cloud and mobility, we’re seeing a shift in spend within the security industry. Investors are catching on to the market opportunity to retool and secure the modern enterprise. Since 2009, over $2.9 billion has been invested in security technology companies that have distinct and unique approaches to security. In the first three months of 2014 alone, over $150 million has been invested in 26 new companies in the security space.
The challenge and opportunity going forward will be to establish a framework for trusting users, devices and applications, and connecting them securely. And this is where identity and security become one and the same. Identity is the new perimeter.



























Comment