hacking
A top European privacy watchdog is investigating following the recent breaches of Dell customers’ personal information, TechCrunch has learned. Ireland’s Data Protection Commission (DPC) deputy commissioner Graham Doyle confirmed to…
The FBI along with a coalition of international law enforcement agencies seized the notorious cybercrime forum BreachForums on Wednesday. For years, BreachForums has been a popular English-language forum for hackers…
The person who claimed to have stolen the physical addresses of 49 million Dell customers appears to have taken more data from a different Dell portal, TechCrunch has learned. The…
Threat actor says he scraped 49M Dell customer addresses before the company found out
The person who claims to have 49 million Dell customer records told TechCrunch that he brute-forced an online company portal and scraped customer data, including physical addresses, directly from Dell’s…
Technology giant Dell notified customers on Thursday that it experienced a data breach involving customers’ names and physical addresses. In an email seen by TechCrunch and shared by several people…
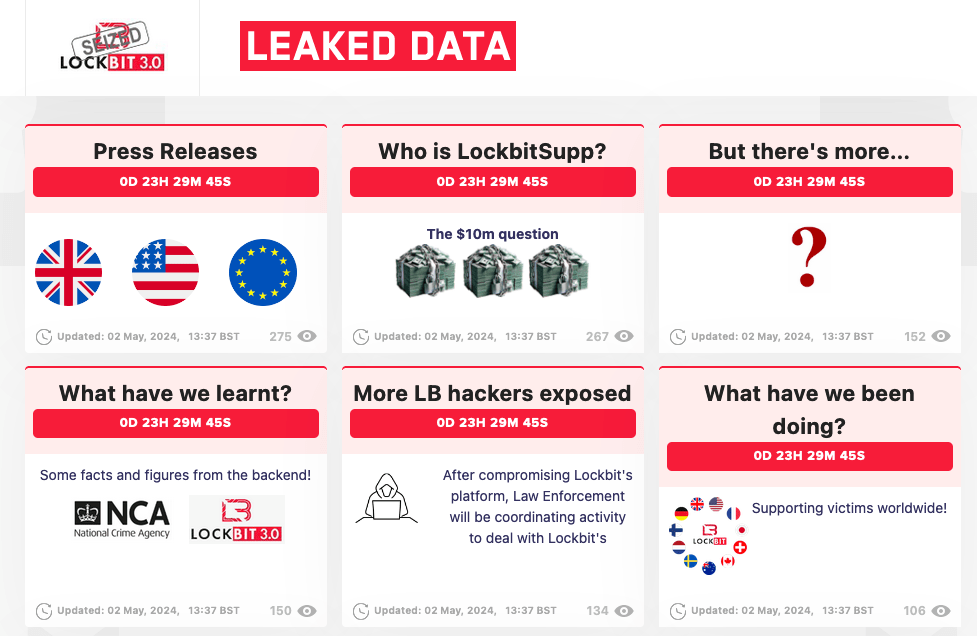
An international coalition of police agencies have resurrected the dark web site of the notorious LockBit ransomware gang, which they had seized earlier this year, teasing new revelations about the…
Apex Legends hacker says game developers patched exploit used on streamers
Last month, a hacker wreaked havoc during an esports tournament of the popular shooter game Apex Legends, hacking two well-known streamers mid-game to make it look like they were using…
Shakeeb Ahmed, a cybersecurity engineer convicted of stealing around $12 million in crypto, was sentenced on Friday to three years in prison. In a press release, the U.S. Attorney for…
Featured Article
How Ukraine’s cyber police fights back against Russia’s hackers
On February 24, 2022, Russian forces invaded Ukraine. Since then, life in the country has changed for everyone. For the Ukrainian forces who had to defend their country, for the regular citizens who had to withstand invading forces and constant shelling, and for the Cyberpolice of Ukraine, which had to shift its focus and priorities.…
Ransomware gangs are increasingly calling up victim organizations to extort and intimidate rank-and-file employees.
Hackers stole 340,000 Social Security numbers from government consulting firm
U.S. consulting firm Greylock McKinnon Associates (GMA) disclosed a data breach in which hackers stole as many as 341,650 Social Security numbers. The data breach was disclosed on Friday on…
Activision investigating password-stealing malware targeting game players
Video game giant Activision is investigating a hacking campaign that’s targeting players with the goal of stealing their credentials, TechCrunch has learned. At this point, the hackers’ specific goals —…
Featured Article
Investors’ pledge to fight spyware undercut by past investments in US malware maker
On Monday, the Biden administration announced that six new countries had joined an international coalition to fight the proliferation of commercial spyware, sold by companies such as NSO Group or Intellexa. Now, some investors have announced that they too are committed to fighting spyware. But at least one of those investors, Paladin Capital Group, has…
On Sunday, the world of video games was shaken by a hacking and cheating scandal. During a competitive esports tournament of Apex Legends, a free-to-play shooter video game played by…
The Pokémon Company said it detected hacking attempts against some of its users and reset those user account passwords. Last week, an alert was visible on Pokémon’s official support website…
Featured Article
Four things we learned when US intelligence chiefs testified to Congress
Cyberattacks, regional conflict, weapons of mass destruction, terrorism, commercial spyware, AI, misinformation, disinformation, deepfakes and TikTok. These are just some of the top perceived threats that the United States faces, according to the U.S. government’s intelligence agency’s latest global risk assessment. The unclassified report published Monday — sanitized for public release — gave a frank…
Russian spies keep hacking into Microsoft in ‘ongoing attack,’ company says
On Friday, Microsoft said Russian government hackers continue to break into its systems using information obtained during a hack last year. This time, the Russian hackers dubbed Midnight Blizzard have…
Researchers say easy-to-exploit security bugs in ConnectWise remote-access software now under mass attack
Security researchers say a pair of easy-to-exploit flaws in a popular remote-access tool used by more than a million companies around the world are now being mass exploited, with hackers…
Featured Article
Researchers warn high-risk ConnectWise flaw under attack is ’embarrassingly easy’ to exploit
Security experts are warning that a high-risk vulnerability in a widely used remote access tool is “trivial and embarrassingly easy” to exploit, as the software’s developer confirms malicious hackers are actively exploiting the flaw. The maximum severity-rated vulnerability affects ConnectWise ScreenConnect (formerly ConnectWise Control), a popular remote access software that allows managed IT providers and…
Researchers say attackers are mass-exploiting new Ivanti VPN flaw
Hackers have begun mass exploiting a third vulnerability affecting Ivanti’s widely used enterprise VPN appliance, new public data shows. Last week, Ivanti said it had discovered two new security flaws…
Remote access giant AnyDesk resets passwords and revokes certificates after hack
Remote desktop software provider AnyDesk confirmed late Friday that a cyberattack allowed hackers to gain access to the company’s production systems, putting the company in lockdown for almost a week.…
US gives federal agencies 48 hours to disconnect flawed Ivanti VPN tech
U.S. cybersecurity agency CISA has ordered federal agencies to urgently disconnect Ivanti VPN appliances given the risk of malicious exploitation due to multiple software flaws. In an update to an…
Europcar says someone likely used ChatGPT to promote a fake data breach
On Sunday, a user in a well-known hacking forum advertised what they claimed was a cache of stolen data from the rental car giant Europcar. The user claimed to have…
Featured Article
US disrupts China-backed hacking operation amid warning of threat to American infrastructure
The U.S. government announced Wednesday it had disrupted a China-backed hacking operation targeting U.S. critical infrastructure, amid warnings that Beijing is preparing to cause “real-world harm” to Americans in the event of a future conflict. Speaking during a U.S. House of Representatives committee hearing on cyber threats posed by China, FBI director Christopher Wray told…
Ivanti patches two zero-days under attack, but finds another
Ivanti warned on Wednesday that hackers are exploiting another previously undisclosed zero-day vulnerability affecting its widely used corporate VPN appliance. Since early December, Chinese state-backed hackers have been exploiting Ivanti…
Malicious hackers have begun mass-exploiting two critical zero-day vulnerabilities in Ivanti’s widely used corporate VPN appliance. That’s according to cybersecurity company Volexity, which first reported last week that China state-backed…
State-backed hackers are exploiting new Ivanti VPN zero-days — but no patches yet
U.S. software giant Ivanti has confirmed that hackers are exploiting two critical-rated vulnerabilities affecting its widely-used corporate VPN appliance, but said that patches won’t be available until the end of…
23andMe tells victims it’s their fault that their data was breached
Facing more than 30 lawsuits from victims of its massive data breach, 23andMe is now deflecting the blame to the victims themselves in an attempt to absolve itself from any…
For yet another year, hackers stole billions of dollars in crypto. But for the first time since 2020, the trend is downwards, according to crypto security firms. This year, hackers…
Featured Article
These are the cybersecurity stories we were jealous of in 2023
Back in 2018, my former colleague at VICE Motherboard Joseph Cox and I started publishing a list of the best cybersecurity stories that were published elsewhere. It wasn’t just a way to tip our hats at our friendly competitors; by pointing to other publications’ stories, we were giving our readers a fuller picture of what…