A user on the Twitter/X alternative Spoutible claims the company deleted their posts after they pushed Spoutible CEO Christopher Bouzy to be more honest about the nature of its recent security issue. The claims, which the company denies, are the latest bizarre twist in the security incident saga taking place over the past week at the startup.
Last week, Bouzy acknowledged a security vulnerability that he said had exposed users’ emails and phone numbers at his startup, positioned as a more inclusive, kinder Twitter. However, security researcher Troy Hunt, creator of the Have I Been Pwned website, which allows people to check to see if their data was compromised in a data breach, found that Spoutible’s developer API was also exposing information that bad actors could have used to take over users’ accounts without them knowing.
Hunt detailed his findings of that far more serious charge on his website, noting that the Spoutible API returned data including the bcrypt hash of any other user’s password, plus 2FA (two-factor) secrets and the token that could be reused to reset a user’s password.
In short, this vulnerability was highly exploitable and could have allowed a bad actor to take over a user’s account without them knowing, as The Verge reported at the time. Hunt had been alerted to this issue by a third party who claimed they had scraped data from Spoutible’s service. As Have I Been Pwned’s account confirmed on X, Spoutible had 207,000 user records scraped from its misconfigured API including “name, email, username, phone, gender, bcrypt password hash, 2FA secret and password reset token.”
As of last June, Spoutible had 240,000 registered users, so the breach impacted a good chunk of the smaller social network’s user base. (Spoutible declined to share its current user numbers).
The security researcher explained that the vulnerability could have been exploited by bad actors, who would have been able to obtain a hashed version of users’ passwords. Though the passwords were protected via bcrypt, shorter passwords could have been easier to guess and crack. Plus, no email notification would be sent to the account holder about the password change, so they would have never known if their account was no longer under their control, Hunt noted.
This sort of thing would have been an issue for any startup, but particularly one where the user base is full of early adopters who may have simply tried out Spoutible for a time before moving on to another Twitter alternative, leaving semi-abandoned accounts ripe for the taking.
Spoutible CEO Christopher Bouzy confirmed the data breach and vulnerability and the company required users to create new, stronger passwords, after addressing the issue. However, he also referred to the vulnerability’s discovery as “an attack” on his network and alleged that the person who scraped the data was someone who was intent on hurting Spoutible’s reputation.
“We are…confident the person involved is the ringleader who has been attacking Spoutible for a year,” Bouzy said in a post, referring to the notifier who sent Hunt the scraped records.
In an email with TechCrunch, Bouzy laid out his ideas further, alleging that the online group known as “Doubtible,” which had emerged early last year, was behind the attack. Doubtible runs a Twitter/X account where they have “tweeted falsehoods about Spoutible, me, and prominent members of our community daily,” Bouzy said. “We firmly believe that this group is behind the unauthorized scraping of our data” — an accusation Bouzy repeated in a response to a review on Trustpilot, where he also suggested he was alerting the FBI to the matter.
“Someone doesn’t have to scrape 207k+ records to reveal a vulnerability,” Bouzy continued. “However, by also including data, it makes it significantly more newsworthy. Should someone aim to expose a vulnerability to tarnish a company’s reputation, Mr. Hunt would indeed be their ideal contact. The reason behind their choice is clear: Mr. Hunt’s tweets, blog post, and follow-up video perfectly align with their intentions. The manner in which Mr Hunt sensationalized and portrayed the incident is exactly what they were hoping for,” he added, conspiratorially.
Bouzy claims that the security vulnerability arose because someone on his team used a function intended for the user settings API with a function designed for the public API, which is why encrypted emails and phone numbers were exposed in plain text. He said that Spoutible has now partnered with a security firm to further review its systems, in light of this incident.
Still, several people have since accused Bouzy of attempting to downplay the severity of the vulnerability, including data journalist Dan Nguyen, who recently reshared tech entrepreneur Anil Dash’s post on Bluesky warning users to “get off spoutible.” Another Bluesky user colorfully referred to Spoutible’s dumping of user data as akin to “Montezuma’s Revenge.”
Though a data breach is already bad PR for a startup, there are now questions as to whether or not the company is silencing its critics.
One Spoutible user, Mike Natale, has publicly accused the CEO of deleting his posts on the social networking site, where he had pushed Bouzy to be more transparent.
“Bouzy…deleted all my posts and wiped my wall,” wrote Natale, in response to another Bluesky user.

Image Credits: Mike Natale on Bluesky (opens in a new window)
In another reply, Natale explained that Bouzy had initially reposted his posts on Spoutible to comment on the matter, but then deleted all of Natale’s posts when he pushed back against “the narrative that this was an attack” and “that other companies have had the same flaws.”
The missing posts don’t include the usual tag indicating their deletion. On Spoutible, posts that are removed have a system note attached reading “@user deleted this reply.” For instance, if Bouzy had deleted the reply, it would have read “@bouzy deleted this reply.”
But in this case, Natale said in comments on Bluesky that posts are just gone and his Spoutible main feed doesn’t even load.
The Twitter/X account Doubtible also posted about Natale’s claims. Natale responded to a request for comment from TechCrunch saying that someone had alerted him to his posts being removed after the exchange with Bouzy.
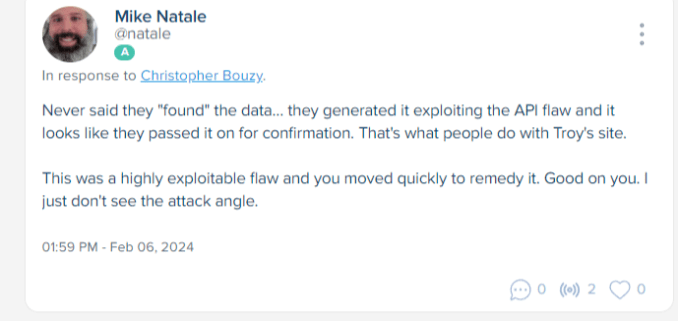
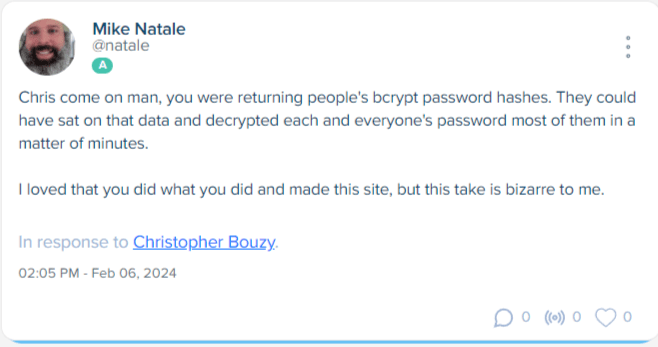
Image Credits: Natale’s deleted posts on Spoutible
“Spoutible did something to my account immediately after I pushed back on him framing Troy’s work as part of some sort of attack,” he said. Bouzy had “respouted” him a few times and Natale put up a few more posts trying to explain further. “At some point later on another platform someone asked me if I took my posts down. I hadn’t so I went back to Spoutible. My wall doesn’t really load, all my posts were gone (except one or 2), so I opened a ticket,” Natale said.
Meanwhile, Spoutible CEO Christopher Bouzy denies deleting Natale’s posts.
“Regarding the issue with user Natale, we did not delete their posts or account. It’s possible for users to remove their own content and then falsely accuse us,” he said, again suggesting a conspiracy. “The allegation is baseless and does not merit further discussion,” he concluded.
After publication, Natale responded to Bouzy’s comment by publishing screenshots of his broken Spoutible profile on rival network Bluesky. His profile shows he has “2 spouts” but nothing is displayed.

Image Credits: Mike Natale
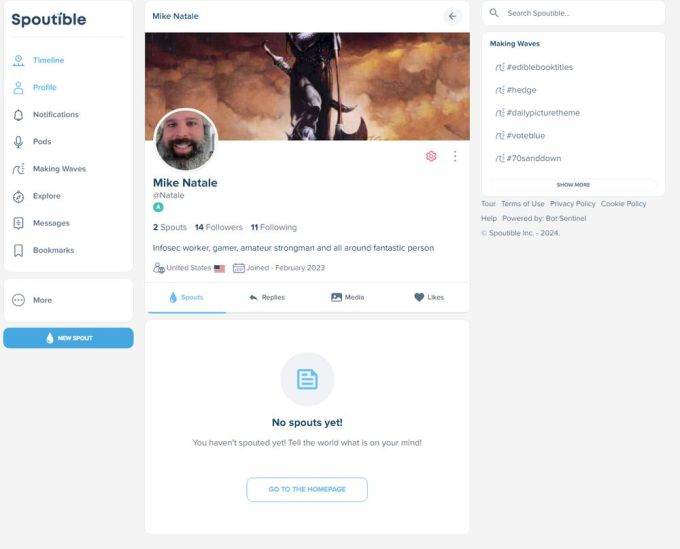
Image Credits: Mike Natale
The incident at Spoutible brings to mind another smaller company, Hive, which also experienced a major security issue after being flooded with Twitter users shortly after Elon Musk’s acquisition. In that case, the startup fully shut down its app to fix the critical flaws before returning to the app store. Hive managed to weather the storm and eventually return, but is no longer considered a threat to Twitter after its lost opportunity.
Whether Spoutible’s reputation will recover from this stain also remains to be seen.
Updated, 2/13/24, 7:30 AM ET with Natalie’s comment. Updated 2/15/24 2:36 PM ET with additional screenshots.
