It’s an open secret that the Internet of Things (if we must call it so) is pretty terrible, whether in standards, interoperability or security. You don’t really expect good security in a smart light bulb or coffee maker, though. A smart front door lock, however, really shouldn’t be quite this easy to hack.
Two different presentations at DEF CON this year made it clear that there’s a long way to go before we should start trusting the average smart lock — or even the nice ones (though if you had to choose, the latter is the better). This may surprise you, or you might have been saying it for years. At all events, these guys proved it with gusto.
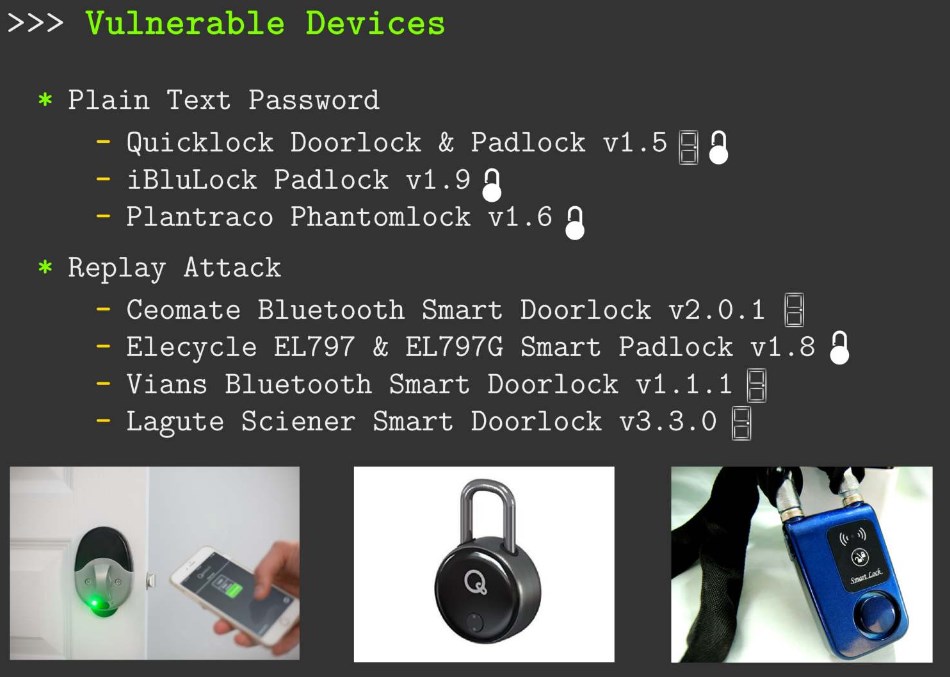
Anthony Rose and Ben Ramsey, from Merculite Security, showed off a bit of lock hacking done with less than $200 worth of off-the-shelf hardware. Some opened easier than others, but in the end 12 out of 16 yielded.
Locks from Quicklock, iBluLock, and Plantraco transmitted their passwords in plaintext, making them vulnerable to anyone with a Bluetooth sniffer. Others were tricked by the attacker simply replaying the same data they snatched out of the air when a legit user unlocked the door. Another entered a failstate and opened by default when it received an encrypted string that was off by one byte.
Worth noting as well: doing a bit of wardriving, the two found plenty of locks identifying themselves as such, making it easy for an attacker to find devices to listen in on.
This was a pretty poor showing altogether, although a few resisted Rose and Ramsey’s attempts: the Noke and Masterlock smart padlocks survived, and a Kwikset Kevo did as well — until they opened it with a screwdriver. Okay, that’s cheating, but the point stands.
Perhaps of most concern, only one of the 12 vendors the two contacted to inform them of these flaws responded — and even then, there was no plan to fix anything.
One that Merculite failed to crack was the August door lock, a rather more well known brand than the others (MasterLock notwithstanding). Fortunately, someone else had already made it their mission to break the thing wide open.
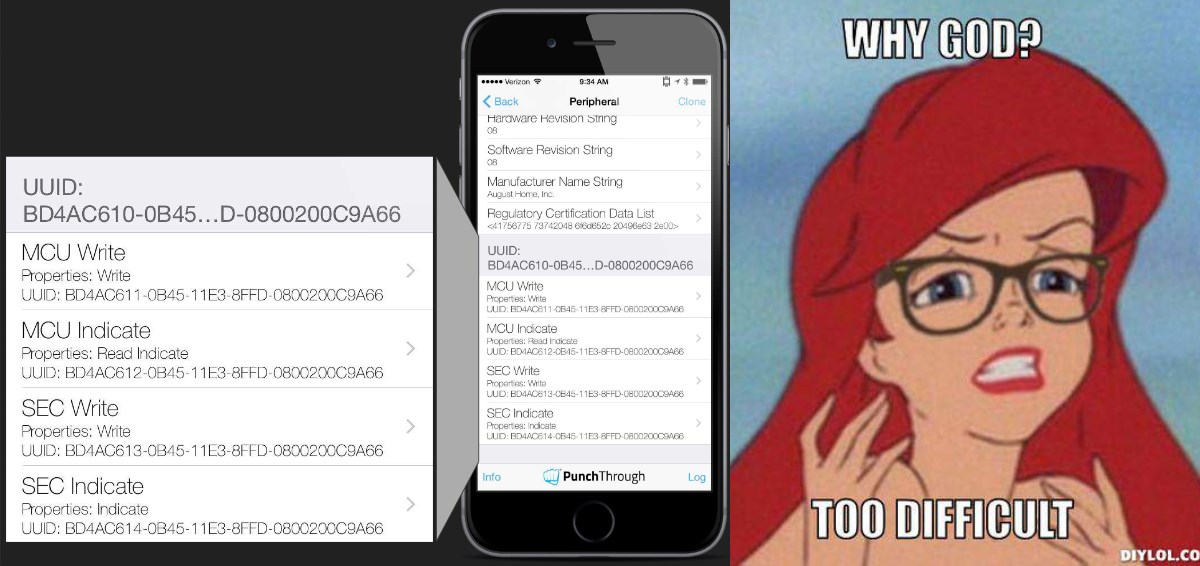
Jmaxxz’s entertaining, meme-filled presentation put the lie to several of the claims set forth by August, and although it’s unlikely your average B&E artist is going to bother to circumvent certificate pinning and paw through your logs, the security holes are real. Or were real — the hacker notes that August, unlike the other companies whose locks were hacked, has been responsive and at least some the issues have been fixed. (An August representative declined to provide more detail on the fixes, though the CEO has commented below.)
Many items that were too hard to get by ordinary hacking means like sniffers… could be found in plaintext in logs and the like. Jmaxxz is one of those hackers that doesn’t like to work any harder than he has to — and why should he? Still, it’s hard to believe that guests could ever award themselves extra lock permissions just by changing a string in the API calls from “user” to “superuser”!
For now, it seems, these locks are long on convenience and short on security. If you don’t mind having less-than-stellar security on your pool house or mother-in-law, this could be a nice way to keep your keychain light — but for the front door, you can do better.