Editor’s note: Oren Levy is CEO and co-founder of Zooz.
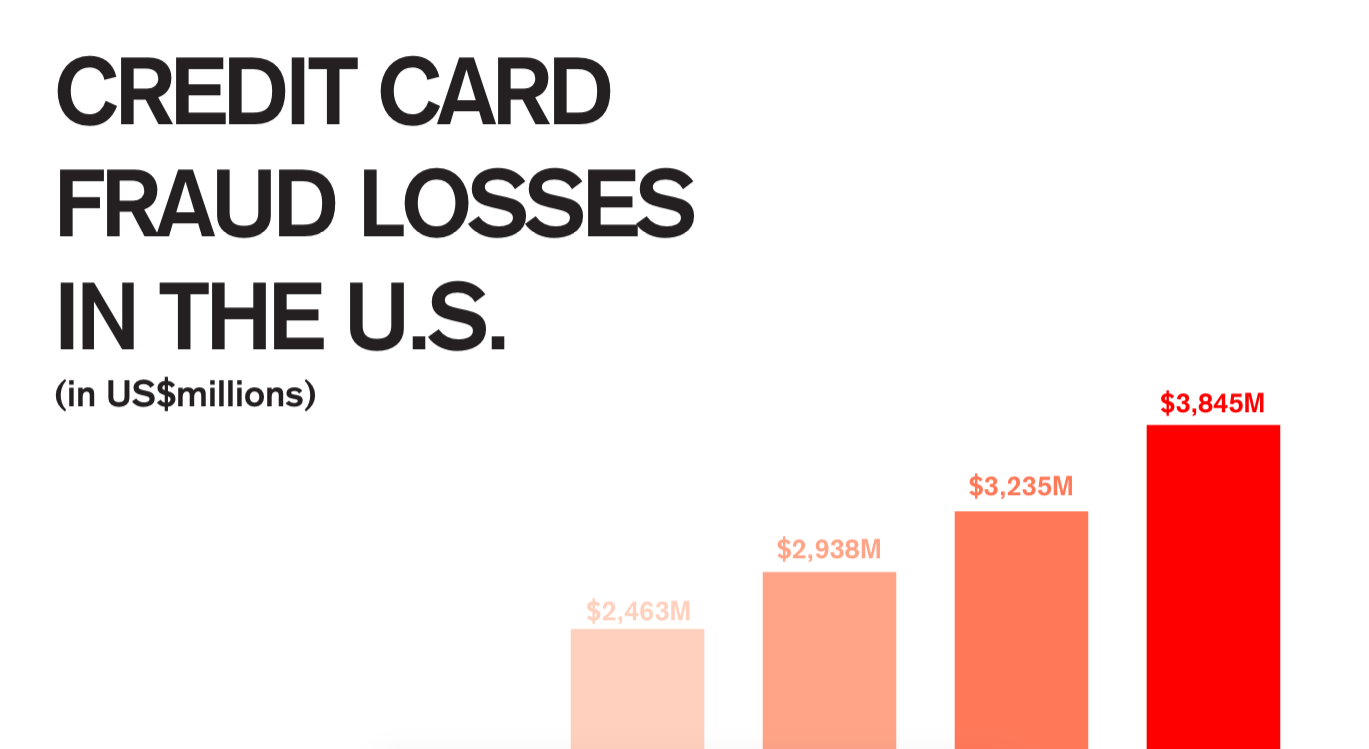
The cyber breaches and system hacks affecting Target, Home Depot, Neiman Marcus and other large retailers over the past two years have resulted in billions of dollars of credit card fraud. This growing epidemic has led to increased calls for a more robust credit card security system.
In October 2014, President Barack Obama took a significant step toward correcting this situation when he signed the BuySecure Executive Order, hastening a transition to the more secure EMV payment technology. EMV, which stands for Europay, MasterCard, and Visa, is a global standard for authenticating credit and debit card transactions that involves chip-compatible cards and point-of-sale (POS) terminals.
EMV technology has been around for years, and is widely accepted in Europe and around the world. When the U.K. switched to EMV cards, fraud at stores was cut by 70 percent. The U.S.’s continued use of the swipe-and-sign method is one of the main reasons why half of the world’s credit card fraud happens in the U.S.
How EMV Works
To understand why EMV is such a secure method, one must first understand the nature of retail fraud. The large-scale credit card thefts of recent years have involved hackers infecting terminals with malware that extracts credit card numbers.
This rogue software gives cyber thieves access to all of the important card data that is transferred during a card swipe. This data is known in the industry as “Track 2” data, and includes the full credit card number, expiration date, card verification value (CVV) and additional cardholder information. Using this data, hackers can create and issue counterfeit cards that are indistinguishable from the original and can be used for making purchases.
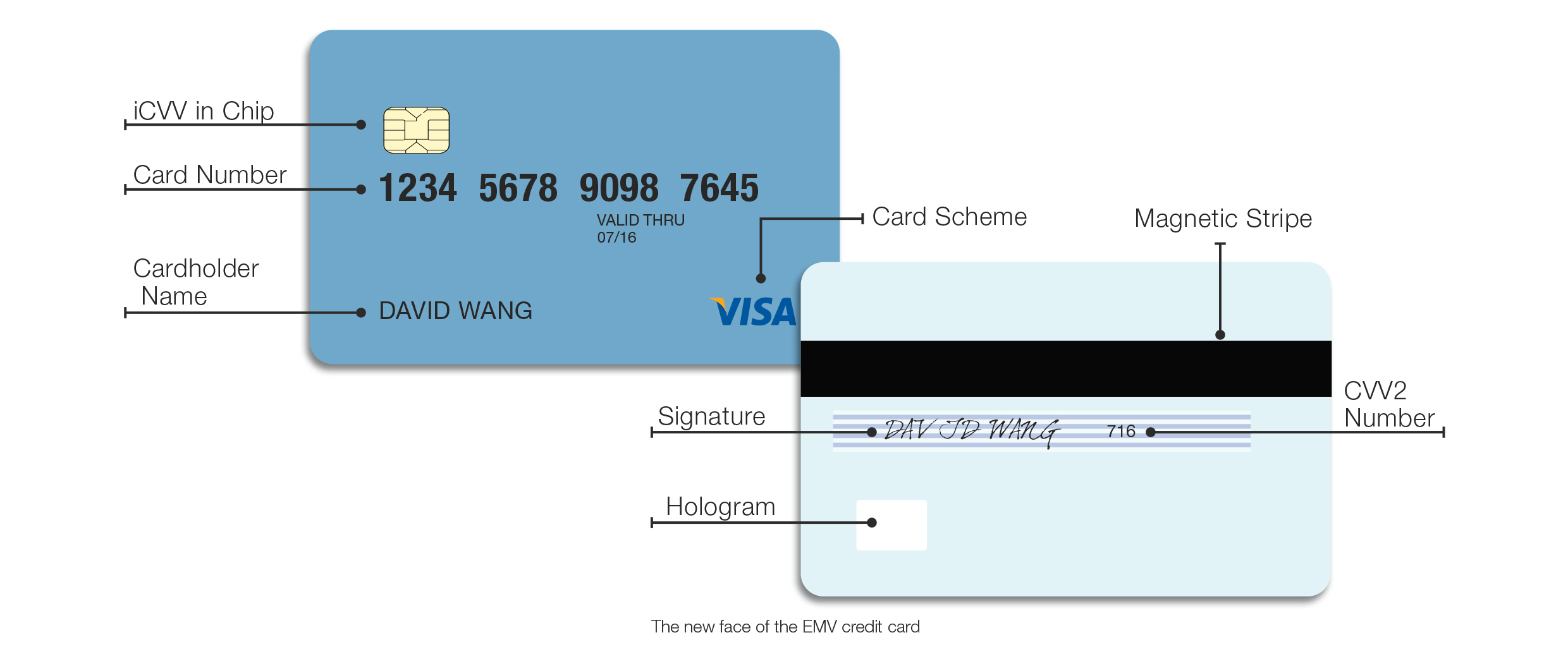
EMV cards, however, also include an integrated CVV (iCVV) that is embedded in a chip and not part of the Track 2 data. This data is encrypted, and only the issuing bank can decrypt it. If a fraudster steals the Track 2 data from the chip and creates a counterfeit card based on it, no transactions will be approved because the iCVV data is missing. EMV also requires card owners to enter a personal identification number (PIN) upon checkout, providing a second layer of fraud protection.
EMV Challenges
Despite its advantages, however, EMV is not a perfect solution. First of all, converting the entire country to EMV technology will be a logistical nightmare. Not only will tech implementation require considerable time and investment, but consumers accustomed to swipe-and-sign will also need time to adjust to the new method, slowing down checkout lines in the interim.
Perhaps the biggest issue with EMV is that, as secure as it is, it still cannot protect merchants or their customers from all possible threats.
For example, it has no impact at all on the security of online transactions. For these “card-not-present” purchases, fraudsters need only steal the card number, expiration data and CVV in order to start a shopping spree. Sophisticated hackers have discovered other vulnerabilities of the system as well; they are much more complicated than the simple hacks we are seeing today, but they do exist.
The Liability Shift
EMV is more evolution than revolution; it’s sort of like putting a firewall around your credit card, but it doesn’t otherwise change the payments ecosystem. Still, it would behoove retailers to adopt the new technology before October 2015, when the “liability shift” is scheduled to kick in.
After this date (unless it is postponed, which has happened previously), issuing banks will no longer be responsible for fraudulent transactions conducted by merchants using the old swipe-and-sign terminals. Instead, if the merchant’s payment technology is less secure than the bank’s, then the merchant will take on all liability.
EMV adoption raises the bar for everyone. As major retailers convert to EMV technology and consumers receive their new EMV-compliant cards in the mail, the merchants still using swipe-and-sign terminals are going to appear outdated and insecure. Customers will wonder why they have failed to invest in the more secure technology, and question how safe their transactions really are.
