Edward Snowden, whistleblower of the decade, has made it consistently clear that he didn’t trust cellphones. While he never described the methods governments and other miscreants used to crack into our handsets, he maintained that eavesdroppers could hear us even if the phone seemed off and everything on our devices was open to a dedicated hacker. But he never said how it was done.
Now we know… at least partially. The app used is called RCS/Galileo by an Italian company, The Hacking Team. The app allows for full control of the data on the phone and allows users to activate the microphone on Android, iOS, and Blackberry devices. In short, this is what Snowden feared.
An intercepted Skype call
In two very detailed and independent posts, both Citizen Lab and Kaspersky have produced some very interesting documentation of the program and have even traced a piece of Hacking Team software to a Trojan horse that had been modified to look like an Arabic news reader. The teams traced the command and control servers and found multiples in over 40 countries with the majority appearing in the U.S., Ecuador, and Kazakhstan. The major exploits included access to the following phone features and apps:
Recording voice
E-mail, SMS, MMS
Listing files
Cookies
Visited URLs
Cached web pages
Address book
Call history
Notes
Calendar
Clipboard
List of apps
SIM change
Live microphone
Camera shots
Support chats, WhatsApp, Skype, Viber
Log keystrokes from all apps and screens via libinjection
It should be noted that the iOS version requires a jailbroken phone – therefore requiring physical access to the phone – but it was easier to reverse engineer than the Android version. The Android version didn’t require a rooted device but was obfuscated to hide the functionality. All an attacker needed to do for an Android attack was to download an infected app like Qatif Today, a news app. By spoofing a legitimate app source, the attackers were able to install the Hacking Teams applications on phones in Arabic-speaking countries including Bahrain and Saudi Arabia.
The proof that these tools are used by the NSA or other governments is still circumstantial – no one has admitted to using the apps to spy on citizens – but the power of the remote control app is clearly disconcerting. An iOS phone left in a hotel room could be easily attacked and compromised at any time and Android phones are especially susceptible.
“This type of exceptionally invasive toolkit, once a costly boutique capability deployed by intelligence communities and militaries, is now available to all but a handful of governments,” wrote the Citizen Lab Researchers. “An unstated assumption is that customers that can pay for these tools will use them correctly, and primarily for strictly overseen, legal purposes. As our research has shown, however, by dramatically lowering the entry cost on invasive and hard-to-trace monitoring, the equipment lowers the cost of targeting political threats.”
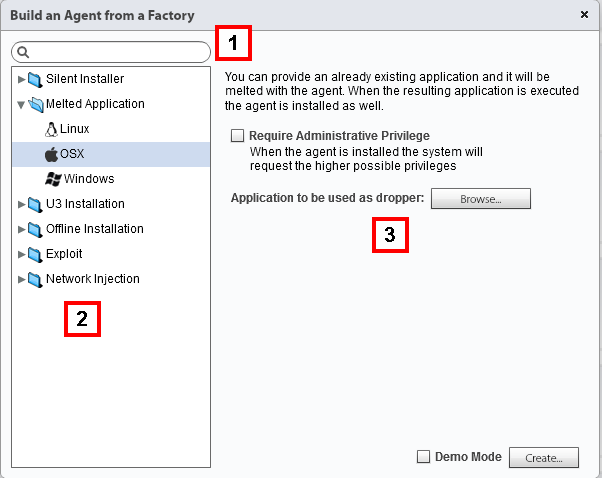
Citizen Lab has a full PDF of the manual used to train law-enforcement on use of the RCS program and, although they refused to make the entire document public they did publish some excerpts. Below we see one of the most jarring examples of the Hacking Teams tradecraft: the ability to inject malware into a seemingly innocuous app package and upload it with a single click. While tech-savvy users will claim that this sort of attack would never happen to them, it’s clear that now no one can know for sure.