Apple’s developer site went dark unexpectedly last Thursday and remained dark straight through the weekend. The company revealed yesterday that it was because an “intruder” attempted to access personal information pertaining to Apple’s registered developers. While Apple continues to work on revamping the Dev Center’s security and bringing the whole thing back online, a 25-year-old Turkish security researcher named Ibrahim Balic thinks that it may have been because of him.
But was it?
Balic swears up and down that he’s not a malicious hacker. Rather, he claims to be just a security buff who stumbled upon a way to access gobs of Apple user data, tried to warn the company about it, and made a (now private) video highlighting the security flaw in question when Apple wouldn’t respond. Because of Apple’s usual opacity, my multiple calls and emails have gone unanswered, so it’s nearly impossible to say for sure whether his poking around caused Apple to take action last week, but the timing definitely seems curious.
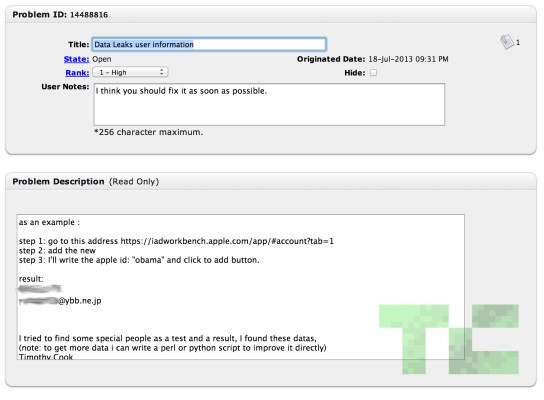
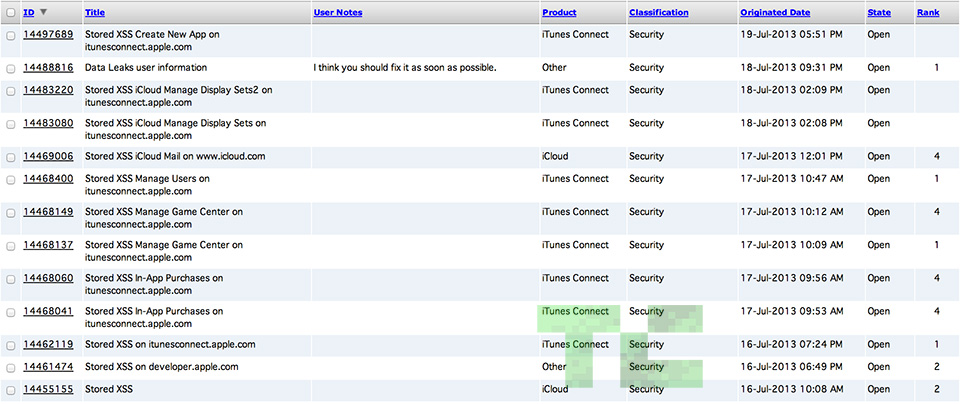
Let’s back up a minute. Balic is an avid bug hunter (he’s reported them to Facebook among others) and has filed a grand total of 13 bug reports to Apple since he first took an interest in the company on July 16. The one that gets most of the spotlight in his video seems to be Apple bug #14488816, which Balic reported on July 18 — the same day users first started reporting downtime for Apple’s Dev Center.
That little security issue is centered around Apple’s iAd Workbench, a recently launched tool that lets users craft and target iAd campaigns to better build hype around their iOS apps. Balic discovered that if you manipulated a request sent to the server that runs Workbench, it would allow you to try to add a new user to the account. From there you could try throwing in first names, last names — whatever really — and the server would then respond with a full name and email address. Once Balic understood the full scope of the problem, he (and this is where his rationale loses me a bit) wrote a Python script to scrape all the data he could find and showed some of it on YouTube.
And what of the Dev Center itself? On July 16 Balic did in fact file a bug report (#14461474) to Apple that dealt with the Dev Center’s vulnerability to a stored XSS attack. He said that it was technically possible to access user data by exploiting that issue, but he never attempted it. Instead, he claims he reported the problem and went off in search of the next big bug to report.
It’s too bad, though, that the video seemed so definitive: After showing off images of Apple’s downed Dev Center and the company’s official response, Balic then showed a slew of files that seem to contain full names and email addresses. It seems pretty damning, but Balic says that he never went after the Developer Center site directly, and all that user information he highlighted came from the iAd Workbench. Two separate bugs paved the way for one very confusing video.
Of course, he didn’t do a great job of explaining this. In a comment left in our original Dev Center hacking story, Balic pointed out that “one of those bugs have provided me access to users details etc” in reference to the iAd bug, and followed up by noting that “4 hours later from my final report Apple developer portal gas closed down and you know it still is.”
The poor framing of the comment made it seem as though he submitted that data leak bug report and Apple shut down the dev site shortly afterward, but his final bug report actually was filed hours later. He later added that neither the data of the 73 Apple employees nor the 100,000 subsequent data files he scraped had anything to do with that Developer Center exploit he reported on the 16th.
According to multiple files Balic sent to me, the data gleaned from the iAds issue is (thankfully) limited to names and email addresses. More worrying though is the idea that this particular bug could have affected more than just Apple’s developer community. An Apple representative told TechCrunch yesterday that only developer accounts could have been affected by the breach, but Balic insists that the issue he found returns regular email addresses and Apple IDs, too. There’s nothing encrypted about what he showed in the video — names and email addresses are rendered in plain text. I’ve contacted many of the users whose information appeared in the video but haven’t heard back yet, so we can’t confirm whether these people are developers or regular iTunes users, or if they’re just a bunch of random email addresses.
UPDATE: In his original #14488816 bug report, Balic included a few examples of user data that he was able to obtain through the iAds exploit. One of those email addresses he recovered belonged to our very own Josh Constine, who confirmed that it was in fact his Apple ID as well.
Throughout our conversation, Balic maintained that he was only ever trying to help Apple and plans to delete all the user data he’s collected so far. When asked why he downloaded all that user data rather than simply reporting the bug, Balic says he just wanted to see how “deep” he could go. If he wanted to do ill, he says, he wouldn’t have reported everything he found. For what it’s worth, he also says he never attempted to reset anyone’s password — the farthest he went was to email one of the addresses he had discovered and ask if it was really the person’s Apple ID. Balic didn’t get a response.
Is it possible that Balic’s poking around caught Apple’s attention and prompted the company to take the developer site down? Yes. The iAd Workbench may fall under the same broad umbrella as the Dev Center, and the Add User functionality that once appeared in the iAd Workbench seems to have disappeared. Only people within Apple really know what’s going on, and they’re just not feeling very chatty at the moment; I’ll update this post if they respond.