Several news outlets today wrongly reported that Anonymous Antisec hackers had leaked “newly available” Facebook law enforcement guidelines that explain how and what data can be obtained by officials with a subpoena, warrant, or court order. In fact, many versions of the outdated guides were already widely available thanks to an Electronic Frontier Foundation Freedom of Information Act request, as well as from other sources.
Though previously available and out of date, the new coverage about how Facebook provides user information when obliged by law could stoke fears about data privacy and Big Brother. By being more public with its law enforcement, guidelines Facebook could have avoided seemingly like it had something worth “leaking”.
[Update: Facebook has just published “Information for Law Enforcement Authorities” to its Safety Center. Most of the information was already available in the guides, but it includes details about data requests from international agencies, cost reimbursement for Facebook attaining and delivering data, and that Facebook does not provide expert testimony. By making this information publicly available, Facebook is less likely to be perceived as having something to hide.]
Talking Points Memo, which incorrectly wrote the guides were new, also reports that Facebook plans to publicly release a current version of its law enforcement guide next week. As of press time, Facebook’s Public Policy team couldn’t be reached to comment on the forthcoming guide. If published, it could fuel or quell discontent depending on details of how much data Facebook releases and what hoops officials must jump through to get it.
https://twitter.com/#!/EFF/status/139502678756691968
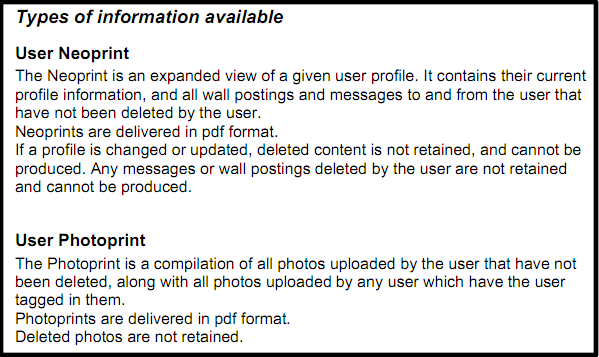
The “Facebook Law Enforcement Guidelines” explain how Facebook has in the past provided data sets with scary names such as “Neoprint” (all profile information and public communication), “Photoprint” (all uploaded and tagged photos), as well as IP logs of up to 90 days and user contact information. The latest versions of the guides from 2010 show that Facebook will release data “Upon receipt of a valid subpoena or a legal document with equivalent”.
The guides are a good read if you want to know exactly how Facebook and law enforcement cooperate. One move of Facebook’s that privacy advocates might like is that the company will suspend all fake accounts, even if belonging to law enforcement, as well as disable accounts wrongly accessed by law enforcement. There’s also some fun edits if you compare versions over the years. For example, Facebook has stripped out the line “Privacy and Integrity are cornerstones of the Facebook application and company philosophy.”
Facebook still stands to take damage from the trumped up release of these “leaked” guides. Facebook is in the business of building trust. The more secure and private people think their data is, the more they’ll be willing to give to add. Getting users to share biographical, location, online activity, and other data types is core to Facebook goals of showing users the most relevant content from their networks and powering its ads products.
If it publicly releases a current version the law enforcement guide, the company’s best bet is to be as transparent as possible. Critics could attack if additional unreleased information comes to light. Facebook will also need to message very clearly that it is legally obligated to provide data when ordered by the court. Then it can try to show that law enforcement agencies cannot carelessly request huge swaths of data. For most people, it’s potential for invasion of privacy without just cause that rattles trust in Facebook.