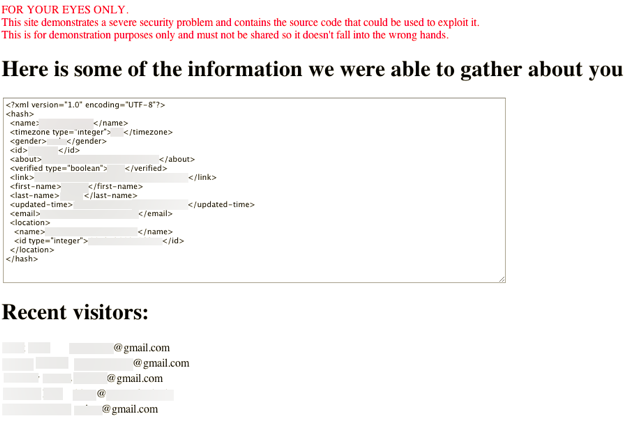
As if Facebook’s Instant Personalization needed another knock against it, tonight comes news of a security issue that makes the feature even more unnerving. Web security consultant George Deglin discovered an exploit that would allow a malicious site to immediately harvest a Facebook user’s name, email, and data shared with ‘everyone’ on Facebook, with no action required on the user’s part. This specific exploit has been patched, and no user data was compromised, but the security problems behind it remain.
As if Facebook’s Instant Personalization needed another knock against it, tonight comes news of a security issue that makes the feature even more unnerving. Web security consultant George Deglin discovered an exploit that would allow a malicious site to immediately harvest a Facebook user’s name, email, and data shared with ‘everyone’ on Facebook, with no action required on the user’s part. This specific exploit has been patched, and no user data was compromised, but the security problems behind it remain.
The exploit took advantage of Cross Site Scripting to inject malicious code into Yelp. Normally such an attack wouldn’t have particularly broad implications for Facebook users, but Yelp is, of course, one of the three sites that have been deemed fit for Facebook’s highly controversial Instant Personalization feature. The feature grants Yelp immediate access to much of a user’s core Facebook data as soon as they visit the reviews site, without having to bother with logins or Connect buttons. But with that convenience comes risk — if a site with Instant Personalization is compromised, it can put almost any Facebook user in harm’s way.
Here’s a high level description of how the exploit worked:
The script in my example would capture the browser cookies set for Yelp.com, extract a key required to make Open Graph API requests to the Facebook API, and send that key to my site. My site would then make a request for your name, email, etc. and store it in a database.
In other words, if you visited the malicious site, it would immediately harvest any data that Yelp had access to. And Yelp automatically has access to a lot, including your email, name, profile photo, current location, friend list, and networks. You wouldn’t have to accidentally click anything. The malicious site could do this even if you had never been to Yelp. Also worth noting: Yelp is automatically given access to your email address, when all other Facebook Connect sites have to ask for special permission to access it.
Update: This morning, Facebook claimed that any email address that was exposed by this exploit was not shared through Instant Personalization. That was false (more on that below). Here is the initial statement they gave us:
The problem was a vulnerability on Yelp’s site and was not specific to the instant personalization pilot program. If the vulnerability were actually exposed, a malicious person could have accessed data from a user that was already publicly available, among other data on the site. It’s important to note that email addresses were not shared through instant personalization, and a user could only have been impacted if he/she clicked a link that was shared with the sole intention of phishing that user.
After a lengthy back and forth, Facebook did indeed confirm that user email addresses were exposed to the attack. In fact, it appears that it was worse than we thought — not only could the malicious site access the user’s email address, it could also access all of the user’s friends’ email addresses. Facebook claims that Yelp was never supposed to have access to these email addresses, which is why they initially said our post was wrong. They say that the oversharing was caused by a bug.
Here’s their statement on the matter:
“Thanks for bringing this to our attention. It did reveal a bug on our side that has since been fixed.”
Fortunately Deglin is one of the good guys. After being notified of the security hole, Yelp and Facebook shut down Instant Personalization for an hour or two until a fix was in place.
But this is unsettling nonetheless. Instant Personalization has only been around for a few weeks on a mere three sites, and one of them has already had issues. Given how common XSS vulnerabilities are, if Facebook expands the program we can likely expect similar exploits. It’s also worth pointing out that some large sites with many Facebook Connect users — like Farmville.com or CNN— could also be susceptible to similar security problems. In short, the system just isn’t very secure.
Here are the statements each company had regarding the issue:
Yelp:
We were notified of a bug with our Facebook implementation. We immediately turned off the feature and pushed out a fix and the functionality is again live. No user information was compromised.
Facebook:
We were notified of a bug with Yelp’s Facebook implementation earlier today, at which point all related functionality was temporarily shut down before the issue was exposed. Yelp immediately investigated the issue, and the implementation is now back up and running.
Facebook has also had numerous other security issues, including a major cross-domain vulnerability and an issue that exposed users’ private Facebook chats.