A Portuguese-language spyware called WebDetetive has been used to compromise more than 76,000 Android phones in recent years across South America, largely in Brazil. WebDetetive is also the latest phone spyware company in recent months to have been hacked.
In an undated note seen by TechCrunch, the unnamed hackers described how they found and exploited several security vulnerabilities that allowed them to compromise WebDetetive’s servers and access its user databases. By exploiting other flaws in the spyware maker’s web dashboard — used by abusers to access the stolen phone data of their victims — the hackers said they enumerated and downloaded every dashboard record, including every customer’s email address.
The hackers said that dashboard access also allowed them to delete victim devices from the spyware network altogether, effectively severing the connection at the server level to prevent the device from uploading new data. “Which we definitely did. Because we could. Because #fuckstalkerware,” the hackers wrote in the note.
The note was included in a cache containing more than 1.5 gigabytes of data scraped from the spyware’s web dashboard. That data included information about each customer, such as the IP address they logged in from and their purchase history. The data also listed every device that each customer had compromised, which version of the spyware the phone was running, and the types of data that the spyware was collecting from the victim’s phone.
The cache did not include the stolen contents from victims’ phones.
DDoSecrets, a nonprofit transparency collective that indexes leaked and exposed datasets in the public interest, received the WebDetetive data and shared it with TechCrunch for analysis.
In total, the data showed that WebDetetive had compromised 76,794 devices to date at the time of the breach. The data also contained 74,336 unique customer email addresses, though WebDetetive does not verify a customer’s email addresses when signing up, preventing any meaningful analysis of the spyware’s customers.
It’s not known who is behind the WebDetetive breach and the hackers did not provide contact information. TechCrunch could not independently confirm the hackers’ claim that it deleted victims’ devices from the network, though TechCrunch did verify the authenticity of the stolen data by matching a selection of device identifiers in the cache against a publicly accessible endpoint on WebDetetive’s server.
WebDetetive is a type of phone monitoring app that is planted on a person’s phone without their consent, often by someone with knowledge of the phone’s passcode.
Once planted, the app changes its icon on the phone’s home screen, making the spyware difficult to detect and remove. WebDetetive then immediately begins stealthily uploading the contents of a person’s phone to its servers, including their messages, call logs, phone call recordings, photos, ambient recordings from the phone’s microphone, social media apps, and real-time precise location data.
Despite the broad access that these “stalkerware” (or spouseware) apps have to a victim’s personal and sensitive phone data, spyware is notoriously buggy and known for their shoddy coding, which puts victims’ already-stolen data at risk of further compromise.
WebDetetive, meet OwnSpy
Little is known about WebDetetive beyond its surveillance capabilities. It’s not uncommon for spyware makers to conceal or obfuscate their real-world identities, given the reputational and legal risks that come with producing spyware and facilitating the illegal surveillance of others. WebDetetive is no different.
But while the breached data itself reveals few clues about WebDetetive’s administrators, much of its roots can be traced back to OwnSpy, another widely used phone spying app.
TechCrunch downloaded the WebDetetive Android app from its website (since both Apple and Google ban stalkerware apps from their app stores), and planted the app onto a virtual device, allowing us to analyze the app in an isolated sandbox without giving it any real data, such as our location. We ran a network traffic analysis to understand what data was flowing in and out of the WebDetetive app, which found it was a largely repackaged copy of OwnSpy’s spyware. WebDetetive’s user agent, which it sends to the server to identify itself, was still referring to itself as OwnSpy, even though it was uploading our virtual device’s dummy data to WebDetetive’s servers.
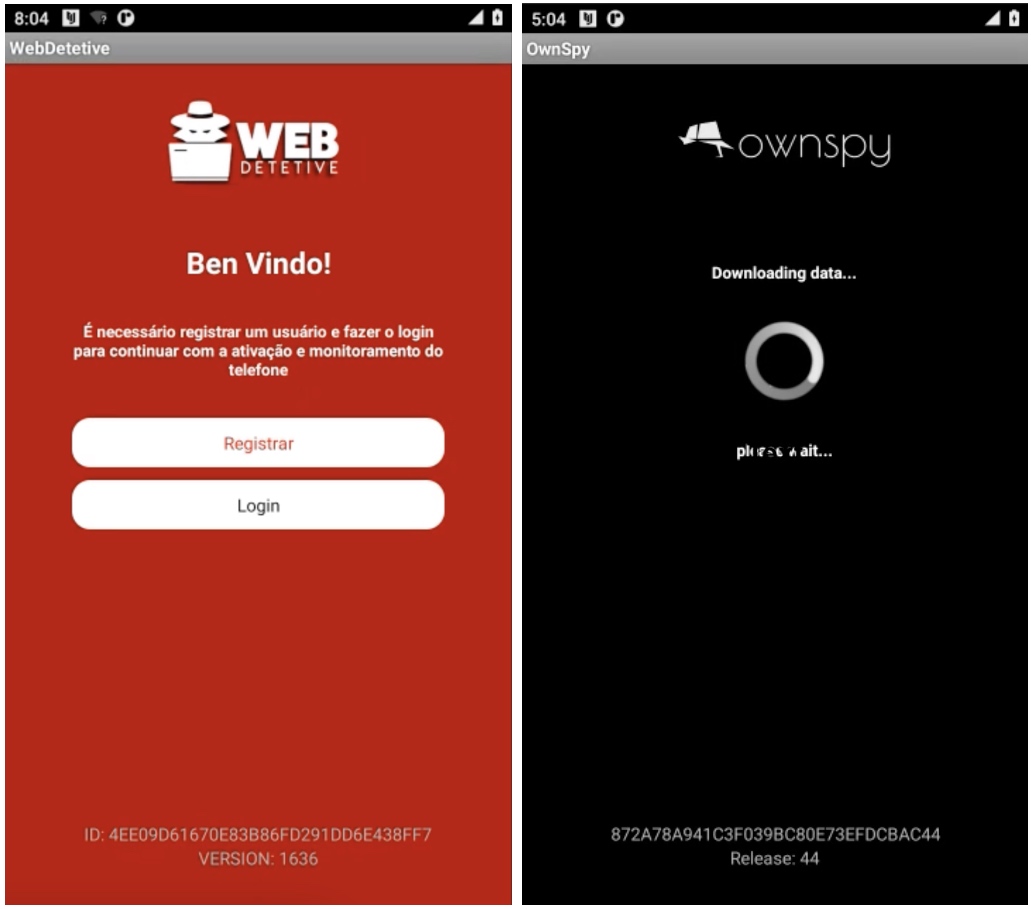
A side-by-side photo comparison of WebDetetive (left) and OwnSpy (right) running on Android. Image Credits: TechCrunch
OwnSpy is developed in Spain by Mobile Innovations, a Madrid-based company run by Antonio Calatrava. OwnSpy has operated since at least 2010, according to its website, and claims to have 50,000 customers, though it’s not known how many devices OwnSpy has compromised to date.
OwnSpy also operates an affiliate model, allowing others to make a commission by promoting the app or offering “a new product to your clients” in return for OwnSpy taking a cut of the profits, according to an archived copy of its affiliate’s website. It’s not clear what other operational links, if any, exist between OwnSpy and WebDetetive. Calatrava did not return a request for comment.
A short time after we emailed Calatrava, portions of OwnSpy’s known infrastructure dropped offline. A separate network traffic analysis of OwnSpy’s app by TechCrunch found that OwnSpy’s spyware app was briefly nonfunctional at the time of publication. WebDetetive’s app continues to function.
Destructive attack?
WebDetetive is the second spyware maker to be targeted by a data-destructive hack in recent months. LetMeSpy, a spyware app developed by Polish developer Rafal Lidwin, shut down following a hack that exposed and deleted victims’ stolen phone data from LetMeSpy’s servers. Lidwin declined to answer questions about the incident.
By TechCrunch’s count, at least a dozen spyware companies in recent years have exposed, spilled, or otherwise put victims’ stolen phone data at risk of further compromise because of shoddy coding and easily exploitable security vulnerabilities.
WebDetetive founder Leonardo Duarte did not respond to a request for comment. An email sent to WebDetetive’s support email address about the data breach — including whether the spyware maker has backups — went unreturned. It’s not clear if the spyware maker will notify customers or victims of the data breach, or if it still has the data or records to do so.
Destructive attacks, although infrequent, could have unintended and dangerous consequences for victims of spyware. Spyware typically alerts the abuser if the spyware app stops working or is removed from a victim’s phone, and severing a connection without a safety plan in place could put spyware victims in an unsafe situation. The Coalition Against Stalkerware, which works to support victims and survivors of stalkerware, has resources on its website for those who suspect their phone is compromised.
How to find and remove WebDetetive
Unlike most phone monitoring apps, WebDetetive and OwnSpy do not hide their app on an Android home screen, but instead disguise themselves as an Android system-presenting Wi-Fi app.
WebDetetive is relatively easy to detect. The app appears named as “WiFi” and features a white wireless icon in a blue circle on a white background.
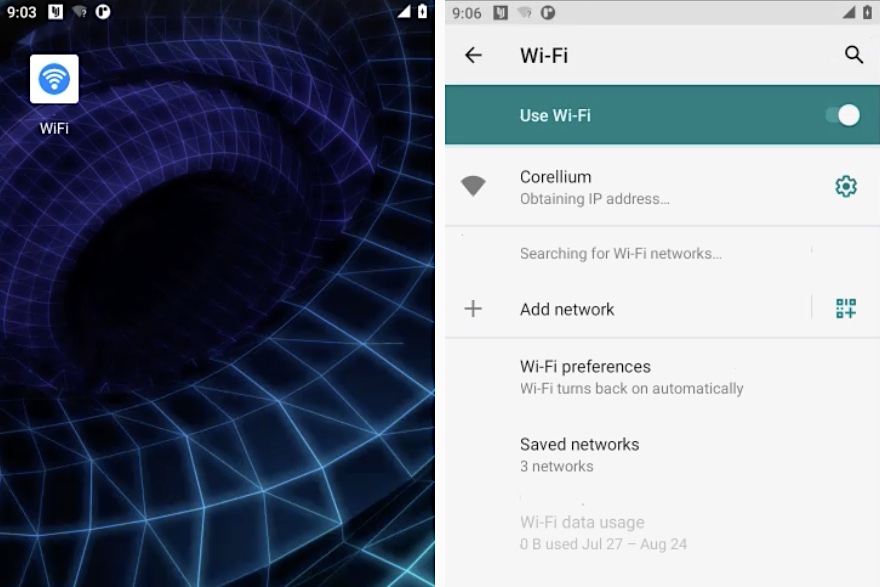
A screenshot showing the “WiFi” app, which presents as a system Wi-Fi app. However, this app is spyware in disguise. Image Credits: TechCrunch
When tapped and held, and the app info is viewed, the app is actually called “Sistema.”
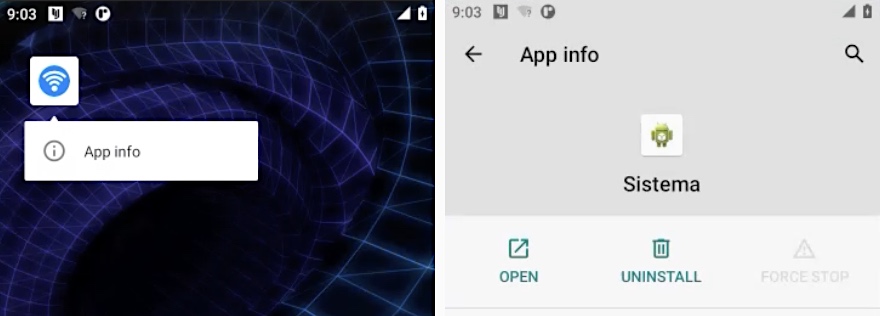
This “WiFi” app icon, when tapped, will actually show as an app called “Sistema,” designed to look like an Android system app, but is actually WebDetetive spyware. Image Credits: TechCrunch
We have a general guide that can help you remove Android spyware from your phone, if it is safe to do so. You should ensure that Google Play Protect is switched on, as this on-device security feature can defend against malicious Android apps. You can check its status from the settings menu in Google Play.
Updated with details on WebDetetive’s founder.
If you or someone you know needs help, the National Domestic Violence Hotline (1-800-799-7233) provides 24/7 free, confidential support to victims of domestic abuse and violence. If you are in an emergency situation, call 911. The Coalition Against Stalkerware also has resources if you think your phone has been compromised by spyware.
