As a former CTO, I know that integrations are required to deliver data-driven products online. I’ve designed transactional data systems that integrated with global telecom networks, applicant tracking systems and cloud-based infrastructures. Powerful integrations are not hard to conceive. It’s easy to identify data you would like to share between two different systems.
An integration, however, is beset by the same suite of pitfalls that any product feature or technological innovation may require, with one big wrinkle: At least half of the requirements were never designed with you, your use case or your organizational goals in mind.
The complex relationship of your vendors, technology and your overall business makes integrations a hard problem. It also makes potential solutions very brittle. If the problem you’re trying to solve is a SOC 2 audit or ISO 27001 certification to drive sales, an integration will not make passing your audit quicker. In reality, it will make it harder to achieve.
The problem you’re trying to solve
Before widely published security standards like SOC 2 or ISO 27001, much of security work was siloed into specific business functions like board management, HR or infotech. Each group designed best practices according to the expertise of their leaders. Few buyers ever asked questions.
Having a published standard with a validated testing or audit methodology provides an important new signal in your entire organization’s maturity. Buyers can point at specific credentials and require companies to accomplish an independent assessment to be certified. As the number and variety of vendors have grown, buyers have increasingly identified efficient tools to analyze your security stance.
The best time to implement an integration is when you’re sure it’s useful.
If the problem you’re trying to solve is trust via certification, does a technical integration accelerate compliance?
Integrations inhibit compliance and increase risk
There are zero integration requirements for SOC 2, ISO 27001, HIPAA or even CMMC, and there is no published security standard that requires an integration to achieve compliance. Even common standards such as PCI-DSS, GDPR or CCPA can be achieved without integrations, deployed agents or enterprise technology.
This is because all security standards are designed to not require any specific technology, personnel or processes. The authors of standards such as ISO 27001 recognize that each company is increasingly unique. For example, companies that offer an on-prem or private cloud deployment model are likely not required to comply with the monitoring portion of the SOC 2 Security standard during audit. Services organizations that develop intellectual property, such as software for their customers, are likely not required to comply with the change management portions of ISO 27001 and SOC 2 Security.
Implementing integrations into change management or end point monitoring for all organizations is the ultimate definition of security theater. Not only is it not required by the auditor, if you were to implement these security controls, you wouldn’t actually achieve greater security. Your highly talented engineering team must implement and support multiple cloud integrations for a non-existent risk.
Finally, if you were to actually be audited on those controls, you may find the auditor reports a serious deficiency in your control design, which wasn’t required in the first place and was therefore not operated properly.
Scope = cost or time (or both)
Like any project, the best way to accelerate delivery is to reduce the scope. Countless hours are spent by product and technology teams on finding what the “minimum viable” solution could be. Focusing on the problem you are trying to solve can help you limit the time, money and disruption caused by developing a new feature.
When developing your security posture, it’s important to have good design. Just as engineers need technical design to develop a feature, your organization needs to design a security posture that fits your business. Starting with a simple risk analysis will identify major security concerns for your organization.
In just a couple of hours, you can cut months off your initial compliance goals and reduce organizational change requirements dramatically. Once you’ve agreed upon an initial set of security controls that mitigate organizational risks, it’s easy to distribute the implementation of those controls.
Is “constant compliance” necessary?
Once you’ve identified the effective controls your organization has implemented, it’s time to identify how to validate or assess that the controls were implemented effectively. If your goal is to prepare for an independent certification or audit of your security controls, you will need to collect evidence that each control was designed and operated effectively. Evidence collection is an ongoing process, but it’s not a constant process.
I’m shocked by the concept that our infrastructure, laptops and mobile devices would need to constantly share data with a third-party vendor. “Continuous compliance” seems to require that I open up the most vulnerable assets under my control to constant communication.
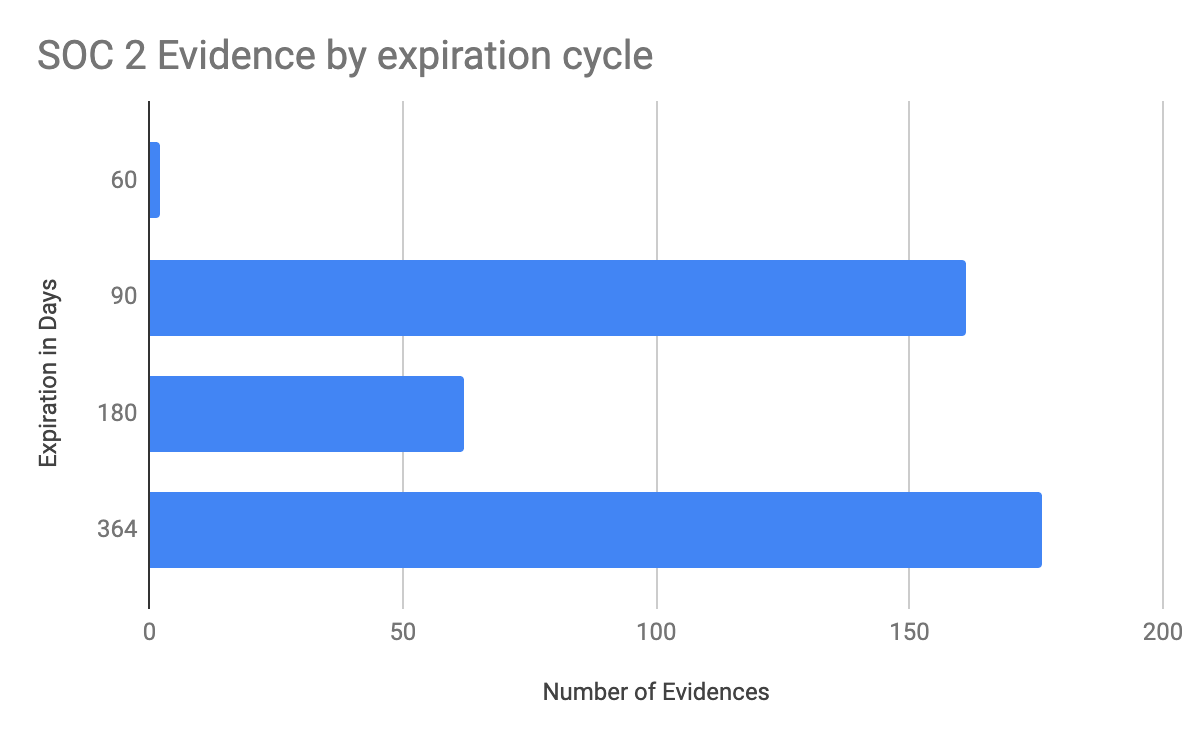
Image Credits: Justin Beals
An analysis of common SOC 2 evidence (as shown above) of 100 companies shows that no evidence expires in fewer than 60 days. The average evidence expiration timeline is six months! It’s hard to justify the effort of an integration when a simple screenshot of your IAM policy every six months will achieve certification.
“Constant compliance” is redundant to existing solutions, readily available and infinitely more secure. I recently met with a CTO who was considering a third-party endpoint protection tool for an AWS-hosted application. Within five minutes, we identified that endpoint protection was not a requirement for their SOC 2. Instead, AWS endpoint monitoring (CloudWatch synthetics to monitor sites, API endpoints, web workflows), included in their AWS subscription, would suffice. Finally, instead of needing “constant compliance” by deploying a third-party agent inside their cloud environment, a quarterly review and screenshot was all their auditor would require for a clean SOC 2 Type II audit.
Identify the useful integrations
The best time to implement an integration is when you’re sure it’s useful. After scoping an effective security practice by designing the organization’s controls, make sure you’re comfortable operating them. During the roll-out of any organizational changes, there will likely be tweaks to your agreed-upon controls. This can dramatically change what evidence is needed and how often it should be collected. Before considering an integration, it’s best to make sure that you’re identifying a valuable set of data in an agreed-upon location that is worthy of automation.
Taking this approach will identify problems that technology can solve. For example, our team has been utilizing cloud deployment technologies (infrastructure-as-code) to open a vast amount of cloud configuration data normalized between major cloud computing providers, which is valuable automation for evidence collection.
Executing security that matters
The time to solve efficiency problems with technology is not before you receive an audit, but after. These standards have been designed with your unique circumstances in mind. After you have a security practice in operation and understand the best practices for validation, then it’s time to consider integration and automation.
As a technology leader, your time is precious. While achieving a security audit is a critical contribution that will accelerate revenue growth, it takes time away from product innovation. Overburdening your technology infrastructure with integrations, new vendors and security theater only reduces your team’s effectiveness.
Focus instead on designing an efficient, yet effective, security practice by identifying the controls that matter. Validate the design of your security practices by first measuring effective operation. Once you have achieved your first security audit or certification, identify what automation will continue to make your security practices more efficient and effective.
