In case you missed it: A ransomware attack saw patient data stolen from one of the largest U.S. fertility networks; the Supreme Court began hearing a case that may change how millions of Americans use computers and the internet; and lawmakers in Massachusetts have voted to ban police from using facial recognition across the state.
In this week’s Decrypted, we’re deep-diving into two stories beyond the headlines, including why the breach at cybersecurity giant FireEye has the cybersecurity industry in shock.
THE BIG PICTURE
Google researcher finds a major iPhone security bug, now fixed
What happens when you leave one of the best security researchers alone for six months? You get one of the most devastating vulnerabilities ever found in an iPhone — a bug so damaging that it can be exploited over-the-air and requires no interaction on the user’s part.

The AWDL bug under attack using a proof-of-concept exploit developed by a Google researcher. Image Credits: Ian Beer/Google Project Zero
The vulnerability was found in Apple Wireless Direct Link (AWDL), an important part of the iPhone’s software that among other things allows users to share files and photos over Wi-Fi through Apple’s AirDrop feature.
“AWDL is enabled by default, exposing a large and complex attack surface to everyone in radio proximity,” wrote Google’s Ian Beer in a tweet, who found the vulnerability in November and disclosed it to Apple, which pushed out a fix for iPhones and Macs in January.
But exploiting the bug allowed Beer to gain access to the underlying iPhone software using Wi-Fi to gain control of a vulnerable device — including the messages, emails and photos — as well as the camera and microphone — without alerting the user. Beer said that the bug could be exploited over “hundreds of meters or more,” depending on the hardware used to carry out the attack. But the good news is that there’s no evidence that malicious hackers have actively tried to exploit the bug.
News of the bug drew immediate attention, though Apple didn’t comment. NSA’s Rob Joyce said the bug find is “quite an accomplishment,” given that most iOS bugs require chaining multiple vulnerabilities together in order to get access to the underlying software.
FireEye hacked by a nation-state, but the aftermath is unclear
Yesterday’s breaking news that cybersecurity giant FireEye had been hacked, likely by a “sophisticated threat actor” backed by a nation-state government, has sent the cybersecurity world into shock. FireEye is often the first company that cybersecurity victims — including governments — call when they’ve fallen victim to hackers. The fact that FireEye was hacked to begin with is like robbers breaking into Fort Knox and walking out unimpeded after stealing all of the gold.
FireEye has not yet pointed blame at any particular country for the breach — though Russia is a prime target, per the Washington Post and The New York Times. But the company admitted that it has never seen hacking techniques like this in the past.
The hackers made off with the company’s red team tools, which help the company run mock cyberattacks against their customers who pay FireEye to test their defenses. Those tools could potentially make it easier for attackers to hack into their targets, though FireEye has already published the methods and means for companies to defend against those tools.
There’s also a real fear that the hackers could also publish the tools, similar to an incident three years ago that saw hackers steal and publish hacking tools developed by the National Security Agency. Those tools were used by North Korean-backed hackers to spread the WannaCry ransomware around the world, crippling hospitals and causing millions in damages.
But as Wired reports, given that there were no zero-day exploits in the code, there’s no rush to get emergency patches out to millions of computers.
U.S. used Patriot Act to collect logs of website visitors
New reporting from The New York Times shows that the U.S. government used the Patriot Act to collect website logs showing who had visited a particular website. The statute has long been assumed to have been used to collect website logs, just as it does millions of Americans’ call logs every day.
But a letter to a prominent Democratic senator from the director of national intelligence confirms the legal authority extends to the web.
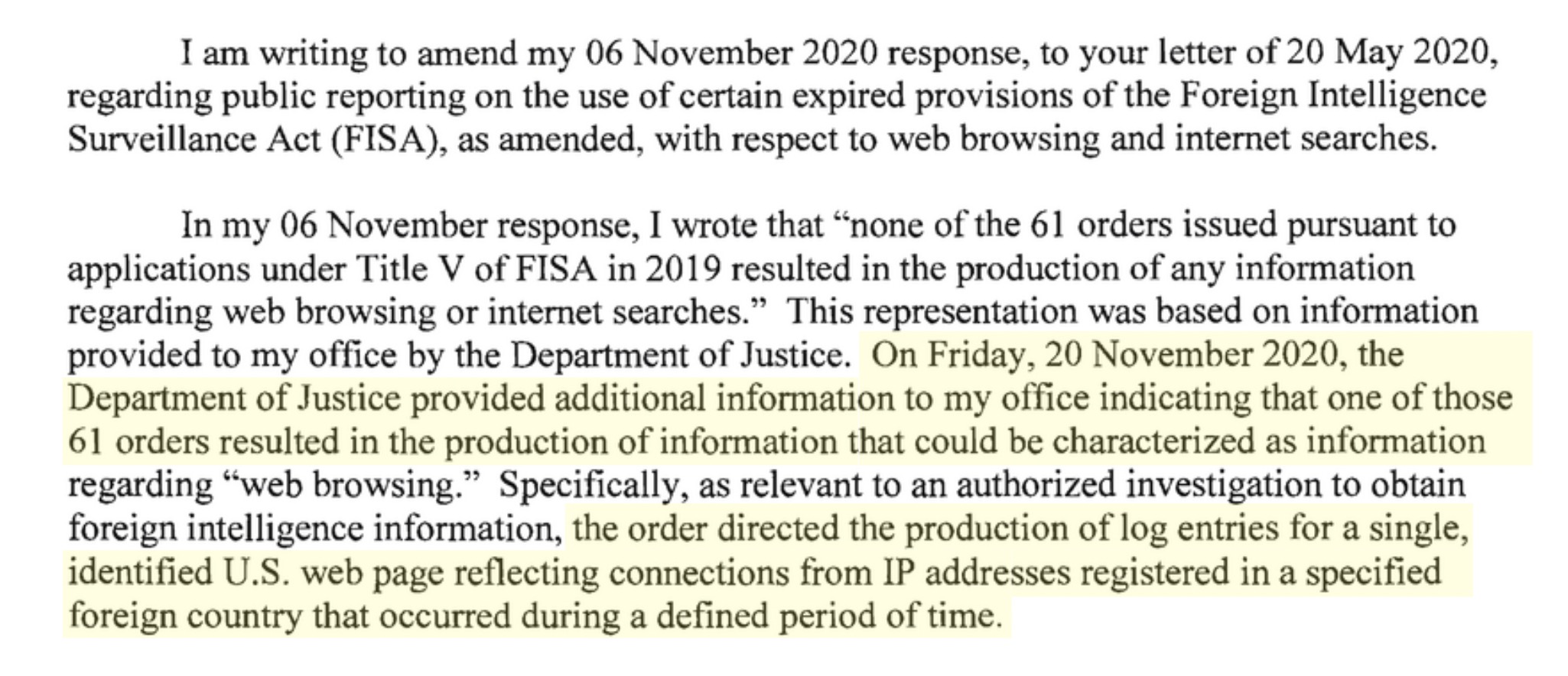
A letter from the U.S. director of national intelligence to Sen. Ron Wyden, who sits on the Senate Intelligence Committee. Image Credits: The New York Times)
The letter says that the statute, known as Section 215 for its place in the law books, was used to authorize one order that approved the government’s collection of logs revealing which computers “in a specified foreign country” had visited “a single, identified U.S. web page.”
That seems limited in scope for that particular order, granted by a body of judges designed to oversee the U.S. government’s surveillance powers known as the Foreign Intelligence Surveillance Court. But the legal line in the sand does not allow the government to collect the keywords that people enter into search engines because that would require a warrant.
That still leaves open the possibility that the limited example that the government gave is not representative of the surveillance in practice. Wyden, who introduced an amendment earlier this year that would’ve required a warrant before accessing Americans’ web browsing data that narrowly failed to pass by a single vote, said that the government has “provided no guarantee” that the government wouldn’t use these same powers to intentionally collect Americans’ web browsing data in the future.
There’s also no clear answer whether the powers are used to collect web browsing data in bulk, just like the powers are used for the call records program.
MOVERS AND SHAKERS
The White House could well be about to get a cyber-shakeup. Just this week, the House voted with a veto-proof majority to pass the annual defense budget and policy bill, the National Defense Authorization Act. That’s going to help the House when it comes up against Trump’s threat to veto the NDAA if it didn’t put in provisions to scrap Section 230, which would open up online platforms to legal liability for content their users post on their sites. (The timing coincided with an unflattering Twitter hashtag about the president that was going viral at the time.)
Packed inside the bill are a ton of cybersecurity-focused provisions that would, among other things, establish a White House national cybersecurity director, a post that previously existed under the National Security Council, but was scrapped by President Trump in 2018 — to much bipartisan protest by lawmakers.
The NDAA would also create positions for a cybersecurity director in each state to improve cyber coordination across the U.S. Another provision would give CISA powers to subpoena ISPs in order to get in contact with the owners of critical infrastructure when a vulnerability is found. TechCrunch first reported the proposal last year.
It’s a huge win for federal cybersecurity legislation, baking in 26 of the 34 recommendations from the Solarium Commission, which set out to modernize U.S. cyber deterrence to protect against cyberattacks.
$ECURITY $TARTUPS
Cybersecurity startup Dragos has raised $110 million in a massive Series C raise to continue its work securing industrial control systems. TechCrunch spoke with founder and chief executive Robert Lee about the raise.
Israeli cloud security startup Orca Security has raised $55 million in its new Series B round. Orca helps customers maintain cloud security and compliance. Using its SideScanning technology, Orca can scan an entire company’s data estate and cloud assets to find security problems.
Beyond Identity, a security startup that’s trying to eliminate passwords by using certificate-based authentication that works across platforms, has raised $75 million at Series B, bringing its total investment to $105 million.
And while you’re here, don’t forget to check out how At-Bay secured $34 million to shore up cybersecurity insurance.
Send tips securely over Signal and WhatsApp to +1 646-755-8849.