Researchers from Georgia Institute of Technology have released a full report on a new attack vector that affects Android up to version 7.1.2. The exploit, called Cloak & Dagger, uses Android’s design and screen behaviors against users, effectively hiding activity behind various app-generated interface elements that lets a hacker grab screen interactions and hide activity behind seemingly innocuous screens.
The team, Yanick Fratantonio, Chenxiong Qian, Simon Pak Ho Chung, and Wenke Lee, have created proof of concept users of the exploit including a bit of malware that draws an invisible grid over the Android screen that exactly mirrors – and can capture – the onscreen keyboard.
“The possible attacks include advanced clickjacking, unconstrained keystroke recording, stealthy phishing, the silent installation of a God-mode app (with all permissions enabled), and silent phone unlocking + arbitrary actions (while keeping the screen off),” wrote the researchers on a dedicated website. They discovered the exploit last August.
From the paper:
Cloak & Dagger is a new class of potential attacks affecting Android devices. These attacks allow a malicious app to completely control the UI feedback loop and take over the device — without giving the user a chance to notice the malicious activity. These attacks only require two permissions that, in case the app is installed from the Play Store, the user does not need to explicitly grant and for which she is not even notified. Our user study indicates that these attacks are practical. These attacks affect all recent versions of Android (including the latest version, Android 7.1.2), and they are yet to be fixed.
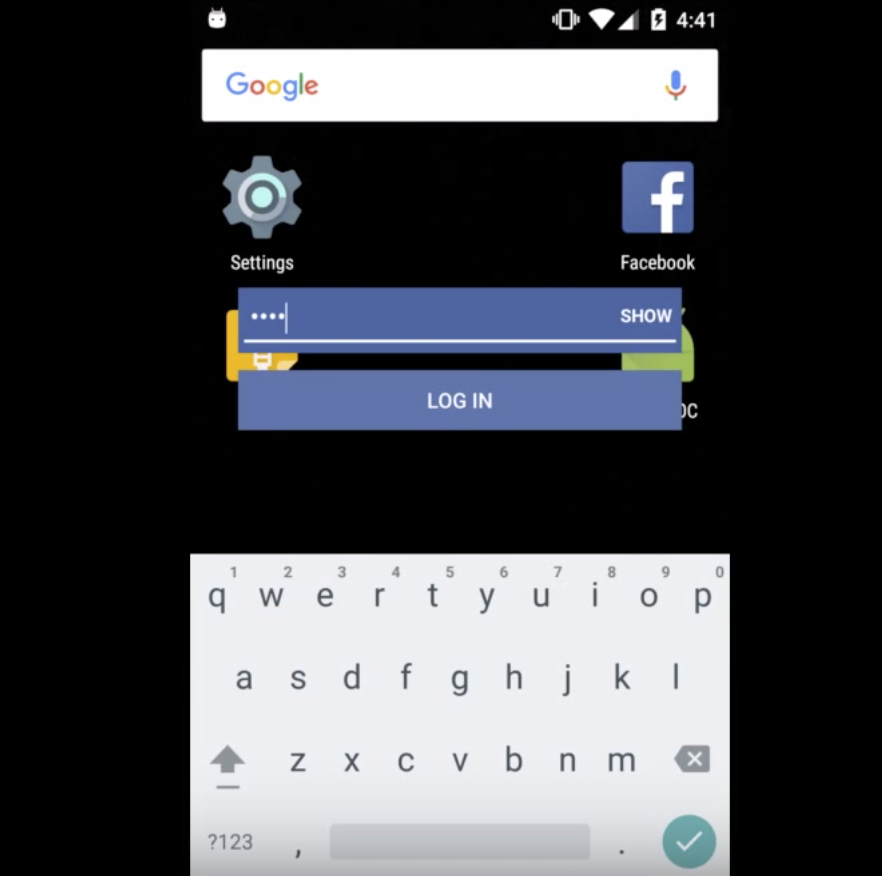
The exploit depends primarily on Android’s SYSTEM_ALERT_WINDOW (“draw on top”) and BIND_ACCESSIBILITY_SERVICE (“a11y”) to draw interactive elements over real apps. For example, in the image above, the team drew a reasonable facsimile of the Facebook password field over the real password field for the app. The user then typed in their real password into the seemingly real password field. However, when the Facebook app is closed you can see the remaining password field hanging in space.
The easiest way to disable this exploit in Android 7.1.2 is to turn off the “draw on top” permission in Settings>Apps>”Gear symbol”>Special access>Draw over other apps.
Fratantonio’s advice? “The usual: don’t install random apps, check the permissions they have (but it’s tricky: these permissions are treated as ‘special’ and the user needs to navigate to special menus. We added the instructions to the website).”
“As of now, I think these attacks are as powerful as they can get,” he said. “The ball is in Google’s court now. That being said, it seems the new version of Android O might address some of these, we’ll start playing with it right away and see how it looks. We’ll keep the website updated.”
Google writes: