
Image Credits: Bryce Durbin / TechCrunch
A TechCrunch investigation found that a notorious spyware operation called TheTruthSpy is actively facilitating the secret surveillance of hundreds of thousands of Android users around the world.
This spyware lookup tool provided by TechCrunch lets you check if your Android device was compromised by TheTruthSpy.
TheTruthSpy is one of a fleet of consumer-grade spyware apps, including iSpyoo, Copy9 and others, which are planted on a person’s phone typically with knowledge of their passcode. These stealthy apps are designed to stay hidden on home screens, but all the while silently and continually upload the private contents of a victim’s phone — including their phone logs and call recordings, messages, and real-time location — to a dashboard viewable by the abuser.
TechCrunch’s investigation found that TheTruthSpy’s apps share a common simple security vulnerability that continues to expose the personal data of hundreds of thousands of Android users.
The security bug, which allows anyone to remotely gain near-unfettered access to a victim’s device data, is extremely easy to find and exploit but remains unfixed by TheTruthSpy’s operators. TechCrunch continues to withhold details of the bug due to the risk it poses to victims. Instead, we published details about the inner workings of the spyware operation and the people who run it.
TechCrunch was later provided with leaked sets of data that included records on every Android device compromised by TheTruthSpy. The data sets contain either the IMEI number or the unique advertising ID associated with every compromised device up to and including December 2023.
Using the leaked lists of compromised devices, TechCrunch built this spyware lookup tool to let you check to see if your Android device was compromised by TheTruthSpy apps, and to provide resources for removing the spyware from your device.
How does the TheTruthSpy spyware lookup tool work?
Before you start, it’s important to have a safety plan in place. The Coalition Against Stalkerware and the National Network to End Domestic Violence offer advice and guidance for victims and survivors of stalkerware.
This is how you get started with the tool.
1. Find a device you know to be safe, like the phone of a trusted friend or a computer in a public library.
2. Visit this same webpage from that trusted device.
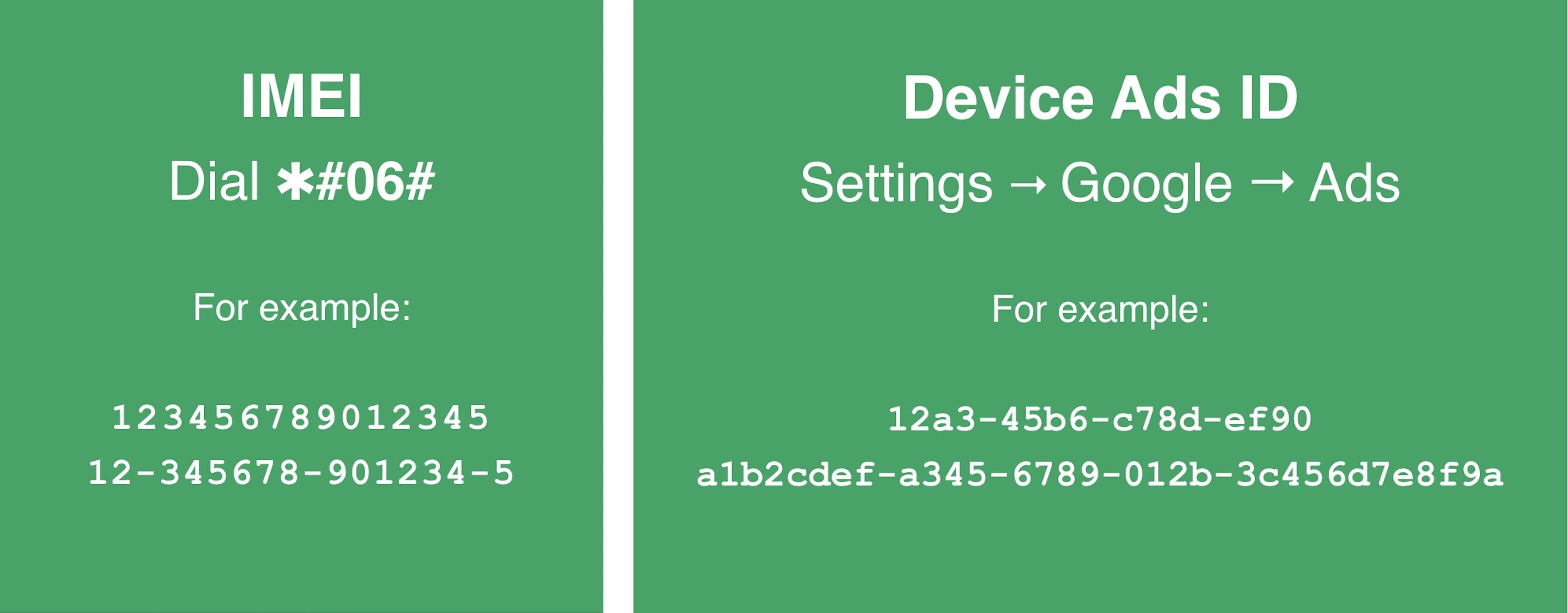
3. Enter below the IMEI number or device advertising ID of the device you suspect to be compromised into the lookup tool. You may want to check both.
This is how you find them:
- An IMEI number is a 14-15 digit number that is unique to your cell phone. From your phone’s dial pad, type in ✱#06# and your IMEI number (sometimes it’s called an MEID) should appear on your screen. You may need to hit the call button on some phone models.
- Some Android devices instead have an advertising ID that can be found in Settings > Google > Ads, though some Android software versions may differ slightly. A device’s advertising IDs vary in size but are typically either 16 or 32 characters and are a mix of letters and numbers.
If you have reset or deleted, or if your advertising ID has otherwise changed since the spyware was installed, this tool may not identify your device as compromised.
If the spyware lookup tool returns a “match,” it means that IMEI number or device advertising ID was found in the leaked lists, and the corresponding device was compromised by one of TheTruthSpy spyware apps during or prior to December 2023.
If you get a “likely match,” it means your IMEI number or device advertising ID partially matched a record in the leaked lists but it may have contained extraneous data, such as the name of the device’s manufacturer. This result means the corresponding device was probably compromised by one of TheTruthSpy apps but that you must confirm by checking for signs that the spyware is installed.
If “no match” is found, it means there is no record matching that device in the leaked lists of compromised devices. This does not automatically mean the device is free from spyware. Your device may have been compromised after December 2023, or may have been targeted by another kind of spyware.
My phone was compromised. What do I do now?
To confirm if an Android device is currently compromised, you must look for signs that the spyware is installed. This guide explains how to search for evidence that your Android device was compromised by spyware and how to remove it from your phone.
Because the spyware is designed to be stealthy, please keep in mind that removing the spyware will likely alert the person who planted it. This could lead to an unsafe situation. The Coalition Against Stalkerware and the National Network to End Domestic Violence offer support, guidance, and resources on how to create a safety plan.
TheTruthSpy lookup tool FAQ:
What does this spyware lookup tool do?
This spyware lookup tool allows you to check if your Android device was compromised by any of TheTruthSpy apps.
TechCrunch has obtained leaked lists containing the IMEI number or the unique device advertising ID collected from every device compromised by TheTruthSpy prior to and including December 2023.
Every cellular-connected phone or tablet has a unique IMEI number hardcoded into the device’s hardware, while advertising IDs are baked into the device’s software and can be easily reset and changed by the user. Once the spyware is planted, the spyware sends one of the phone’s identifiers back to its servers.
TechCrunch verified the authenticity of the leaked lists by matching known IMEIs from burner and virtual devices TechCrunch used as part of our investigation into the spyware network
This spyware lookup tool does not store submitted IMEI numbers or advertising IDs.
Why did TechCrunch build a spyware lookup tool?
The leaked lists of devices compromised by TheTruthSpy does not contain enough information for TechCrunch to personally identify or notify individual device owners. Even if it did, we couldn’t contact victims without also potentially notifying the person who planted the spyware and creating a dangerous situation.
A phone can store some of a person’s most personal and sensitive information. No member of civil society should ever be subject to such invasive surveillance without their knowledge. By offering this tool, anyone can check if TheTruthSpy spyware compromised their Android device at a safe time and place of their choosing
The spyware lookup tool cannot tell you if your device is currently compromised. It can only tell you if there is a match for a device identifier found in the leaked list, indicating that device was likely compromised some time during or before December 2023.
What can this spyware do?
Consumer-grade spyware apps are often promoted as child monitoring apps, but these apps also go by the name “stalkerware” or “spouseware” for their ability to track and monitor other people, like spouses and domestic partners, without their consent.
Apps like TheTruthSpy are downloaded and installed by someone with physical access to a person’s phone and are designed to stay hidden from home screens, but will silently and continually upload call logs, text messages, photos, browsing histories, call recordings and real-time location data to a dashboard viewable by the abuser.
TheTruthSpy has victims in virtually every country, with large clusters in Europe, India, Indonesia, the U.S. and the United Kingdom. Most victims will have no idea that their device has been compromised.
What is the security vulnerability?
At least nine known near-identical spyware apps in TheTruthSpy’s network — some now defunct — that share and communicate with the same server infrastructure, and therefore the same security vulnerability.
Those apps include Copy9, MxSpy, iSpyoo, SecondClone, TheSpyApp, ExactSpy, GuestSpy and FoneTracker. Other than their names, these apps are identical to TheTruthSpy.
The security vulnerability, known officially as CVE-2022-0732, is simple to abuse and exploit, allowing anyone to remotely download the contents of a victim’s device data.
With no expectation that the vulnerability would be fixed, TechCrunch published details about the spyware operators, as well as resources for victims to identify and remove the spyware — if it is safe to do so.
The legal stuff
If you use this spyware lookup tool, TechCrunch will collect your IMEI number or advertising ID and your IP address for the sole purpose of helping you identify if your device was compromised by this spyware. IMEI numbers and advertising IDs are not stored, sold, or shared with any third-parties and are deleted once you receive the spyware lookup tool results. IP addresses are briefly stored to limit automated requests only. TechCrunch is not liable for any loss or damage to your device or data and offers no guarantees about the accuracy of the results. You use this tool at your own risk.
First published August 17, 2022 and updated February 12, 2024.
Read more on TechCrunch:
- Behind the stalkerware network spilling the private phone data of hundreds of thousands
- Inside TheTruthSpy, the stalkerware network spying on thousands
- Fake passports, real bank accounts: How TheTruthSpy stalkerware made its millions
- Your Android phone could have stalkerware, here’s how to remove it
Cybersecurity 101: