Buy now, pay later (BNPL) is booming in popularity, particularly among the traditional credit-wary millennial and Gen Z consumer populations. With $680 billion in transaction volume by 2025 up for grabs, fintech startups and long-standing financial institutions alike are jumping into the mix with their own offerings.
But, as we’ve seen with other emerging tech trends, rapid growth leads to new challenges.
While many industry pundits would point to the recent Consumer Financial Protection Bureau (CFPB) probe into BNPL vendors as the sector’s biggest headwind, there’s another area that regulators and industry players should be concerned about: fraud. Cybercrime often acts as a barometer of economic trends, and as the BNPL market continues to soar, fraudsters are cashing in.
Rather than relegating their activities to dark web marketplaces, scammers are hiding in plain sight on encrypted messaging apps. They collaborate through publicly available forums on these platforms to target BNPL providers with new tactics.
The only way to get ahead of these scams is for BNPL vendors to ensure they have the right defense strategy in place to combat fraud on their own platforms and networks.
Payment fraud is going mainstream, and anyone with an internet connection can join in. Yet, rather than hoping that platforms remove these fraud forums from their services, BNPL providers and the merchants who use them can shore up their own properties by understanding exactly how they are at risk.
So, what do these new fraud methods look like, and how can providers protect against them? Let’s dive in.
The dark web versus the deep web: The rise of fraud as a service
The dark web has, for years, been home to cybercrime and has become an oasis for scammers looking to obtain compromised information. However, with the recent crackdown on dark web marketplaces, cybercriminals have turned to new and under-the-radar hubs to commit illegal activity.
Malign actors have set their sights on secure messaging apps, such as Telegram, to conduct their illegal activity. As a part of the deep web, which isn’t indexed by search engines, secure messaging apps are a haven for professional criminals hoping to remain anonymous.
Within these forums, fraudsters have evolved their attack strategies. Instead of solely buying and selling access to information, cybercriminals have begun to promote fraud as a service.
One example is a Telegram scheme in which cybercriminals steal from restaurants and food delivery services. By advertising their ability to purchase food and beverage orders with stolen information (e.g., log-in credentials or credit card numbers), they offer opportunistic diners a meal at a heavily discounted rate.
The cybercriminal receives payment from the would-be diner in cryptocurrency, then uses stolen credit card details or hacked accounts to purchase the meal and have it delivered to the diner’s location.
The danger of these scams is that they’re not limited to Telegram and are easy to replicate. Encrypted apps give scammers a secure platform to advertise their access to stolen information. From offering fake COVID-19 vaccine cards to sharing tactics for bypassing know your customer (KYC) verifications on crypto exchanges, fraudsters are able to cash in on any market by providing fraud-as-a-service schemes on encrypted platforms.
Risks to the BNPL sector
With the success scammers have had with encrypted apps, it’s only natural that they have turned their sights toward BNPL providers. Cybercriminals advertise their scams on top Telegram fraud forums, which can have anywhere from 3,000 to 125,000 subscribers.
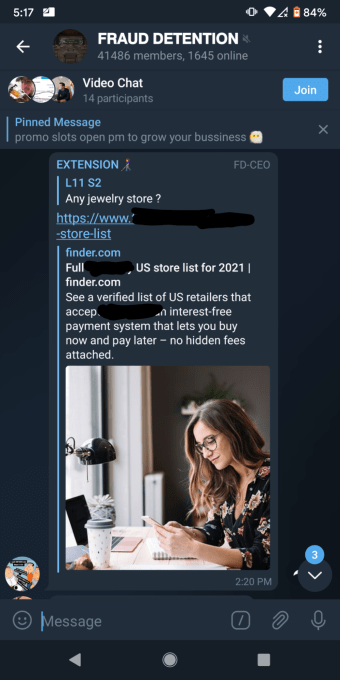
Image Credits: Brittany Allen
Such schemes are made possible by the access malign actors have to two main types of stolen information: user credentials and dead credit cards. Illegally obtained credential scams look similar to the image on the right, which shows a malign actor providing a list of U.S. retailers that can be targeted by using stolen accounts.
These agents offer access to different types of stolen information, such as user accounts on retailer websites, BNPL providers, as well as email details.
In many cases, they sell access to BNPL accounts associated with dormant Yahoo and AOL email addresses. Using these accounts, individuals can make BNPL purchases with no intention of ever paying for the transaction, leaving either the real account owner or the BNPL provider to foot the bill.
Another common BNPL scam involves the sale of dead credit card numbers obtained on the dark web, via data breaches or a privacy-focused messaging app’s fraud forum. Once an individual purchases the information, they can use it to make fraudulent BNPL purchases that they know will later fail because the credit card number is no longer valid.
This scheme is commonly leveraged against BNPL providers that do not immediately collect the first installment payment or those that have suboptimal authorization flows. However, once the credit card is approved for the transaction, it no longer becomes the purchaser’s problem. Instead, when the retailer or BNPL service provider is unable to process the credit card, they must take the loss.
Protecting against the attacks
Unfortunately, it’s nearly impossible to shut down this type of fraud activity on encrypted messaging forums. While it seems that Telegram is aware of these groups — as there have been a handful of instances where a fraudulent group was removed — it’s not enough to stop this activity. As soon as one group is shut down, another one is created in a never-ending cycle of illegal information sharing.
The only way to get ahead of these scams is for BNPL vendors to ensure they have the right defense strategy in place to combat fraud on their own platforms and networks. The challenge is that vendors are dealing with a rapid increase in transaction volume, so the ability to scale their fraud prevention efforts is critical.
This is where automation can play a key role. Many anti-fraud teams are under-resourced and don’t have the ability to analyze each transaction made on their platform. By pairing automation with vast amounts of data, systems can analyze thousands of different signals on purchases in real time.
Once a suspicious transaction is identified, such as an account using a new shipping address or a different credit card, it can flag the purchase to the fraud team before it is processed. This gives fraud teams the ability to analyze only suspicious orders without having to sort through every single purchase.
What’s ahead for the BNPL market
As the BNPL market handles the CFPB probe, it will be imperative for providers to focus on stopping the fraud happening across their platforms. A single brush with fraud can turn consumers toward a competing business, so it will be the vendors that are able to effectively address fraud attacks that will end up on top.
Luckily for the BNPL sector, the rise of fraud in a trending market isn’t something new. The first step for vendors is being aware that it is happening on their platform and understanding how to stop it.
