A 17-year-old Florida teenager is accused of perpetrating one of the year’s biggest and most high-profile hacks: Twitter.
A federal 30-count indictment filed in Tampa said Graham Ivan Clark used a phone spearphishing attack to pivot through multiple layers of Twitter’s security and bypassed its two-factor authentication to gain access to an internal “admin” tool that let the hacker take over any account. With two accomplices named in a separate federal indictment, Clark — who went by the online handle “Kirk” — allegedly used the tool to hijack the accounts of dozens of celebrities and public figures, including Bill Gates, Elon Musk and former president Barack Obama, to post a cryptocurrency scam netting over $100,000 in bitcoin in just a few hours.
It was, by all accounts, a sophisticated attack that required technical skills and an ability to trick and deceive to pull off the scam. Some security professionals were impressed, comparing the attack to one that had the finesse and professionalism of a well-resourced nation-state attacker.
But a profile in The New York Times describes Clark was an “adept scammer with an explosive temper.”
In the teenager’s defense, the attack could have been much worse. Instead of pushing a scam that promised to “double your money,” Clark and his compatriots could have wreaked havoc. In 2013, hackers hijacked the Associated Press’ Twitter account and tweeted a fake bomb attack on the White House, sending the markets plummeting — only to quickly recover after the all-clear was given.
But with control of some of the world’s most popular Twitter accounts, Clark was for a few hours in July one of the most powerful people in the world. If found guilty, the teenager could spend his better years behind bars.
Here’s more from the past week.
THE BIG PICTURE
Garmin hobbles back after ransomware attack, but questions remain
After reporting an “outage” for the best part of a week, Garmin eventually admitted it had been hit by a ransomware attack. Reporting had already confirmed the attack. Garmin’s internet services eventually got back on their feet after the five-day outage, but users were still livid at the lack of communication.
But how Garmin got its systems back remains a mystery — one that could be probed by federal investigators.
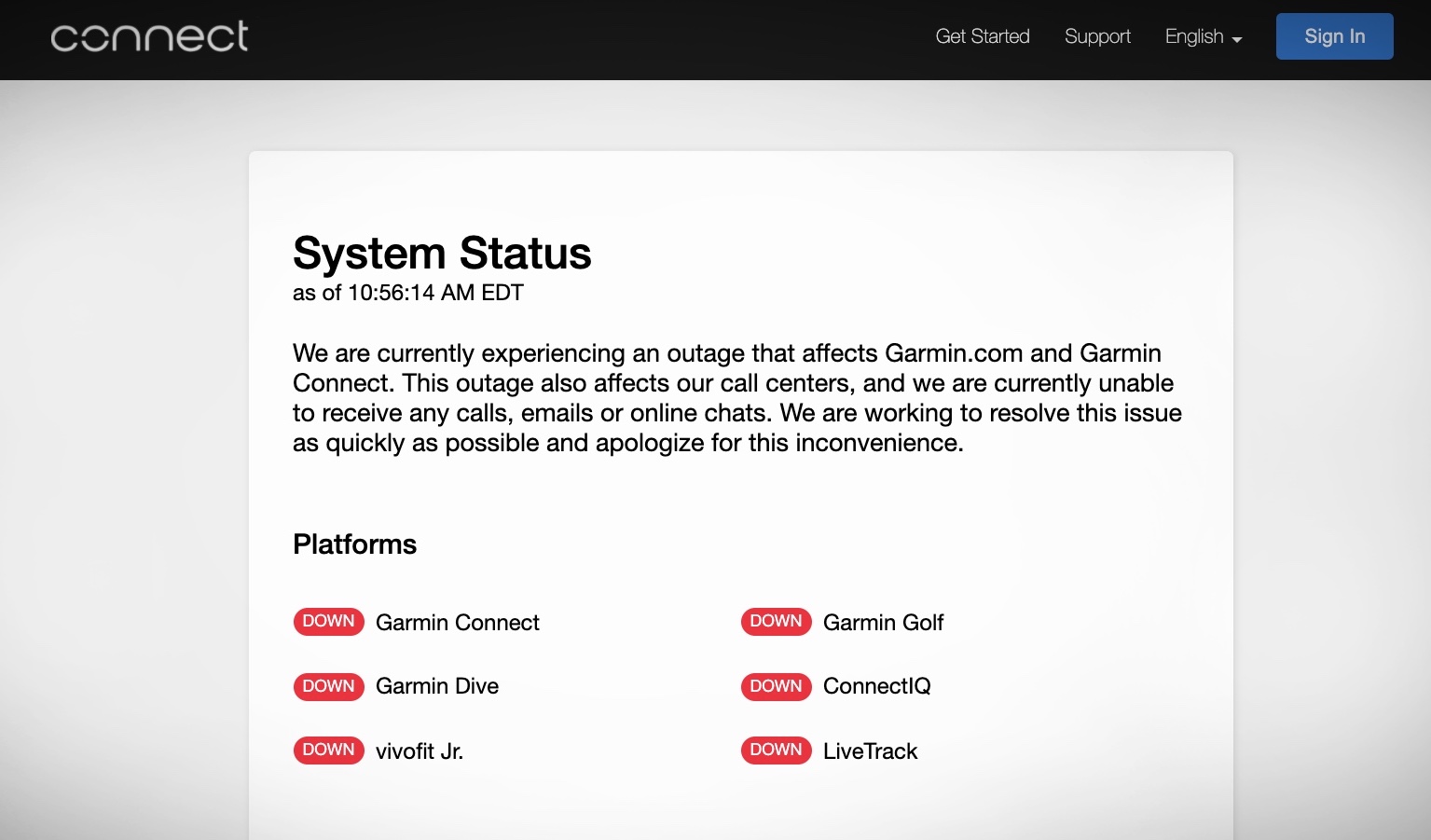
Garmin’s online services were down for five days following a ransomware attack. (Image: TechCrunch)
Reports confirmed the file-encrypting malware used in the attack was WastedLocker, a ransomware with ties to Russian hacking group Evil Corp. But here’s the tricky bit: Last year, the U.S. Treasury indicted its alleged head and imposed sanctions on the group, effectively making it illegal for any company infected by an Evil Corp ransomware attack to pay the ransom — even if they wanted to.
One news report said Garmin obtained the decryption key, perhaps through an intermediary. That ties in with what one source told TechCrunch prior to the company’s recovery. Garmin didn’t comment beyond its statement. But no doubt, the government will want to know how Garmin got its systems back.
Dragnet location warrants are on the rise, as is the scrutiny
An increasingly popular way for law enforcement to home in on criminal suspects using their location data is set to face scrutiny for the first time.
Say police are looking for a criminal suspect in a particular area at a certain time and day. Police can use these so-called “reverse-location” warrants to demand companies that collect tons of location data, like Google and Facebook, to turn over data on anyone who was nearby at the time. That arguably helps to narrow the search for their suspect, assuming they weren’t smart enough to leave their phone at home.
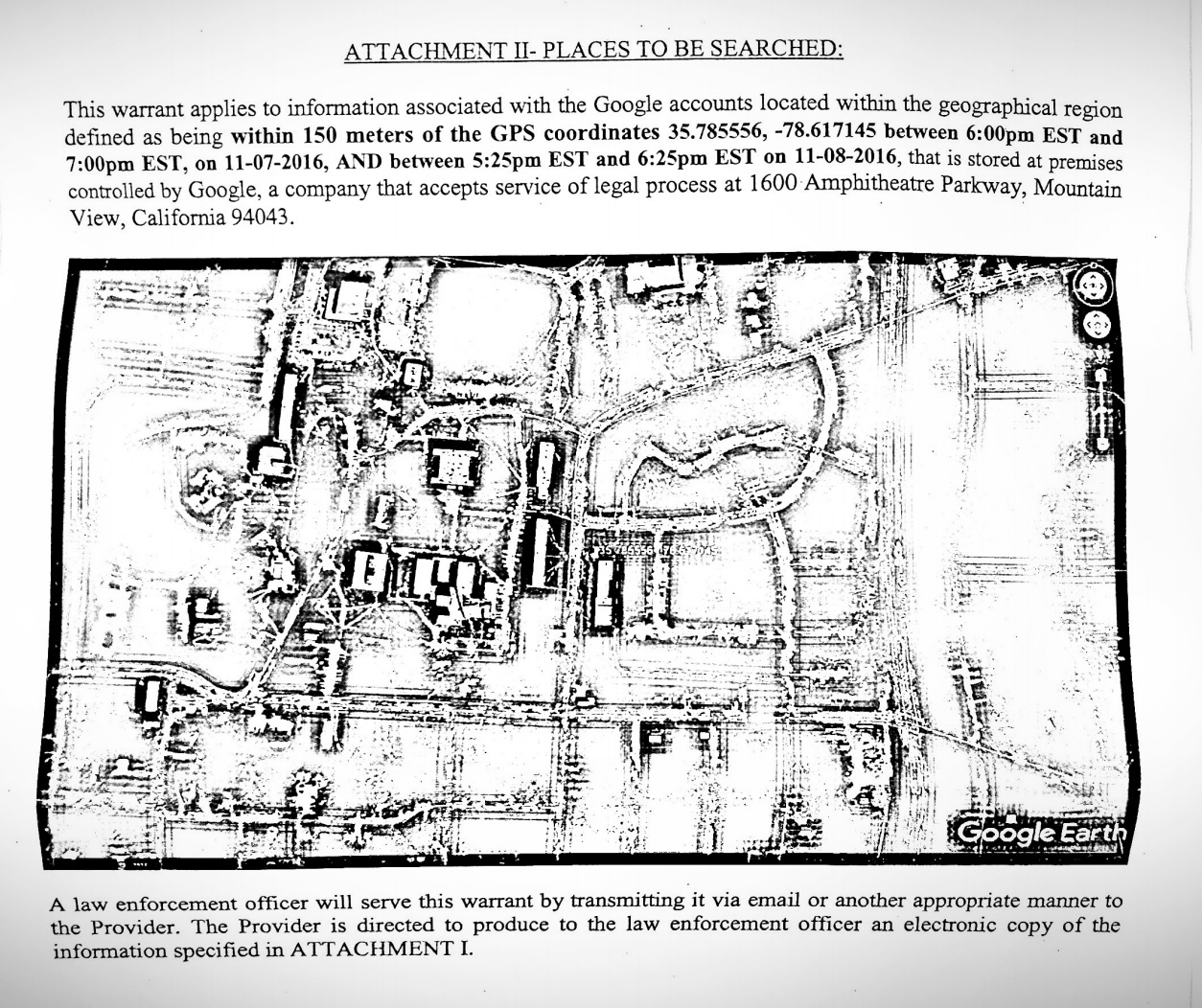
A reverse-location data warrant. (Image: TechCrunch)
But these warrants are executed often at the expense of invading the privacy of innocent people caught up in the data dragnet. In some cases, this can involve hundreds — or even thousands of phones. Police are using these warrants more frequently: The Wall Street Journal reports that these warrant demands spiked 1,500% between 2017 and 2018, and another 500% from 2018 to 2019.
Privacy advocates have long questioned the validity of these warrants, but now two criminal defendants in Virginia and San Francisco are challenging the legal basis behind reverse-location warrants and New York lawmakers are pushing to end the practice. Could reverse-location warrants soon be a thing of the past?
MOVERS AND SHAKERS
Last week saw the heads of Apple, Amazon, Facebook and Google defend their dominant market positions by claiming that, for the most part, everything was fine and that they aren’t too big or powerful.
It wasn’t an argument that convinced one Democratic lawmaker, who honed in on Google’s Sundar Pichai, taking issue with how the company reneged on a promise not to merge its massive bank of advertising data it obtained through its 2007 acquisition of DoubleClick with Google’s own account data. A decade later, in 2016, Google merged its ad data with user account data — a move likely authorized by Pichai himself.
Rep. Val Demings slammed Google for “effectively destroying anonymity on the internet.” Demings blasted the move to combine users’ search and browsing history with location data and information from Gmail inboxes as “absolutely staggering.”
Demings was one of several lawmakers grilling the tech giants as part of the House’s investigation into possible violations of antitrust law. Privacy and security were big talking points during the hearings.
$ECURITY $TARTUPS
And before we sign off, here’s a quick look at the security startup world over the past week.
Cybersecurity training provider Offensive Security has acquired VulnHub, an open-source catalog of technology that’s legally breakable and hackable, allowing hackers and security researchers to get safe, hands-on experience with penetration testing. OffSec also provides a number of open-source tools, like Kali Linux, a distribution of Linux designed for helping ethical hackers run penetration tests; and Exploit-DB, a massive repository of known exploits that are popular with security professionals.
Stack Overflow, a forum and community for developers, has raised $85 million in its latest Series E round, announced at the end of July. The round was led by Singapore-based global investment firm GIC and had participation from Andreessen Horowitz, Index Ventures and others.
Ermetic, a cloud security startup, snapped up $17 million in its Series A, led by Accel and others. Ermetic helps companies that rely on cloud infrastructure, like Amazon Web Services, Google Cloud and Microsoft Azure, enforce tighter and stricter permissions, reducing the risk of data breaches or exposures — at least, in theory.
And, we wrote about Butlr last week, a home and retail automation startup that makes privacy-friendly sensors that pivoted during the pandemic to help stores reopen while complying with maximum occupancy rules and queue management. The aim is to help prevent the spread of coronavirus. But because the sensors only detect body heat, they can’t tell who you are — only where you are. You can read our story here.
Send tips securely over Signal and WhatsApp to +1 646-755-8849.