As the world looks to reopen after weeks of lockdown, governments are turning to contact tracing to understand the spread of the deadly coronavirus.
Most nations are leaning toward privacy-focused apps that use Bluetooth signals to create an anonymous profile of where a person has been and when. Some, like Israel, are bucking the trend and are using location and cell phone data to track the spread, prompting privacy concerns.
Some of the biggest European economies — Germany, Italy, Switzerland and Ireland — are building apps that work with Apple and Google’s contact-tracing API. But the U.K., one of the worst-hit nations in Europe, is going it alone.
Unsurprisingly, critics have both security and privacy concerns, so much so that the U.K. may end up switching over to Apple and Google’s system anyway. Given that one of Israel’s contact-tracing systems was found on an passwordless server this week, and India denied a privacy issue in its contact-tracing app, there’s not much wiggle-room to get these things wrong.
Turns out that even during a pandemic, people still care about their privacy.
Here’s more from the week.
THE BIG PICTURE
Zoom acquires Keybase, but questions remain
When Zoom announced it acquired online encryption key startup Keybase, for many, the reaction was closer to mild than wild. Even Keybase, a service that lets users store and manage their encryption keys, acknowledged its uncertain future. “Keybase’s future is in Zoom’s hands, and we’ll see where that takes us,” the company wrote in a blog post. Terms of the deal were not disclosed.
Zoom has faced security snafu after snafu. But after dancing around the problems, it promised to call in the cavalry and double down on fixing its encryption. So far, so good. But where does Keybase, largely a consumer product, fit into the fray? It doesn’t sound like even Zoom knows yet, per enterprise reporter Ron Miller. What’s clear is that Zoom needs encryption help, and few have the technical chops to pull that off.
Keybase’s team might — might — just help Zoom make good on its security promises.
WeChat, but they watch
Citizen Lab, a unit inside the University of Toronto that studies surveillance and threats to human rights, says WeChat is “invisibly” training its censorship system for users in China by snooping on files sent by foreign users.
WeChat is owned by internet giant Tencent and has over a billion users globally, making it one of the world’s most popular messaging apps. China’s political censorship laws have become stricter as internet usage surged and the nation remains one of the toughest, most oppressive regimes for free speech.
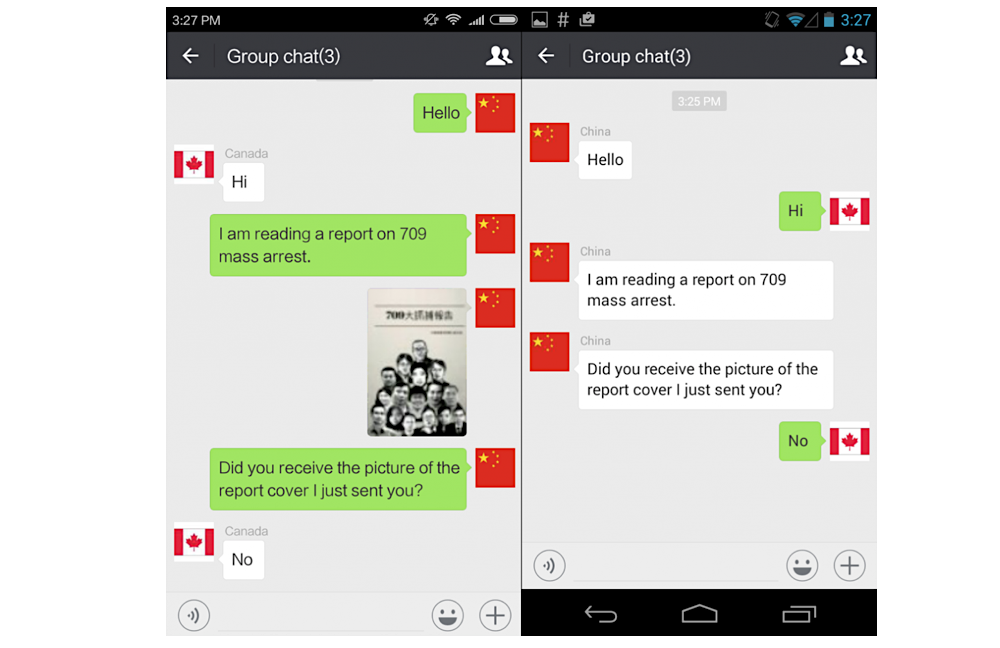
WeChat censoring images on users in China (Image: Citizen Lab)
Researchers found that WeChat creates a unique digital “fingerprint” for images and documents sent over the messaging app. These fingerprints are matched against a database of censored content. After running several experiments, researchers found that if there was a match, a WeChat user in China would not see the flagged content.
Despite the aggressively anti-free speech regime, Citizen Lab said that there is “no evidence” to show that Tencent’s surveillance is enforced by Beijing.
Europe’s largest hospital hit by ransomware
Many of the newer data-stealing ransomware groups promised to temporarily cease targeting hospitals and medical facilities. After all, we are still in the throes of a global pandemic, and hackers are human too.
But not every ransomware group is playing ball. One such group, Snake, targeted Europe’s largest private hospital systems this week, reports security journalist Brian Krebs. Snake not only infects systems with file-encrypting malware, it also exfiltrates the data. If the victim fails to pay up, the group publishes their files online.
Krebs said, citing a source, that the Snake ransomware group hit “every part of [Fresenius’] operations around the globe.”
MOVERS AND SHAKERS
“Not securing a server would be an embarrassment for a school project. For a billion-dollar company to not password-protect a secretive project that hopes to handle location and health data suggests a quick and sloppy roll out.”
That’s John Scott-Railton, a senior researcher at the Citizen Lab, part of the Munk School at the University of Toronto. We spoke to Scott-Railton this week for our exclusive story mentioned earlier — the discovery of a passwordless server belonging to spyware firm NSO Group. The system, codenamed Fleming, is designed to use cell location data to pinpoint potential COVID-19 infections. NSO called it a “demo” system and denied it used real location data in the system. Scott-Railton disagreed.
Experts also say that location data isn’t accurate enough for contact tracing, rendering the system largely redundant in any case.
$ECURITY $TARTUPS
In startup news this week, Microsoft is said to be eyeing Israeli cybersecurity startup CyberX, according to Israeli newspaper Haaretz. The software giant is expected to pay $165 million for the company, which specializes in Internet of Things security. Since its founding in 2013, CyberX has raised $48 million and is valued at about $110 million. A deal could be announced as soon as Monday.
Dtex, a cybersecurity firm specializing in spotting and mitigating insider threats, has raised $17.5 million. Before this raise, it took in as much as $57.5 million in funding.
Another Israeli startup, Orca, landed $20.5 million in its Series A raise for its “agentless” cloud security platform.
And BlackCloak, a corporate executive security startup, raised $1.9 million. While it may pale compared to some fundraise rounds, it’s an interesting and largely underserved part of the cybersecurity arena. Hackers are increasingly targeting corporate executives through their personal devices and home networks. There was no bigger target than Amazon CEO Jeff Bezos, targeted last year allegedly by the Saudi regime.
Send tips securely over Signal and WhatsApp to +1 646-755-8849.