A massive database storing millions of credit card transactions has been secured after spending close to three weeks exposed publicly to the internet.
The database belongs to Paay, a card payments processor based in New York. Like other payment processors, the company verifies payments on behalf of selling merchants, like online stores and other businesses, to prevent fraudulent transactions.
But because there was no password on the server, anyone could access the data inside.
Security researcher Anurag Sen found the database. He told TechCrunch that he estimates there are about 2.5 million card transaction records in the database. After TechCrunch contacted the company on his behalf, the database was pulled offline.
“On April 3, we spun up a new instance on a service we are currently in the process of deprecating,” said Paay co-founder Yitz Mendlowitz. “An error was made that left that database exposed without a password.”
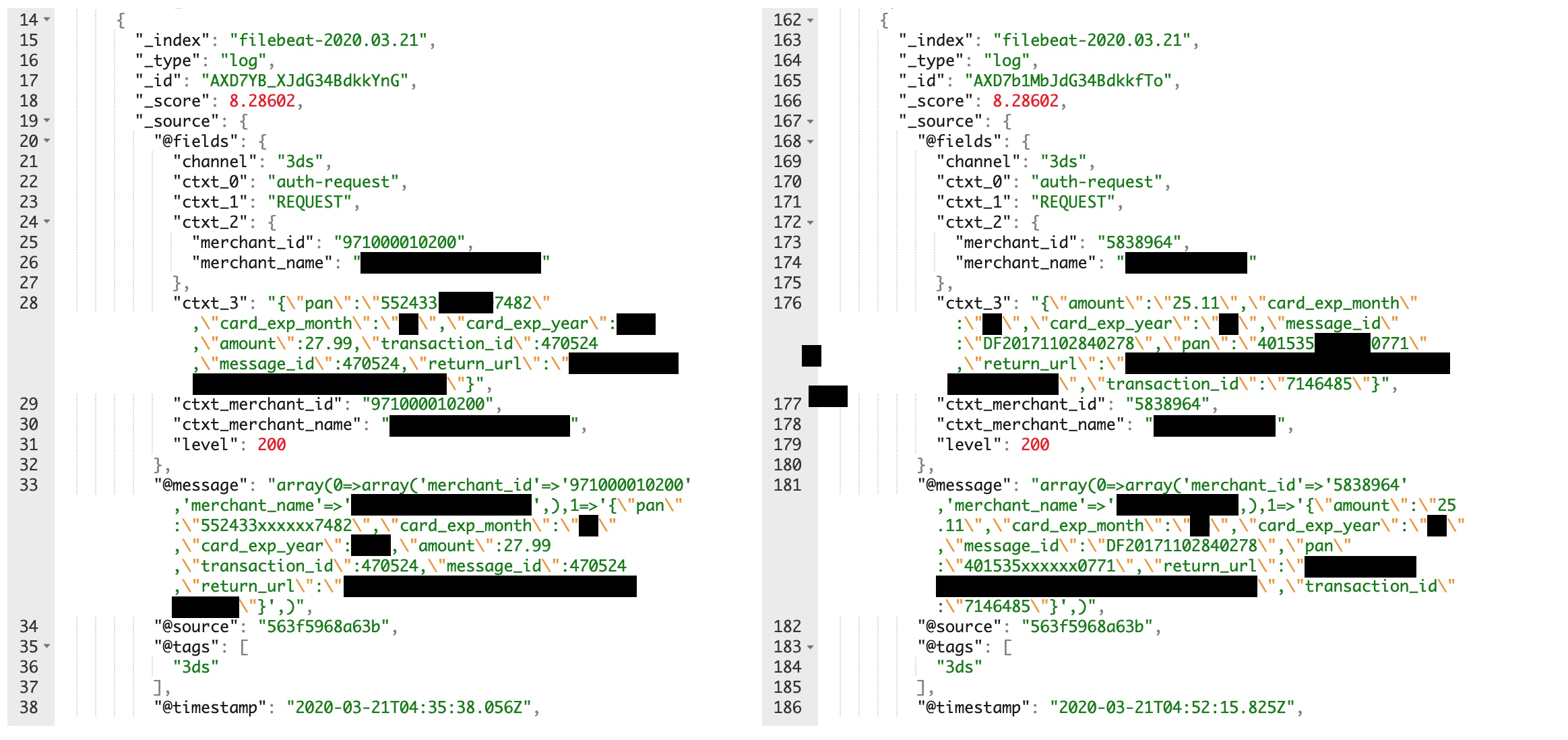
Two records from the exposed database. TechCrunch has blacked out the full credit card number in the record to prevent fraud.
The database contained daily records of card transactions dating back to September 1, 2019 from a number of merchants. TechCrunch reviewed a portion of the data. Each transaction contained the full plaintext credit card number, expiry date and the amount spent. The records also contained a partially masked copy of each credit card number. The data did not include cardholder names or card verification values, making it more difficult to use the credit card for fraud.
Mendlowitz disputed the findings. “We don’t store card numbers, as we have no use for them.” TechCrunch sent him a portion of the data showing card numbers in plaintext, but he did not respond to our follow-up.
It’s the third payments processor this year to admit a security lapse. In January, Sen found another payments processor with an exposed database storing 6.7 million records. Earlier this month, another researcher found two payment sites for paying court fines and utilities also left a cache of data exposed for several months.
Mendlowitz said the company was informing between 15 and 20 merchants, and that the company has engaged an unnamed forensic auditor to understand the scope of the security lapse.
