A Washington state internet provider left an unprotected server online without a password, exposing network schematics, passwords and other sensitive files for at least six months.
Worse, it took the company a week to shut off the leak, despite several phone calls and emails warning of the exposure.
The little-known internet provider, PocketiNet, may not be widely known outside the west coast but it’s a local powerhouse — providing high speed internet access to thousands of homes, local multi-national corporations, hospitals and a regional airport across the state. But the company put its customers and its network at risk after it left open an Amazon S3 storage bucket — an all too common cause of data exposures — containing tens of gigabytes of files.
Chris Vickery, director of cyber risk research at security firm UpGuard, found the data and shared his findings with TechCrunch. He described the cache the “keys to the kingdom.”
Among the files, the bucket contained detailed diagrams of the company’s network setup, router configurations, and details and locations of customers’ equipment.
Vickery also found spreadsheets and plaintext password files belonging to employees and network devices — like firewalls, switches and wireless points — that he said could have given a hacker “everything they need to disrupt, exploit, or otherwise modify network operations.”
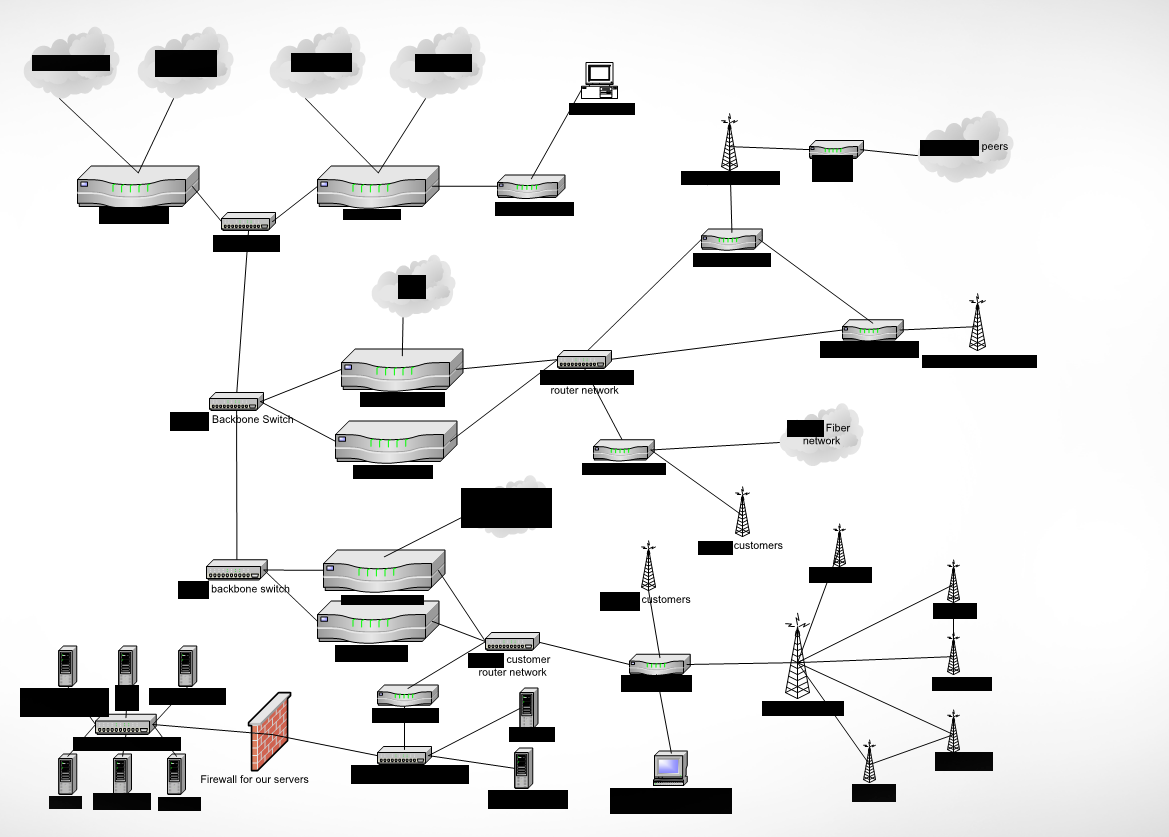
A redacted network schematic from the exposed Amazon S3 bucket (Image: supplied)
Although there wasn’t any customer data stored in the bucket, one file revealed PocketiNet’s “priority” customers, including the nearby Lourdes Medical Center in Pasco, the Toyota Center arena in Kennewick, and a little-known Lockheed Martin facility in Richand. The company provides service to dozens of hotspots around the region, including at the the Tri-City Airport in Pasco. It also provides hotspots and backend network infrastructure to Walla Walla Regional Airport.
As soon as Vickery found the data on October 11, he contacted the company the same day. But the company took its time to close the bucket.
In a phone call on Saturday, PocketiNet’s chief technology officer Steve Hoffman told TechCrunch that the bucket had been open for “six months” and that following an unrelated power outage on the network, securing the bucket “can wait another day.” That’s contrary to his an email the day before, claiming that the bucket had been secured “days ago,” which it wasn’t.
A day later, Vickery confirmed that the bucket was secured.
We reached out to the company again for comment. Chief executive Todd Brandenberg responded past our deadline, confirming the breach.
“Most of this data was out of date,” he said in an email. “We appreciate being alerting us to this error. PocketiNet is currently conducting a comprehensive network review to guarantee no additional data is compromised. We have also begun a complete analysis of operating procedures to ensure no future errors occur.”
Vickery said the data should not have been public and could have put the company’s network at risk of exploitation or compromise. Homeland Security already considers internet providers “critical infrastructure.” But while so many companies today are looking for foreign threats and complex adversaries, some might want to look a little closer to home.
