The U.S. Government has officially blamed North Korea for WannaCry, the massive ransomware attacked that spread across the world disrupting more than 200,000 businesses from 35 countries this past May.
Writing in the New York Times [link subject to a paywall], Homeland Security Advisor Thomas P. Bossert said for the first time that the North Korean regime is directly to blame for the chaos, which is said to have crippled parts of the UK’s National Health Service among other targets.
“It encrypted and rendered useless hundreds of thousands of computers in hospitals, schools, businesses and homes. While victims received ransom demands, paying did not unlock their computers. It was cowardly, costly and careless. The attack was widespread and cost billions, and North Korea is directly responsible,” Bossert wrote.
Researchers began to suspect North Korea’s involvement in the aftermath of the attack, which utilized an exploit that was stolen from the NSA, after dotting links with a 2014 attack on Sony that was widely through to have originated from the country after it objected to ‘The Interview.’ Recently, the UK government and Microsoft both pointed the finger at Pyongyang.
“I think at this point that all observers in the know have concluded that WannaCry was caused by North Korea using cyber tools or weapons that were stolen from the National Security Agency in the United States,” Microsoft president and chief counsel Brad Smith told British broadcaster ITV in October.
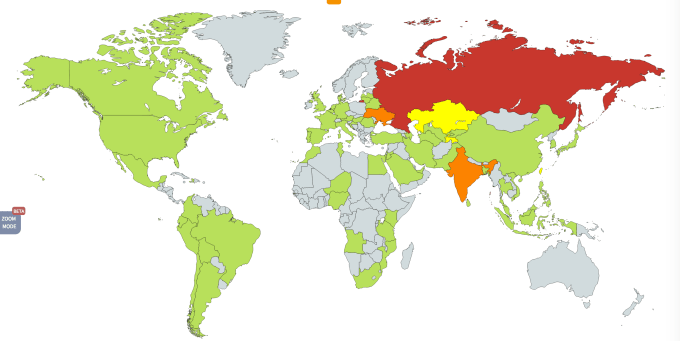
A heat map showing the initial impact of WannaCry in May 2017
Bossert, who called the WannaCry attack “indiscriminately reckless,” said President Trump’s administration is in the process of fortifying U.S. cyber defenses but it will also lead action to bring North Korea to justice for the virus.
“We call on the private sector to increase its accountability in the cyber realm by taking actions that deny North Korea and other bad actors the ability to launch reckless and destructive cyberattacks. We applaud Microsoft and others for acting on their own initiative last week, without any direction or participation by the U.S., to disrupt the activities of North Korean hackers,” he wrote.
Beyond WannaCry, the U.S. government is investigating allegations that actors linked to the Russian government interfered with last year’s Presidential election. Twitter and Facebook have provided evidence to Congress and the House, while both have introduced new standards aimed at preventing a repeat in the future.
Just last week, the Trump administration signed a bill that bans the federal government from using products from Kaspersky due to “the grave risk that [its software] poses to our national security.”
The company recently announced that it would close its Washington, D.C. offices, which it stated were “no longer viable.”
One thing that has been consistent from researchers is that North Korea’s cyber army is seen as being more sophisticated than was previously thought. Other targets of the country have included bitcoin exchanges in South Korea. Cybersecurity firm FireEye claims to have tracked at least five attacks on bitcoin exchanges, or individual bitcoin wallets, within the past six months.
“It should be no surprise that cryptocurrencies, as an emerging asset class, are becoming a target of interest by a regime that operates in many ways like a criminal enterprise. While at present North Korea is somewhat distinctive in both their willingness to engage in financial crime and their possession of cyber espionage capabilities, the uniqueness of this combination will likely not last long-term as rising cyber powers may see similar potential,” FireEye concluded.
The bitcoin link is also relevant with WannaCry, which demanded ransoms to be paid using the cryptocurrency.
