We’ve mostly moved past the point where our Internet of Things devices leak private information to anyone watching via unsecured connections, but that doesn’t mean you can stop being afraid. Never, ever stop being afraid. To top up your paranoia reserves, a new study finds that internet providers can, if they so choose, monitor all kinds of things from your smart home’s traitorous metadata.
The paper, from a team at Princeton’s computer science school led by grad student Noah Apthorpe, gets straight to the point: “we demonstrate that an ISP or other network observer can infer privacy sensitive in-home activities by analyzing internet traffic from smart homes containing commercially available IoT devices even when the devices use encryption.”
It’s a pretty straightforward attack: the IoT devices often identify themselves voluntarily, usually by connecting to specific domains or URLs. Even if they didn’t, there are simple ways of profiling them based on observation and some known data. The researchers demonstrated this by showing that various devices show distinct patterns of data transmission:
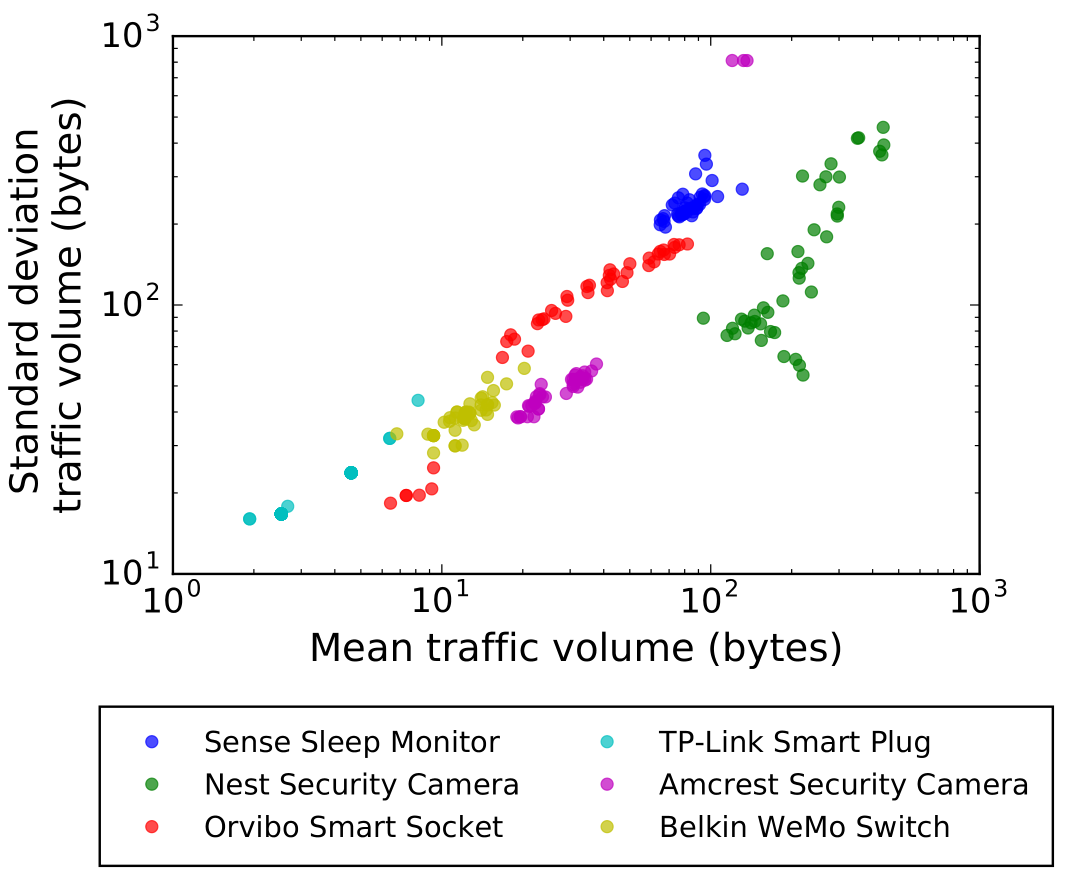 Once they’re identified, the ISP (in this case played by the researchers) can simply watch for increases in traffic. What those changes in traffic mean are either self-evident or perfectly able to be inferred with a little analysis.
Once they’re identified, the ISP (in this case played by the researchers) can simply watch for increases in traffic. What those changes in traffic mean are either self-evident or perfectly able to be inferred with a little analysis.
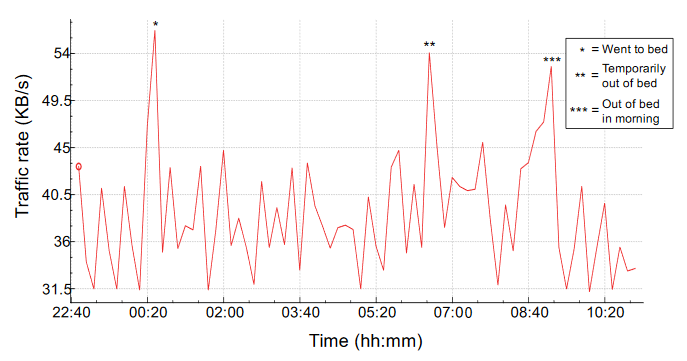
By watching a sleep tracker, the ISP can see when the user gets in bed and wakes up, perhaps even how well they sleep, whether they get up in the middle of the night and so on.
 By watching various smart switches, the ISP can see when certain devices are in use: the TV, the space heater, the light in the basement, the garage door.
By watching various smart switches, the ISP can see when certain devices are in use: the TV, the space heater, the light in the basement, the garage door.
By watching the IP security camera traffic, the ISP can see when the camera detects motion, when the user is tuned in to watch their home from afar or when they check archived footage.
And if a handful of academics can do it, you better believe a major ISP could — though of course they’ll tell you they won’t. Doesn’t matter, they can collect this stuff and sell it without telling you, since Congress zapped the FCC’s privacy protections. The researchers note this in the paper, in fact.
But don’t worry, there’s actually a pretty good solution! The team found that by transmitting the IoT data through a central hub (e.g. a router with a little custom software), they could effectively camouflage it by transmitting a trickle of junk data at all times. This traffic shaping, as it’s called, doesn’t prevent the devices from working (many of them worked surprisingly well with artificially slowed connections), but it does make it hard for an attacker to tell signal from noise.
They suggest a constant stream of around 40 KB/s should be more than enough, though that adds up over time to over a hundred gigabytes — not something everyone can afford, depending on data caps. But that system could easily be improved or made more amenable to people with limited bandwidth.
The full paper is quite readable and is available here.