Winter is coming to the icy land of IT departments. Ferocious cyberattacks against corporate IT infrastructures are proliferating, and it seems like every day we hear about another company experiencing a critical data breach. Sometimes those leaks are minor, but other times, the leaks are an entire company’s email archive.
The threat environment for IT systems has arguably never been worse, and yet, the defenses needed to protect this critical infrastructure have never been more porous. Rapid change in these systems – at both the infrastructure and application layers – have meant that IT staffers have been racing to try to keep their systems secure against challenging odds. Many have failed.
Skyport Systems, a Mountain View-based security startup that last month raised a $30 million Series B round from Sutter Hill, Intel Capital, and Index Ventures, is publicly launching what it believes to be the future of security: a system for completely trusted computing.
Trust But Verify
Now, if you aren’t immediately skeptical when hearing that a security product is going to be impervious to attacks, you are not doing your job as a security professional. If real life (and Hollywood!) have taught us anything, it is that the bad guys always have another trick up their sleeves.
This time, though, their bag of tricks might finally be empty. Skyport’s product, dubbed the SkySecure System, is designed to enforce policies from the firmware all the way up through software monitoring. In doing so, the startup has taken perhaps the most ambitious stab yet at the problem of IT security in the cloud age.
Doug Gourlay, corporate vice president at Skyport, says that part of the impetus for this hybrid hardware/software model comes from a simple yet nearly impossible challenge. “How will I prove that the software I have running on my server is exactly the software that I want on it? The conclusion we have come to is that software cannot verify software.”
There are of course best practices to implement that can guarantee a high level of security, most prominently from the National Institute of Standards and Technologies (NIST). However, in the frenetic day-to-day activity of the typical IT department, maintaining those best practices is at best futile.
A Triple-Pounder of Security
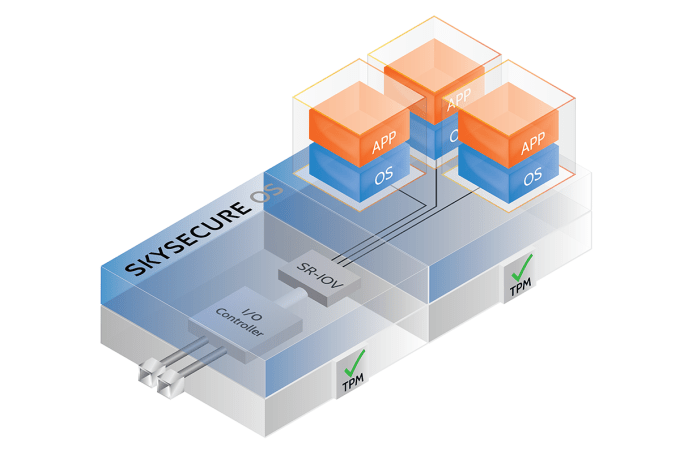
Skyport’s Diagram of the SkySecure System
Skyport hopes to transform those written best practices into hardware and software components that can enforce them. The company’s system relies on a three-layer model to build trusted computing. At the base layer, the company offers a hardware server product that is designed to be turn-key and secure by default.
To get a sense of Skyport’s product, imagine an intruder trying to gain access to a server box. There is an old adage in security that no amount of programming can stop an attacker with physical access to hardware. Skyport’s system, however, uses a set of checksums to independently verify the firmware and software currently running on the server. Even if there is tampering, the system should detect this quickly and remove the offending unit from service.
Perhaps even more notably, the company shoots high-resolution photographs of the motherboard before delivery as part of its secure supply chain, and can then cross-verify them to ensure that the physical machine hasn’t been compromised at the hardware level. “A customer can go back five years later and check the serial number and what it looked like,” Gourlay explained.
The second layer of Skyport’s system uses traditional approaches to compartmentalizing software, but enforces it at the hardware level. A key aspect of IT security is whitelisting, or authorizing only certain connections to reach a server. However, the software model currently used by IT departments is prone to attack from hackers. The SkySecure Server is designed to hardware-enforce these whitelists, hardening them against potential software-based attacks.
The third and final layer is a product called SkySecure Center, which acts as a secure data warehouse for IT policies and logs. One challenge that companies face is from insider attacks – compromised IT workers who break into their own systems using all of their sudo-powers. Stopping this vector of attacks is key for corporate security, but incredibly difficult to implement in practice.
What Center offers is tamper-proof logs and traffic that can be audited at anytime. Log entries are created for every single administrative transaction in the system, from a user signing in to making a policy change. These can never be altered or deleted by a hacker, nor an admin. In addition, there are beautiful dashboards and analytical tools on top of this data that can help IT staff find potential threats and variances in their infrastructure.
Solving The Security Dilemma
Security is no longer a simple addition of a firewall near the ethernet port leaving a server closet. Attackers have become incredibly sophisticated in their approaches, and Skyport believes that only a completely integrated “hyper-secured” system designed to match will protect corporate digital property.
Considering the scale of the company’s ambitions, it shouldn’t be surprising that it has taken a little more than two years to get its product to public launch. The company’s goal up until now has been making its design customers successful before scaling the product to a wider audience.
Skyport doesn’t expect that customers will adopt thousands of these devices immediately. Rather, it is taking the philosophy that companies will prefer its technologies in sensitive areas of their infrastructure where the security perimeter needs to be tightened, such as servers for important overseas markets. The company hopes that as those systems gain credibility with IT staff, companies will wish to deploy the technology throughout their data centers.
Pricing is based on a software-as-a-service model, priced monthly but billed annually, with a typical enterprise sales model.
Gourlay believes this model of security can be the future of trusted computing in enterprise. “An Xbox and my iPhone are more secure than any enterprise server being deployed today,” he said, due to the complexity of policies and applications required to run the modern corporation. If Skyport’s system works in concert the way the company intends, then it might just have the product a lot of IT departments are hungry for. Winter may not come after all.