
Any third-party Twitter app developer can currently ask you to authorize software using OAuth under the pretense that they will not be able to access any of your private – both sent and received – messages, while in fact they easily can. TechCrunch was contacted by developer Simon Colijn, who hopes to make as many people aware of this privacy issue – or disaster, if you will – as possible. Note: See update from Twitter below.
Colijn created this test application to prove that the anomaly with the authorization process actually exists. You can use a dummy account if you’re not comfortable clicking anything on that page, but I just ran a test with my personal Twitter account.
Sure enough, I was shown an authorization screen that explicitly told me that the app would not be able to access my private messages … after which it swiftly did in mere seconds.
To be clear, the developer had selected the option ‘Read-only’, which means he wasn’t supposed to be able to fetch (and thus download and store) my direct Twitter messages at all.
This obviously gives the term ‘private messages’ a whole new meaning.
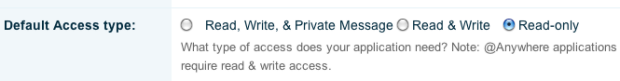
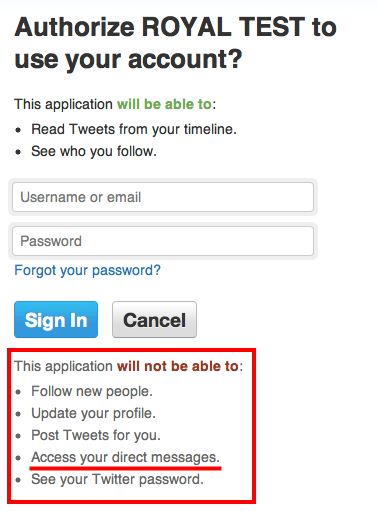

One Twitter app developer I’ve since spoken to about the privacy issue, Topify.com founder Arik Fraimovich, suspected that what is going on is this:
Twitter recently updated its OAuth screens, which are supposed to give users greater transparency about the level of access third-party applications have to their accounts.
Fraimovich thinks what happened is that Twitter planned to release the new authentication model (which will limit DM access) on June 1st, and then postponed it to the end of June without fully realizing that the new UI for the OAuth permission screens would already be live.
In other words: what you see is not quite what you get.
The reason why I think this is in fact a serious privacy fail that shouldn’t be simply swept under the rug: there are currently hundreds of thousands of third-party applications on Twitter, as Twitter itself repeatedly says, and at this point they can all trick you into authorizing their software while you think they will not be able to see your private messages (or do all other sorts of things with them than just view them, like publishing them elsewhere).
One developer I know, Mike Robinson, was kind enough to verify the bug a third time just to make sure it exists, creating a test Twitter application that exploited the privacy hole in just a couple of minutes. Think about that.
Whether this is indeed a UI screw-up, or a more serious system bug of some sorts, it’s an issue that can affect a lot of people’s privacy.
We’ve contacted Twitter about Colijn’s discovery a few hours ago, but haven’t heard back yet (note that it’s early morning in San Francisco).
Either way, think twice before you authorize third-party apps on Twitter, check your settings to see which applications can currently access your account, and in general be careful not to share too much private or sensitive information via direct Twitter messages.
UPDATE:
A spokesperson for Twitter issued this statement to us:
As we announced in May, Twitter is transitioning our authentication model to give users more control over the information they share with third-party applications. We recently extended this transition until the end of June to give developers more time to reconfigure their applications to fit the new model. We are updating the text in the current permissions screens to clarify what information applications will or will not have access to during the transition period.
For a summary of the third party applications you’ve approved or to make changes to this list, visit the “Applications” page in your Twitter account.
Related reading:
Twitter Revokes Automatic 3rd Party DM Access, Gives Users More Details On App Permissions (May 2011)
Latest Twitter Bug: “Misdelivery of Direct Messages” (April 2009)
DMFail: Another Reason To Just Not Send Private Messages On Twitter (December 2008)
Privacy Disaster At Twitter: Direct Messages Exposed (April 2008)
(Image from Flickr user Dan McKay, used with permission)