Internet telephony giant Skype may well have a significant security issue on its hands, TechCrunch has learned.
Someone claims to have reverse-engineered the proprietary encryption protocols Skype has put in place to prevent developers from building their own Skype desktop clients or Web-based services based on the company’s in-house technology. If this checks out, this basically means the walls of Skype’s pretty garden have been abruptly hauled down, something the company was hoping to do on its own, albeit slowly, by rolling out public APIs in the future.
The full extent of what a possible breach of this system could entail is unclear, but worst case, malicious hackers could gain insights from the reverse-engineered procedures and learn how to exploit it. To be clear: there’s no reason for panic until the implications become obvious.
Either way, Skype posits there is no security issue at all, but the jury is still out on that.
Let’s start with the beginning. The person (Sean O’Neil) who claims to have pulled of this feat, which has apparently been tried for the past 10 years to no avail, published a blog post with a title that leaves little to the imagination: “Skype’s Biggest Secret Revealed”.
The post was submitted to Reddit not long after publication, but for whatever reason the blog (enrupt.com) is no longer accessible now, although you can still get to the cached version of the article in question (see below).
Here are the key parts of the blog post (I removed the link to the ciphers, but they shouldn’t be too hard to find, as the information is already spreading in the places these things tend to spread, and quickly at that):
For over 10 years, Skype enjoyed selling the world security by obscurity. We must admit, really good obscurity. I mean, really really good obscurity. So good that almost no one has been able to reverse engineer it out of the numerous Skype binaries. Those who could, didn’t dare to publish their code, as it most certainly looked scarier than Frankenstein.
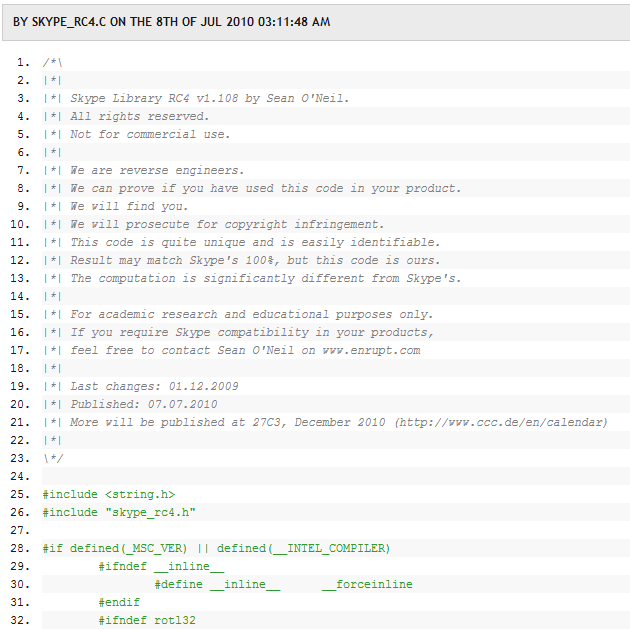
The time has come to reveal this secret. XXX contains the greatest secret of Skype communication protocol, the obfuscated Skype RC4 key expansion algorithm in plain portable C. Enjoy!
I’m no security expert, let alone an experienced coder, so it’s hard for me to assess the significance of the release of the algorithm. Co-Founder & CEO at Scio Security Dug Song, however, is convinced this is regarded as a major breakthrough in hacker circles, according to his tweets. Industry blog The H Security, meanwhile, cautiously warns that the publication of the code does “not mean that Skype’s encryption can be considered ‘cracked’ “.
For what it’s worth, Sean O’Neil (according to Skype perhaps not his real name) says this code has been in his possession for a long time, and that some of it was leaked a couple of months ago – leading to usage of it by hackers with malicious intent. He also says he reported the leak to Skype, but writes that he was “abused by Skype administration”, whatever that means.
I do not want to go into any finger-pointing details here, but naturally, we do not wish to be held responsible for our code being abused. So we decided that the time has come for all the IT security experts to have it. Why let the hackers have the advantage? As professional cryptologists and reverse engineers, we are not on their side. Skype is a popular and important product. We believe that this publication will help the IT security community help secure Skype better.
However, for the time being, we are not giving away a licence to use our code for free in commercial products. Please contact us if you need a commercial licence.
The blog post is signed with ‘Skype Reverse Engineering Team’, and ends with an open invitation to the next Chaos Communication Congress (27C3) in Berlin, to “hear all the juicy details on how to use this function to decrypt Skype traffic”.
Skype is quite open about being aware that this code is out in the open, but seems overly confident that it poses no security risk of any kind. This is the statement I was provided with:
Skype, like other software that provide IM capabilities, has been the target of SPAM. We have been working for some time on reducing this volume and as a result have seen a marked decrease in the volumes of SPAM directed to our customers. We believe that the work being done by Sean O’Neil, who we understand was formerly known as Yaroslav Charnovsky, is directly facilitating spamming attacks against Skype and we are considering our legal remedies.
Whilst we understand the desire for people to reverse engineer our protocols with the intent of improving security, the work done by this individual clearly demonstrates the opposite.
Skype has invested heavily in the safety and privacy of our software and we are proud of the high levels of security that we are able to offer our customers. This release of code in no way compromises this. Skype remains a safe and effective method of global communications and Skype will vigorously defend our security from any and all known threats.
I’ll reiterate once more that I’m not a security expert, but I’m sure the significance of the code’s release will be actively discussed by people who are in the coming days.
Any security wizards who’d like to weigh in on this in the comment section?