Do SQL injections turn you on? How about double SQL injections? If the answer is ‘yes’, then
1): Good luck with your dating life
2) Boy are you in some luck!
A new of breed of security product called Seeker produces some vivid hacker pr0n in the form of a video (see above) of how it broke and exploited every nook and cranny of your unsecure code. Yes, I’m going to say it, Seeker might be the Seymore Butts of security products!
Kidding aside, Seeker seems be packing pretty fearsome application security technology. The company behind it is an Israeli white hat hacking shop called Hacktics. These guys do work for startups, banks, telcos, governments, and homeland security agencies. Their team members hold very high security clearances due to their prior and current service records in the IDF (Israeli Defense Force). It’s safe to say these guys know a thing or two about application security.
Seeker was designed for use by individuals that are part of the development organization which do not necessarily possess security knowledge, or even deep technical knowledge. These can range from developers, to QA staff, to team leaders. It’s for this reason that Seeker points to real business threats rather than just technical issues.
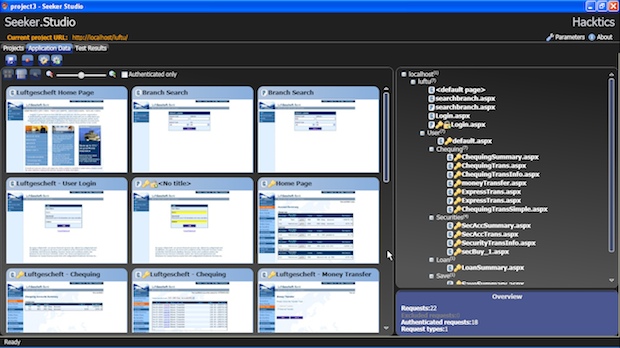
This is where a two particular product features stand out. Seeker produces screenshots (see below) that allow testers to see the vulnerabilities in the context of the actual application functionality they relate to, rather than getting just technical information based on URLs. The screenshots also contain screenshots showing how the application handled each attack.
The second stand-out feature is ‘Exploit Videos’. Seeker automatically creates a step-by-step exploit video for each vulnerability it identifies and exploits, making it easier for the developer to manually reproduce errors before and after fixing the code. Video is also quite an effective method for non-security users to understand the actual threats and potential exploits. Just imagine being able to show management or external developers such a video. Pretty effective stuff.
Seeker’s methodology is to perform runtime analysis of code executed in order to identify security flaws in the application. This is done by hooking into the process executing the application, and performing step-by-step analysis of the executed code. The attacks themselves are generated dynamically based on a ‘Smart Attack Tree,’ a long list of rules for mutating attacks based both on how the application reacts to them, and the actual application code.
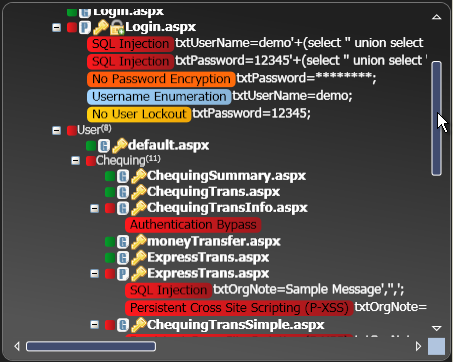
The product supports an orgy of vulnerabilities, including: SQL injection, XML/XPath injection, directory traversal, cross-site scripting, parameter tampering, forceful browsing, malicious content upload, username/password enumeration, insecure redirects, source code disclosure, insecure storage of sensitive data (such as Credit cards, CVVs, SSNs), cookie poisoning and plenty more.
Currently supported are Java and .NET code analysis, using any database if no stored procedures are used. For stored procedures, Seeker supports Microsoft SQL and Oracle. PHP, as well as support for MySQL stored procedures, will be rolled out in a few months.
Seeker is currently headquartered in Israel, with $3M in funding under its belt.