Octarine, a startup that helps automate security of Kubernetes workloads, released an open-source scanning tool today. The tool, which is called Kube-scan, is designed to help developers understand the level of security risk in their Kubernetes clusters.
The company is also open-sourcing a second tool called The Kubernetes Common Configuration Scoring System, or KCCSS for short, which is the underlying configuration framework used in Kube-scan.
As Ocatrine’s head of product Julien Sobrier points out, there are 30 security settings in Kubernetes, and Kube-scan can help you see where you might be vulnerable on any one of them, measured on a scale of 0-10, with 10 being extremely vulnerable.
“Kubernetes gives a lot of flexibility and a lot of power to developers. There are over 30 security settings, and understanding how they interact with each other, which settings make security worse, which make it better, and the impact of each selection is not something that’s easy to measure or explain,” Sobrier told TechCrunch.
Octarine wants to help with these two open-source tools. It started by building KCCSS, a vulnerability model based on the industry-standard Common Vulnerability Scoring System (CVSS), to provide a risk assessment framework for Kube-scan.
“We’ve taken this model of CVSS and applied into Kubernetes. This helps explain to users, what are the security settings that are causing risk? What is the danger to the workload in terms of availability of the cluster, integrity of the cluster and confidentiality of the cluster,” Sobrier explained. This gives developers and operations a common system for understanding of the security posture of the cluster, and makes it easier for them to decide whether the risk is acceptable or not.
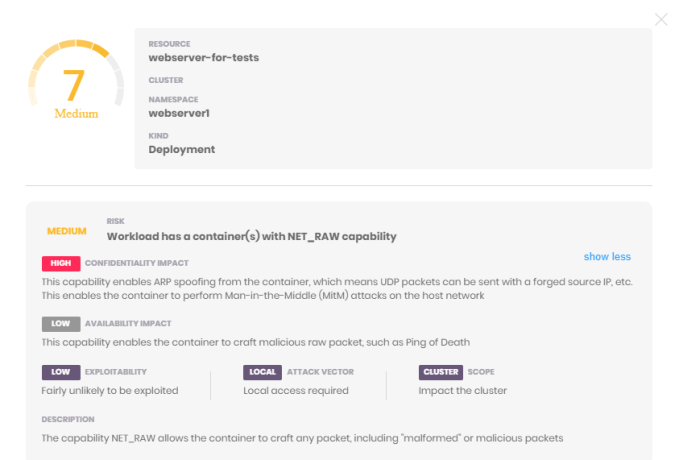
Kube-scan result. Screenshot: Octarine (cropped)
They have then taken the KCCSS framework and built Kube-scan. This takes the settings as defined in KCCSS and applies a score, which measures the level of risk for each setting in the Kubernetes cluster you run it on. “Kube-scan is basically an implementation of the KCCSS framework. So it’s software, a container, that will run on your cluster and show you the risk of all the [settings] on a scale from zero, not risky, to 10, highly risky, and then give you all the details about what the grade is and the possible remediation that you that you can put in place,” he said.
While it obviously could work hand-in-glove with Octarine’s own security tools, Rafael Feitelberg, VP of Commercialization, says the project has been more about helping companies see their Kubernetes cluster risk level, and giving them information to fix the problems it finds. “A lot of these things can be remediated by adjusting the Kubernetes configuration, and you can explicitly see see how you can remediate [the problem] in Kube-scan,” he said.
Feitelberg says that Octarine is something separate, designed to help you automate your security settings. “Our commercial product is more about the automation of the process, of doing this continuously, so it’s part of your CI/CD [pipeline] and your DevOps process,” he said.
Both of the open-source tools are available today on GitHub.
