We have a love affair with our cars. We equate them with independence and romance. We spend hours washing, waxing and restoring them.
As a portion of total consumer credit, we spend more on car loans than we do on home mortgages. So when researchers claim they can remotely control our cars, disable the brakes and take control of the steering, and news websites show pictures of an SUV nose down in a ditch, it affects us not only as an intellectual exercise, but at an emotional level.
It’s true that researchers have proven time and again that they can turn our cars into compliant minions at their beck and call, but while the public at large may gasp in shock, anyone in information security may shrug and think, “Sounds about right.” The main reason to be so cavalier is that, despite the recent attention on the issue, the body of research on connected vehicle security extends back five years.
To come to grips with the true risks of connected vehicle security, we have to separate the fear-driven hype from the practical motives of the threat actors.
I’ll start with a brief history of car vulnerability research to understand what’s been shown to be possible. Then I’ll take a closer look at the varying threat actors in the world of cybercrime and the ways they might take advantage of vehicle security flaws in real life.
A Short History Of Car Vulnerability Research
In 2010, researchers from the University of Washington and University of California, San Diego published a seminal paper proving that once an attacker has physical access to a vehicle, they can compromise every component, from the entertainment system to the electronic control units (ECUs) that operate the engine, brakes and even the steering wheel in modern cars that self-park and sport lane-departure correction.
This research showed that an attacker could use connection points between vehicle systems as an entry point to inject arbitrary commands on the controller area network (CAN) bus to perform activities such as disabling all the engine’s cylinders, locking up one brake pad and disabling all brakes — even when the car was traveling at 40 miles per hour. The researchers even created a CAN bus analysis and packet injection tool, dubbed CarShark.
But the automakers weren’t phased by the research; their view was that an attacker would have to be jacked into your car in order to execute an attack.
In response, these same researchers undertook another study in 2011 to further prove their point, this time centered on how to remotely gain access to the vehicle. The paper enumerated the attack surfaces, including channels that provide remote access: Bluetooth, in-vehicle Wi-Fi, telematics, remote keyless entry and RFID immobilizers, dedicated short-range communications (DSRC) used to communicate between vehicles and the road infrastructure, global positioning (GPS), satellite radio and even tire pressure monitor sensors.
The researchers took the play from the punt to the end zone by remotely compromising a vehicle, then using the techniques they created in their first paper to gain complete control of the car. They even claimed they could compromise the telematics unit by simply playing an audio file over the mobile carrier’s network.
Using another vector, the researchers wrote a mobile phone Trojan that gave them remote access to a driver’s or passenger’s mobile phone, and when paired with a vehicle’s telematics unit, exploited a vulnerability in the Bluetooth firmware. They effectively used the mobile phone as a springboard to pwn the vehicle.
In a zombie apocalypse scenario, the researchers even wrote software that could turn cars into a rolling “bot” army.
The researchers also compromised a typical diagnostics computer used by many service shops so that when it was connected to the diagnostics port on a vehicle, the computer would infect the vehicle with malware allowing the attackers to control it. In a zombie apocalypse scenario, the researchers even wrote software that could turn cars into a rolling “bot” army that reports back to a command and control (C&C) channel through which a criminal could issue commands.
It would seem that these researchers had proven conclusively that connected vehicle security required retooling, and that the consequences could have a major impact on customer confidence and safety. However, without details on the specific vehicles involved in the research, nor publicly disclosed proof of concept instructions, the automotive industry made little public noise about the research.
In fairness, the auto industry may have rallied war rooms and devised plans to amp up security in their automotive products; however, the automotive industry is tight-knit and guards new designs and technology closely. Further, modern automobiles are complex marvels of engineering, and the process of retooling the mechanics and software has to be undertaken slowly, carefully and over a period of many years. Bear in mind that from inception, a new automobile typically takes 5-7 years before it hits the mass market.
And yet, to the general public — and especially to researchers — the silence implied apathy on the part of the automakers. Some in the industry may not fully recognize the broader implications of these results. For example, I spoke to the design manager on the topic of the tire pressure monitoring system (TPMS) vulnerability and he responded with: “So what? All you could do is light up an amber LED on the dashboard.”
Which would be true if all TPMS receivers only had a wire loop that went to the LED in question; however, it’s likely that most of the automakers connect the TPMS receiver to other parts of the in-vehicle network, if for no other reason than to send that data as telemetry back to the predictive maintenance analytics running in the cloud. But let’s not get hung up on the TPMS system: The vehicle threat surface is as broad as the African savanna is to a big game poacher.
The vehicle threat surface is as broad as the African savanna is to a big game poacher.
Enter Charlie Miller and Chris Valasek, whose 2013 Today Show vehicle hack elicited a collective gasp from the public. Automakers pointed out that such a hack would be unfeasible in real life, as the dashboard is dismantled and there’s a guy sitting in your back seat with a laptop. As is the way with such stories, other shiny objects and celebrity reality television soon overwrote that chunk of the public’s short-term memory, and drivers slid behind the wheel with nary a thought of cars gone wild.
In 2015, Miller and Valasek were back. The widely publicized video of these researchers remotely hacking into a vehicle on the road and ultimately sending it into a ditch struck a chord with the general public that research to date had yet to reach.
To put this in perspective, Recorded Future, which collects intelligence from more than 600,000 sources, including social media and underground forums, queried their data warehouse for mentions of connected vehicle security. As displayed below, there was a fair amount of chatter when the CarShark exploit was announced, then it exploded around the two Valasek and Miller exploits. The red “bubbles” show the amount of references by date and the milestones are called out. Additionally, references to announced or publicly speculated future events are plotted at the bottom of the chart.
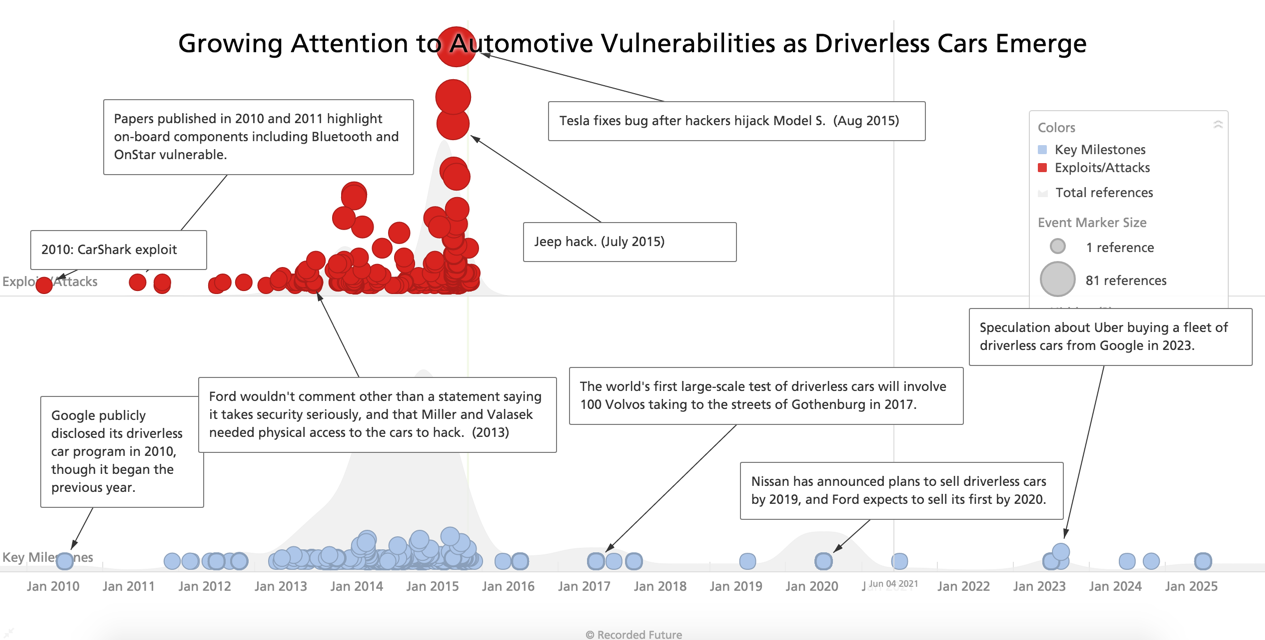
The above graphic overlays growing references to attacks and exploits against automakers, vehicles and components with anticipated milestones for driverless car technology. (Source: Recorded Future)
I’d like to say that the latest research will have a more lasting impact on the general populace, but history doesn’t support that hope. And honestly, I’d rather the world not exclusively focus on the hyperbolic consequences of hacking vehicles, because those scenarios are so unlikely that they distract from the more likely motives of serious attackers.
To understand the threat cases where flaws could be used in real life, you first have to get a sense of the pantheon of threat actors.
Introducing The Pantheon Of Connected Vehicle Hackers
Researchers. Yep, they’re a kind of threat actor. Researchers test the security boundaries; their motive is usually publicity for their organizations or personal fame (or notoriety, depending on your perspective). Certainly they can annoy the makers of the products that they hack, but the level of threat they might pose to any individual driver is low.
Competitors. Corporate espionage and sabotage exist. The motive here is commercial gain: to steal intellectual property, gain intelligence on future plans and, in the most insidious case, sabotage a competitor’s offerings or expose embarrassing communications to inflict brand/reputation damage.
Insiders. Largely the same as competitors, but usually someone who’s either grown disillusioned with the company or is being paid to be an insider agent.
Criminals. Most of the security exploits we see that target traditional computers are due to cyber criminal activity: banking trojans that steal online account information, ransomware, credit card data theft. The main motive is financial gain at the expense of their victims. Theft of personal information and accounts are one hop away from the money; criminals use that information to forge credible phishing emails to get their malware installed on end-user machines and nation states may use it to track high-value targets.
Hacktivists. Also known as chaotic actors, hacktivists want to make a political statement. They’ll use website defacement, denial of service (DoS) attacks, pasting account info online, doxing and any tactic that embarrasses their target.
Ideologues. Somewhere between hacktivists and nation states, ideologues will go to extremes to make a statement, including causing physical and corporeal damage. Think terrorists.
Nation States. Opposing countries and governments seek intelligence, and will use cyber espionage to get it. Nation states also desire tactical weapons, including access to their enemies’ critical infrastructure, such as electric, water and sewer utilities.
 Image: Shutterstock/Nikita Chisnikov (modified by Bryce Durbin)
Image: Shutterstock/Nikita Chisnikov (modified by Bryce Durbin)
Motives And Threat Cases
Let’s apply these threat actors and their motives to a threat model for connected vehicles. We’ll omit researchers since their interests bridge the entire spectrum: Effectively, they want to discover all the ways to compromise vehicles. In that sense, they’re agnostic. It’s also worth noting that most researchers act responsibly and aren’t hacking in order to create a threat, but instead to find and prevent them.
Competitors And Insiders
As noted previously, they can share similar motives; the difference is the knowledge they have of the organization and the trust that the organization puts in them. Their primary target is usually the IT network, where they can find and steal product plans, intellectual property, software and firmware, emails and other information.
Theft of data may not seem to directly affect the connected car itself, but competitors and insiders may also sabotage vehicles by adding flaws to a schematic or a bug in firmware, either of which might cause a failure in the vehicle’s control or safety systems. They may also target the app that controls the vehicle (e.g., an iPhone or Android app to start the car, monitor fuel usage, etc.) to a similar end.
Bear in mind, however, that the line between stealing data and causing physical harm, while narrow in difficulty of execution, is an abyss from whence there is no return. The mitigating control is human morality, governed by laws and strict penalties. In short, it’s unlikely that insiders or competitors would sabotage vehicles to harm the occupants.
Nation States
Nation states share some of the same motives as competitors and insiders. However, they may have other, more dangerous intentions. One scenario might be gaining access to the in-vehicle network of an enemy’s fleet of diplomatic limousines. Imagine surreptitiously listening in on political plans and state secrets through the hands-free microphone in the vehicle. Even without access to conversations, enemies could monitor the itineraries of officials and infer all kinds of interesting intelligence.
Hey, accountant from Peoria, no nation-state wants to send your minivan into a deep ditch.
On the more insidious side, nation states could take control of the steering wheel of a limo transporting an enemy or brick its engine and, well let your imagination and Tom Clancy fill in the rest. But while this may be possible, it almost surely won’t impact most people’s day-to-day driving, and is not a cause for mass hysteria. Hey, accountant from Peoria, no nation-state wants to send your minivan into a deep ditch.
Ideologues
Ideologues, on the other hand, are the one group who act to cause wide fear and are prepared to cause physical harm. They also may target the IT network, but more than likely to get plans and code that they can use to penetrate the vehicle or controlling app. Once they control vehicles, they may disable the brakes or shut off the engines of all cars on the California 101 freeway at rush hour just to cause mayhem and harm. They may not choose their victims carefully; terrorism is mostly a game of opportunity.
Fortunately, such a scenario is unlikely and shouldn’t be a paralyzing concern to the average driver or passenger; and yet, due to the severity of the potential harm, automakers need to take the threat seriously.
Hacktivists
Hacktivists may target the IT network to steal emails and documents to dox executives, post intellectual property on Pastebin or expose emails to the public. They may launch a denial of service (DoS) attack against the portal to which your car’s mobile app connects, preventing you from being able to open the door or start the engine remotely, at least without a key fob. They may also brick the vehicle. All nuisances for sure; but again, hacktivists are unlikely to nose dive your SUV into a ravine.
 Image: Shutterstock/Hluboki Dzianis
Image: Shutterstock/Hluboki Dzianis
Cyber Criminals
There’s an expression in the information security community that if you want to find out what the threat is, look for where there’s money to be made. In other words, most of the malware, phishing, exploits and just general havoc wrought on computers is the work of cyber criminals who just want your money. Let’s look at some of the ways they can capitalize on connected vehicle vulnerabilities:
Vehicle Theft. The car itself has a value, and criminals want to transfer that value from you to themselves. The deterrents are your car lock and alarm system. However, as those functions creep into the app on your mobile phone, attackers can simply get you to install malware and they can have their way with your car. Or they can attack the automaker’s web portal and potentially own any car on the road. Thieves still have the traditional “Gone in 60 Seconds” problem: Criminals need someone to jump into the vehicle and drive it off…until autonomous vehicles become mainstream.
Vehicle Tracking. Using geolocation or telemetry sent from the vehicle, criminals can locate vehicles wherever they are and steal them. If the thief manages to install malware in the vehicle, it could report back the VIN, which is tied to a make, year and model, and the thief could filter out the exact car desired, much like carder forums allow buyers to choose lots from certain geographies.
The thief also could use the information to target homes for burglary: When all vehicles belonging to the homeowners are outside a 15-mile range, the burglar has a guaranteed half-hour of uninterrupted home invasion. Couple that with information from compromised home IoT devices that track occupancy, and the burglar can practically make a meal and watch a television program in your absence, with a notification when you’re 10 minutes out.
Another byproduct of tracking vehicles is the ability to determine your habits.
Just as social networking provides a trove of intelligence for creating convincing phishing emails, another byproduct of tracking vehicles is the ability to determine your habits. The criminal could send an email purporting to be from a place you actually visited, such as a restaurant or golf course.
Data Theft. Mobile phones are the digital equivalent of our bloodstream, carrying information to and from us, providing services like email and texting, calendaring, contact management, phone logs and a host of other critical information. The ultimate goal is to have the phone and car merge into a single unit, where the head unit takes over all the phone functions for the duration of your occupancy in the vehicle. That means that the phone trusts the vehicle and vice versa, and that the vehicle will contain a significant set of data that resides on your phone. That data and the apps are valuable to criminals for a variety of purposes, of which the mobile security experts have already done a thorough job of enumerating and I’ll leave as an assignment for you to Google.
Ransom. Perhaps one of the most lucrative schemes in cyber crime is ransomware, whereby malware encrypts the data on your computer and instructs you to pay the criminal to restore the decrypted data. The connected vehicle provides a promising new platform for this tactic: Brick the engine or disable the brakes and demand a couple of bitcoin to restore the vehicle to a functional state. This avoids the need to have a mule nearby to drive away in a stolen car, and criminals love asymmetric campaigns: minimal effort, maximal reward.
Keep Calm And Carry On
None of the above threat cases has the mass doomsday effect that the press has attributed to the Miller/Valasek hacks. The point is to stay calm and carry on. In fact, a search of the Recorded Future data presented earlier shows no chatter of threat actors discussing connected vehicles as a target. To take some poetic liberty, 700,000 sources and nothing on (as far as threats against cars).
However, that’s not to say automakers can ignore the severe threat cases: they need to design for failure and expect the worst. In my experience, they are taking the threats seriously. It turns out that it’s a monumental task to change the design of vehicles, and they don’t have the luxury of scrapping existing designs and starting over. It’s now a race between automakers and the threat actors.
Interestingly, one of the biggest threats may be economic. Transportation is critical infrastructure all over the world. Many people rely on cars to get to work and to get work done. The side effect of vehicle vulnerabilities is that, if cars become unreliable or unavailable due to malicious activities, local, regional, national and global economies can be affected. And it’s not just personally owned vehicles: The threats expand into the entire transportation system, including vehicle fleets; cargo carriers, such as trucks, trains and ships; public transportation, such as commuter trains, buses and ferries; and private conveyances, such as airlines.
Expect to hear more as smart cities come online and the IoT subsumes more everyday objects.