Alongside the launch of the Kardashian and Jenner mobile apps, which are now dominating the App Store after seeing hundreds of thousands of downloads apiece in their first days on the market, the celeb sisters also released new websites designed to help them better connect with their fans while offering a more personal look inside their lives.
However, one enterprising young developer dug around those websites and immediately found an issue. Due to a misconfiguration, he was able to access the full names and email addresses of over 600,000 users who signed up for Kylie Jenner’s website as well as pull similar user data from the other websites.
In addition, the developer said he had the ability to create and destroy users, photos, videos and more, though we understand he didn’t actually take those actions.
The developer in question, 19-year-old Alaxic Smith, had some interest in the celebrity biz already. As the co-founder of Communly, he’s been working on a mobile app that lets users connect with others who share their interests, including tracking new information about favorite celebs, for example.
On blogging site Medium, Smith explained how he was able to access the user data from Kylie Jenner’s website. He also noted that his explorations initially began as idle curiosity about what was powering the new sites under the hood, rather than being some malicious hack or even a more focused attempt at uncovering security vulnerabilities.
Writes Smith:
I’ll admit I downloaded Kylie’s app just to check it out. I also checked out the website, and just like most developers, I decided to take a look around to see what was powering the site. After I started digging a little bit deeper, I found a JavaScript file namedkylie.min.75c4ceae105ad8689f88270895e77cb0_gz.js. Just for fun, I decided to un-minify this file to see what kind of data they were collecting from users and other metrics they may be tracking. I saw several calls to an API, which of course made sense. I popped one of those endpoints into my browser, and got an error just liked I expected.
Smith then logged into the website with his own user name and password and was directed to a web page that contained the first and last names and email addresses of the 663,270 people who had signed up for the site, he says.
Following this discovery, Smith realized he could perform the same API call across each of the other sisters’ websites and return the same data. Besides being able to access this user data, Smith says he found he was also able to create and destroy users, photos and videos.
Essentially, what he had discovered was an open, unsecured API.
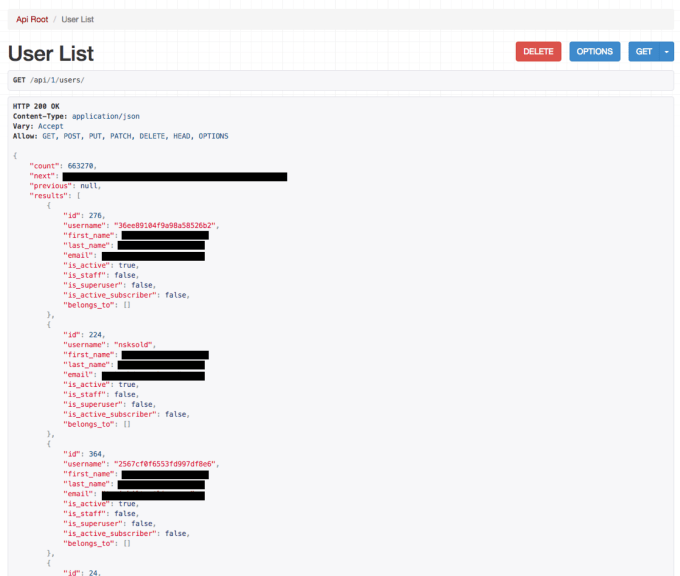
As this was clearly a major issue in terms of security, and a surprising find given the high-profile nature of the websites, the developer immediately blogged about the problem on Medium where he posed the question: “should users trust not only their personal information, but also payment information with these apps?”
In case you’ve been living under a rock, what he’s referring to is the fact that the new websites and apps from Kim Kardashian West, Khloé Kardashian, Kendall Jenner and Kylie Jenner, released earlier this week, offer up exclusive content to paid subscribers who provide their payment information. Like a private, members-only social media platform, each sister’s website and app offers a unique look into their own interests, with content that includes diary entries, live video, beauty tutorials, workout tips and more.
 While it’s one thing to have your name and email exposed (or more embarrassingly, the fact that you’re actually paying for this sort of content in the first place!), if the websites lack strong security, that could be putting users’ personal and private information at risk.
While it’s one thing to have your name and email exposed (or more embarrassingly, the fact that you’re actually paying for this sort of content in the first place!), if the websites lack strong security, that could be putting users’ personal and private information at risk.
We reached out to the company behind the sites and apps, Whalerock Industries, to confirm the details of the data breach and the patch.
We understand now that Smith is now cooperating with the company, as he’s taken down his original blog post and declining to talk to media.
A Whalerock spokesperson confirms that user data was available briefly, but the issue was soon addressed, saying:
Shortly after launch we were alerted that there was an open Api. It was promptly closed. Our logs indicate that the author of the blog post was able to access only a limited set of names and email addresses. Our logs further indicate no one else had access and that no passwords nor payment data of any kind was exposed. Our highest priority is the security of our customers’ data.
For what it’s worth, the majority of the payments related to the sisters’ new tech properties were handled through the app stores, not via the web. We’ve also confirmed that Whalerock has been working with a third-party e-commerce provider to handle online payments. That means they were never hosting payment information on their own servers – something the team is likely thanking its lucky stars for right now.
And the security hole itself was only open for a few hours, as Whalerock’s team was working around the clock during the big launch. Smith had contacted them at the same time he published his blog post, and the developers immediately took action.
We understand, too, that the company is still in the process of validating what data was breached, and what, if any, data was actually saved or archived by Smith himself.
But from the sounds of things, the young developer probably didn’t realize just what he was getting himself into when he compromised the security surrounding the hottest celebrity tech launches of the year, nor how risky it was to openly disclose such a thing to the world, no matter if he had done so without malicious intentions in mind.