There’s evidence to suggest that hackers are using popular websites to attack government agencies, NGOs and other cyber espionage targets with increasingly more subtle insurgencies.
That’s according to the findings of a new report from security firm FireEye, which last month revealed details of a ten-year cyber campaign waged out of China against companies across Asia. The company’s newest dispatch sheds light on another China-based hacking group that used popular Microsoft web forum TechNet to remotely activate malware that could grant it access to an organization’s internal network and, potentially, troves of private data.
The program — run by a group known as APT17 — has since been shut down by Microsoft and FireEye. It didn’t appear to pose a threat to regular users of the website, rather TechNet was used as a seemingly legitimate medium through which the group could pull the levers necessarily to infiltrate a target.
In basic terms, APT17 — which FireEye said has targeted the likes of government agencies, NGOs, and legal firms — would initially seed malware with an individual inside a target organization, perhaps using a malicious file delivered via email. If the malware loaded successfully, it could be remotely triggered using code that was embedded within a comment left on the TechNet forum.
BLACKCOFFEE, the software that APT17 used for its offenses, can enable the group to carry out a range of activities, including uploading and downloading files, terminating processes on a host machine and introducing other backdoor commands.
Though the comments themselves appeared nonsensical and spammy, they represented a more covert method of laying an activation code without attracting the attention of internal security systems.
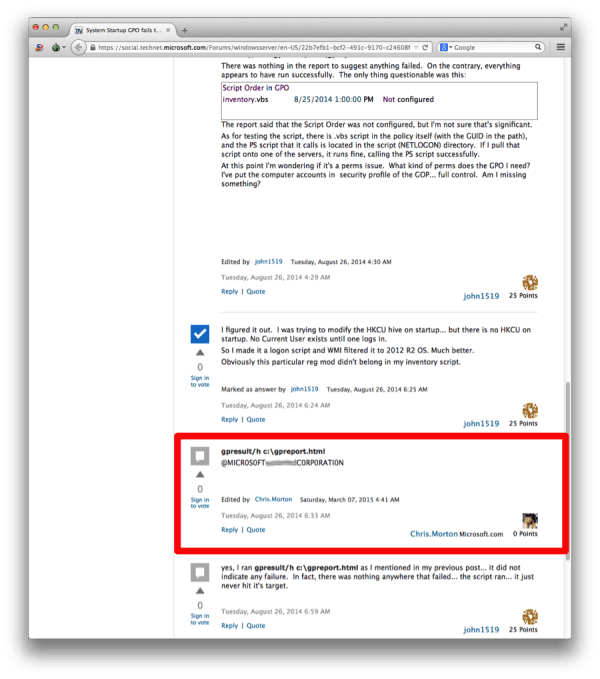
Embedding encoded C2 IP addresses into a site like TechNet, which is frequently visited by IT professionals worldwide, made detecting malicious activity more challenging than tracing threats from websites that have entirely compromised for nefarious purposes. In other words, visiting a site like TechNet regularly isn’t likely to raise alarm like regular traffic to obscure websites hosted in Russia, for example.
“This additional obfuscation puts yet another layer between APT17 and the security professionals attempting to chase them down,” FireEye said in its report.
Ultimately, FireEye contacted Microsoft, which locked the group’s accounts on TechNet, but it said that this strategy — which “few security companies have publicly discussed” — is likely to become more commonplace as cyber espionage techniques evolve in sophistication.
“Organizations will need new technology to detect these attacks,” Bryce Boland, FireEye’s APAC CTO, told TechCrunch in an interview. The case is a reminder that organizations with “highly critical environments shouldn’t allow people to receive content from the internet.”
But the onus isn’t just on companies to manage their network, Boland added, websites that allow user-generated content — including social networks — should also be wary.
“You look at a lot of sites and the nonsense that people post in comment sections, but did you ever think it was so bad that it could be an attacker looking for an intrusion?” he added.
