Symantec has found an unusual new threat called Regin aka Backdoor.Regin. The software, which is essentially a very powerful Trojan Horse, appears to have been circulating in the wild since 2008 and has been hitting governmental, industrial, and individual systems with impunity, using sophisticated encryption and targeting systems to spy on targets.
The anti-virus company has released a white paper on the new threat, noting its similarity to the specially targeted Stuxnet virus that attacked Iranian nuclear reactors.
Is the tool still a threat? As far as Symantec can tell the original Regin virus disappeared in 2011 only to reappear in 2013. The virus was able to hide itself completely on host computers and it wasn’t until Symantec reverse-engineered its packets that they were able to tell the scope and danger associated with the virus. It seems that it is completely modular, allowing the controllers to use the product to steal information and spy on network traffic.
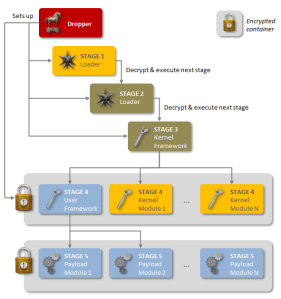
From the report:
Recode reported that the software has special payloads targeting airline and energy industries. It seems to have first spread in infected payloads hidden in legitimate software.