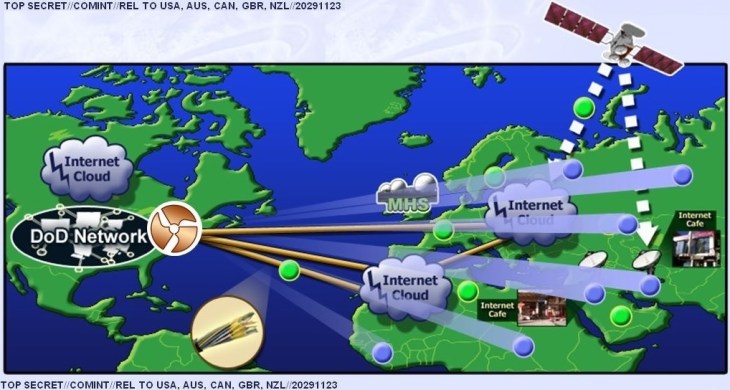
The National Security Agency reportedly has plans to control millions of computers by infecting them with malware, according to documents leaked to The Intercept by NSA whistleblower Edward Snowden.
“In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam,” explain The Intercept’s Ryan Gallagher and Glenn Greenwald.
The documents reveal that the NSA’s plans to infect networks was once reserved for a few hundred targets, but quickly ballooned into a larger scale project to hunt out suspects.
“The NSA began rapidly escalating its hacking efforts a decade ago. In 2004, according to secret internal records, the agency was managing a small network of only 100 to 150 implants,” explains The Intercept.
“Implants” is a term from the documents for the hacking done to suspected computers. “But over the next six to eight years, as an elite unit called Tailored Access Operations (TAO) recruited new hackers and developed new malware tools, the number of implants soared to tens of thousands.”
Like most leaks from Edward Snowden, we do not know the impacts of the project or if they are on-going. It only gives us an idea of the kinds of things the NSA wants to do to surveil the Internet.
Intelligence agencies have long considered encryption technology a threat to national security. Since the 90’s, they’ve actively lobbied for tools that allow them backdoor access to people’s devices. More recently, they’ve sought to undermine international security standards that can prevent them from hunting suspects. Security experts, however, worry that promoting weaker standards makes the Internet more vulnerable to attacks from malicious users.
“As soon as you put this capability in the backbone infrastructure, the software and security engineer in me says that’s terrifying,” University of Pennsylvania Professor, Matt Blaze, told The Intercept. “Forget about how the NSA is intending to use it. How do we know it is working correctly and only targeting who the NSA wants?”