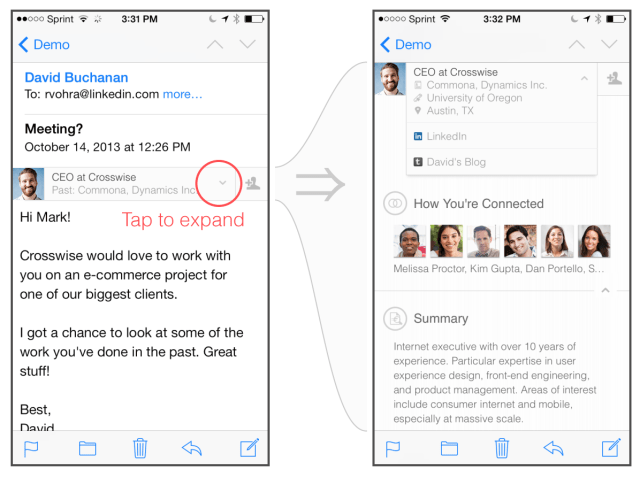
Earlier today LinkedIn launched a new iPad app and what appeared to be a pretty slick feature for iOS Mail called Intro. It presents the a profile of email senders right within the body of the message, with more details available with a single tap. It works like using Rapportive, which LinkedIn acquired last year.
Intro appears to deliver contact details in a nifty interface. It’s also a spectacularly bad idea.
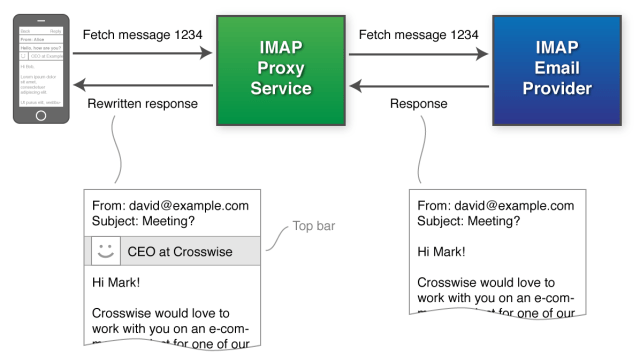
See, iOS Mail does not have an official extensible framework. Apple does not provide any APIs or frameworks to developers that would allow this kind of modification of its interface. Instead, LinkedIn is acting as a ‘man in the middle’ by intercepting (with your permission) your email and injecting HTML code into it that enables a style sheet to pop open over your content, containing an extended profile and information on positions held, connections and a bunch of other stuff.
The implementation, explained in a LinkedIn blog post, is pretty admirable from an engineering perspective. As ‘hacks’ go, this is a really clever solution to Apple’s fairly restrictive Mail.app policies.
But when you dig into the methods that LinkedIn is using to enable Intro, it becomes clear that this is a stickier proposition than it appears. Right off the bat, the installation process requires that you add a configuration profile that contains a set of signing certificates. Then it asks for your email username and password – unless it’s a Gmail account in which case the more secure Oauth method is used — which requires no password access for LinkedIn. Those enable LinkedIn to (presumably securely) obtain permission to act as a middle man between you and your email provider.
This proxy server is what is used to intercept (yes, as in grab, open and modify) your email and inject the code that makes Intro possible. Apparently there aren’t any humans involved in the process, and one would pray that your email contents remain un-readable somehow but I’m not sure how that’s possible. The ‘top bar’ that enables the feature is not a field or part of the header, it’s additional content that gets inserted into the body of the email.
LinkedIn seems to agree that this is how this works.
“We understand that operating an email proxy server carries great responsibility. We respect the fact that your email may contain very personal or sensitive information, and we will do everything we can to make sure that it is safe,” the section on security reads, along with a link to LinkedIn’s ‘pledge of privacy’.
That’s all well and good, and it’s fair to state flat-out at this point that I truly believe that the engineers at LinkedIn that created this hack are both insanely clever and really interested in giving you a cool way to access LinkedIn data. I find it highly unlikely that there is any malicious intent here. Instead, it’s simply a really clever solution to a problem that exists for a reason. Apple provides configuration profiles with email and encryption certificates for organizations that want to improve security, not companies that are enabling people to willfully compromise the integrity of their email stores.
Mail isn’t extensible because Apple wants to make sure that the sandboxed nature of its apps protects a user from code that could execute outside the mailbox. Because it’s actually handling your email outside of the device, LinkedIn is breaking none of Apple’s rules. It’s simply re-purposed Apple’s provisioning profiles and Mail.app’s ability to display HTML and CSS to hack in a new feature.
Unfortunately, that feature relies on handing over access to your email to a third-party — LinkedIn. That’s just never a good idea and may actually be against many corporate IT policies (I can guarantee it actually). Those corporate clients who have sensitive email that should never be transmitted via a proxy server probably have a fairly high overlap with the types of professionals targeted by LinkedIn with ‘Intro.’
LinkedIn likely has zero interest in bringing on the storm of crap that would come along with accessing your email, but once you insert a middle man, you’re adding a vulnerability to your email chain. A spoofed certificate served via a phishing site that emulates the LinkedIn Intro installation wizard is one possibility that pops to mind.
Even if you aren’t one of these corporate clients, adding in an interstitial proxy server that even temporarily handles your email is not a good idea – especially if the company who runs the server has been the victim of an enormous data theft hack which nabbed some 6.5M passwords and was shown to be transmitting emails, names and notes from your calendar in plain text. Both of which occurred in the last 18 months. I’m just not sure that LinkedIn doing ‘everything we can’ to keep us safe is good enough in this case.
Update: LinkedIn has reached out with an update to its engineering post, noting the following points, including the fact that the communications in between the servers are encrypted:
- You have to opt-in and install Intro before you see LinkedIn profiles in any email.
- Usernames, passwords, OAuth tokens, and email contents are not permanently stored anywhere inside LinkedIn data centers. Instead, these are stored on your iPhone.
- Once you install Intro, a new Mail account is created on your iPhone. Only the email in this new Intro Mail account goes via LinkedIn; other Mail accounts are not affected in any way.
- All communication from the Mail app to the LinkedIn Intro servers is fully encrypted. Likewise, all communication from the LinkedIn Intro servers to your email provider (e.g. Gmail or Yahoo! Mail) is fully encrypted.
- Your emails are only accessed when the Mail app is retrieving emails from your email provider. LinkedIn servers automatically look up the “From” email address, so that Intro can then be inserted into the email.
Update 10/26: Today, LinkedIn Information Security Manager Cory Scott published a a blog post explaining more security details behind the post. You can read those details here. Scott wraps up with this statement:
After having been a member of the security community for more than 15 years, I understand that healthy skepticism and speculation towards worst-case scenarios are an important part of the security discipline; however, we felt, in this case, it was necessary to correct the misperceptions. We welcome and encourage an open dialogue about the risks that are present in all Internet-based services that handle electronic mail and other sensitive data.
Image Credit: TAKA@P.P.R.S / Flickr CC
Article updated to note Rapportive acquisition.