Editor’s note: David Teten is a partner with ff Venture Capital and founder and chairman of Harvard Business School Alumni Angels of Greater New York. Follow him on Twitter @dteten.
Modern encryption systems are, in theory, exceptionally secure. The Advanced Encryption Standard (AES), for example, is so sophisticated that all known attacks are considered computationally infeasible. It is no surprise then, that the NSA considers 256-bit AES safe for storing top-secret data.
What is a little more surprising, however, is that it is not just government agencies that are benefitting from the use of such cryptosystems — you probably are as well. AES has been adopted for commercial use by well-known companies like Apple, and it would appear that law enforcement is none too happy about the development. In his recent keynote address at the DFRWS computer forensics conference in Washington, D.C., Ovie Carroll (director of the cyber-crime lab at the Computer Crime and Intellectual Property Section in the Department of Justice) lamented, “I can tell you from the Department of Justice perspective, if that drive is encrypted, you’re done… When conducting criminal investigations, if you pull the power on a drive that is whole-disk encrypted you have lost any chance of recovering that data.”
As tempting as it might be to conclude that your data is safe and sound, every day new attacks prove otherwise. After all, despite the strength of these encryption systems, all an attack ultimately usually requires is an ID and/or password — information that can be readily obtained by private individuals through social engineering or carelessness on the part of the user. If a few teenagers can remotely compromise a person’s Apple, Google, Twitter, and Amazon accounts in the span of a few hours with nothing more than an Internet connection and a phone, it is hard to believe that the Department of Justice, with all of the powers and resources at its disposal, is so helpless.
In addition to its discreet but certainly formidable array of hacking tools, the DOJ has repeatedly claimed, with some success, the right to compel defendants to disclose passwords and decrypt files. Moreover, the sophistication of hacking techniques has gone beyond software vulnerabilities; hardware is now just as susceptible to malicious injections. It may be all for the best if criminals are under the impression that their data is protected from prying eyes, but the rest of us shouldn’t be so naïve. It is only by recognizing the vulnerability of our data that we can go about taking the appropriate steps to protect it and call into question the authority of government agencies (which would like us to believe our data is beyond their reach) to access it.
A friend of mine said, “This reminds me of my days in the online video game space. The king of the hill at the time, Sony Online Entertainment (specifically their President John Smedley), would almost like clockwork do an interview/host an event a few weeks before a new launch of their MMO EverQuest, to tell the world how it was the worst business to be in and that it was almost technically impossible to do.
“The correlation is as follows: It wasn’t a horrible business, they made bank, and it wasn’t near technically impossible. In fact, it was only getting /a lot/ easier and less costly. Smedley was doing everything he could to discourage folks entering the market.”
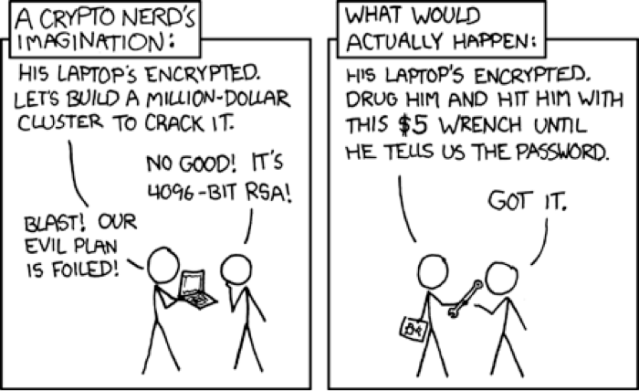
The Department of Justice is stating that encrypting a drive means you’re safe. They are stating that an encrypted drive recovered after power has been cut is impossible to access. This is just not true (not that we have anything against this tactic to catch real criminals).
The reason is simple: The government doesn’t need to break or crack the encryption. They are the government. They can compel you in many other ways to just turn over your access codes or just obtain them through social engineering.
This has prompted some to move their entire operations offshore to try and avoid the prying hands of local government agencies. However, Engin Akyol, CTO of Distil.it (ff Venture Capital portfolio company which operates a global network of servers) observed, “The problem with this approach is that the global reach of U.S. influence is pretty extensive, and virtually no developed nation is going to risk the political fallout of hosting a criminal enterprise and protecting it from American authorities or Interpol.”
Encrypting your data is akin to keeping a self-destructing safe. While your most crucial documents may be destroyed in lieu of falling into the hands of governments and other people, your interactions with other human beings will be harder to erase or destroy. When the FBI took down mob assets in the second half of the 20th century, it wasn’t because they cracked safes containing incriminating documents. It was through long-term investigations and surveillance and legislative advancements.
The same tactics are starting to prove just as successful in cyberspace.
Thanks to Rami Essaid (CEO, Distil.it) for input and Matt Joyce (Dartmouth Computer Science student) for help researching this.
[Comic via xkcd]